How to install evalhook on Centos (WHM)
This time I want to share my experience. Okay, about 2 weeks ago, late / evening ... on Facebook there is a share of the ' nuyul ' safelink script. And the script is copied, yeah, as usual, if people share the script about the ' quiz', they will definitely be hacked, I don't know what the goal is. After I searched it turned out that the script was copied on ud64.com , then I tried deobfuscate manually, by changing the eval function to print_r . Until finally I managed to get the original script, that's about 5 minutes, because the length of the string is almost 800-1000 lines, forget about the time. So we just go to the point.
In this experiment I used the additional php extension, evalhook. You have to install Evalhook first and the install tutorial is on the page https://github.com/unreturned/evalhook.
If it's already installed, then prepare the script first, which has been copied on ud64.com.
Then type php -d extension=evalhook.so namafile.php enter
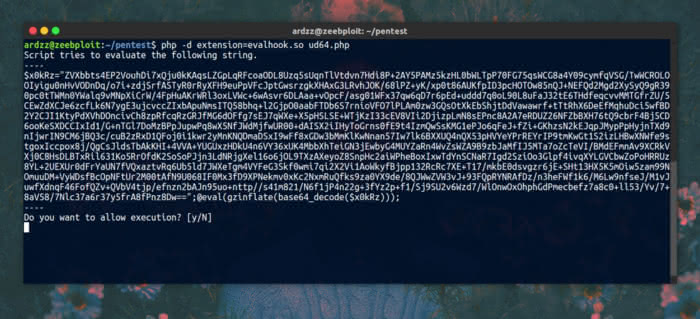
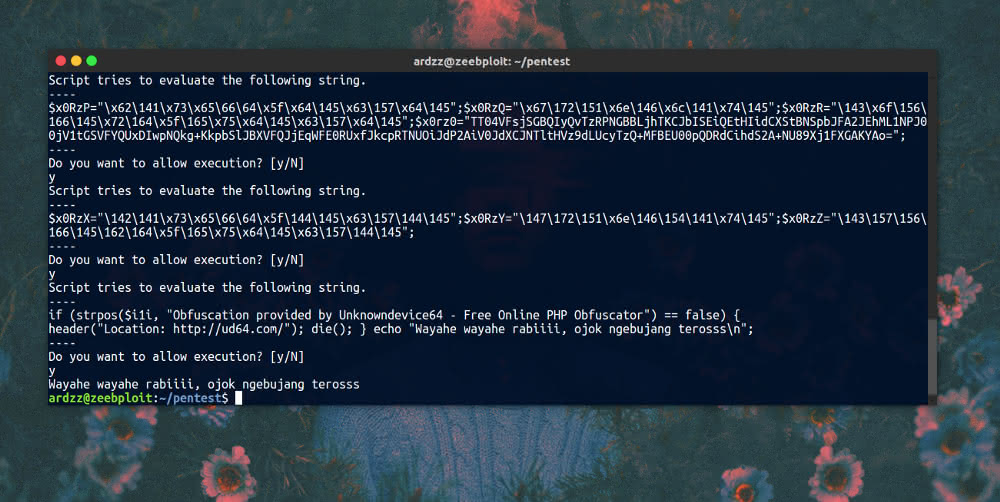
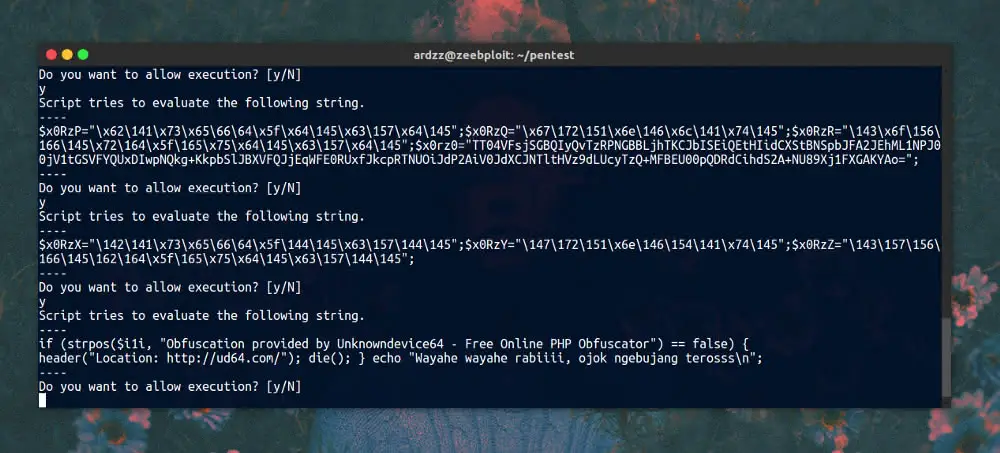
Do you want to allow execution? just answer y until there is a piece of script
if (strpos ($ i1i, "Obfuscation provided by Unknowndevice64 - Free Online PHP Obfuscator") == false) {
header ("Location: http://ud64.com/ "); die (); }
If you have seen the code snippet above, it means the script has been deleted.