Some time ago we dedicated an article to
how to verify the integrity of files in Windows
, something that is relatively simple in this operating system. My problem was that once I reached the Linux terminal, I lost this functionality because I didn't know the different tools. This has motivated me to write this little tutorial where I will teach you to
verify the integrity of files from the Linux terminal
.

Specifically I will use the terminal in a Linux Ubuntu 16.04 operating system. I will use the tools included in the operating system, without installing any additional software. I have encountered occasions when I would like to make a quick verification not only of the integrity of the file, but
with this method, we can also check if two files are the same
.
What is the process of verifying the integrity of a file?
When we talk about verifying the integrity of a file, we are talking about verifying that the data in a copy are exactly the same as in the original file.
This verification allows us to
avoid data corruption problems
and ensure that the data has been stored correctly.
To perform this verification, there are different algorithms or hash functions that allow us to obtain the so-called
checksum
(
checksum
)
. Many data transfer protocols,
backup
systems and even
file compressors
make use of these checksums.
Practical example to better understand the verification process.
To better understand the whole process, we will propose a very simple example. Imagine that we have a very important file called
documento.bin
and I want to copy it to a USB flash drive with the name
documento_copia.bin
, making sure that the data has not been altered during the process.
All I have to do is get the checksum of the original file
(document.bin)
and the checksum of the copied file
(document_copy.bin)
to compare them.
If both checksum are the same, the file is an exact copy of the original and the data maintains its integrity.
If, on the contrary, both checksum are different, the data has been damaged in the process.
Tools to verify the integrity of files from the Linux terminal.
In the GNU / Linux world there are many tools and commands to verify the integrity of the files, even package managers such as APT make use of these. In our case, we will use the
most common tools that we can use from the console
.
cksum
Cksum is the standard tool to calculate the 32-bit CRC checksum.
There are different implementations of the CRC32 algorithm
(Cyclic Redundancy Code)
, but the
cksum
tool specifically uses the implementation of the Ethernet network standard.
If what we want to calculate is the 16-bit CRC
(CRC16)
, the tool we should use is
sum
, but its use is not recommended if we can use
cksum
.
From a security point of view,
CRC32 is considered an insecure hash function
, but to verify the integrity of files at home is more than enough. It has the advantage that it is an
algorithm with great performance and fast
.
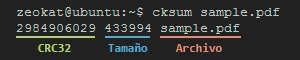
To use this tool, simply execute the following command in the console:
cksum archivo
md5sum
The md5sum tool calculates the MD5 hashes of a file or data set.
This allows us to verify the integrity of files and their use is quite widespread.
From the point of view of security,
the MD5 algorithm is not considered safe
and its use is not recommended in situations where a malicious user can modify it. Even so, to verify the integrity of files on our personal PC, it performs its function without problems.
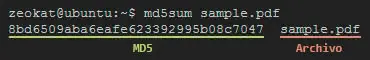
We can use this from the terminal as follows:
md5sum archivo
sha256sum.
At present it is recommended to use the SHA-256 algorithm to calculate the checksums of the files and thus be able to verify their integrity. SHA-256 is the logical replacement of the MD5 algorithm, since for the moment no vulnerabilities have been discovered.
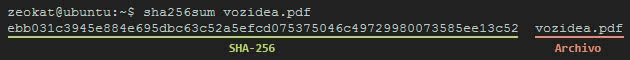
To
calculate the SHA-256 checksum of a file from the Linux terminal
we execute the command:
sha256sum archivo
There are other variants of the SHA algorithm that we can use using the tools:
shasum
,
sha1sum
,
sha224sum
,
sha384sum
and
sha512sum
.
Checksum verification files with extension: .sfv, .crc, .md5, etc.
We already know the tools to calculate checksums from the console, but in Linux there are also
tools to check lists of checksums
. This is especially useful when we have to verify several files.
Sometimes we can find files that make up checklists. These files contain a list consisting of the file name and its respective checksum.
Cksfv tool: create and verify SFV lists.
To check or create files with extension
.sfv
, in Linux we have the tool
cksfv
. In the case of Ubuntu, this tool is not installed by default, so we will have to install it with the command:
sudo apt install cksfv
.
Once the tool is installed, we can
verify .sfv files from the terminal with the command
:
cksfv -g /home/zeokat/lista.sfv
We can also
create .sfv files
with the command:
cksfv fichero1 fichero2 fichero3 > listado.sfv
Cfv tool: create and verify lists in different formats.
The cfv tool is more complete than cksfv, since it supports more file formats.
Among the supported formats are the following:
.sfv, .sfvmd5, .md5, .par, .par2, .crc, .csv, .torrent, sha1sum and md5sum
.
In Ubuntu it is not installed by default, so we will have to install it with the command:
sudo apt install cfv
.
The basic command to verify a list of files is:
cfv -f /home/zeokat/test.sfv
To create a checklist, the basic command would be:
cfv -C -flista.sfv -tsfv documento.pdf documento2.jpg
cfv -C -f[nombre de lista] -t[formato de lista] [archivos"¦]
For more information, we can always use the
cfv --h
command to see the help screen.
Within the world of package integrity verification there are many other formats and tools depending on the type of distribution. Here ends the tutorial and I hope you learned the basics to verify the integrity of files.