In versions previous to CentOS 7 we had the iptables service that referred to the Firewall. Now in CentOS 7, this service is different and is called firewalld . If we want to maintain the old way of opening a port, using iptables; we can install the iptables service in CentOS 7 and disable the firewalld that has this version by default. However, if we want to maintain the new firewalld command , we will have to open the port by executing a different command.
Open ports in CentOS7
Here are some simple steps to open a port on RedHat / CentOS 7 permanently, using the new firewalldcommand . You can always edit the file /etc/firewalld/zones/zone.conf statically and restart the daemon, but the correct way to do it is the following:
1. Open the port by specifying the appropriate zone, port number and protocol. In order for the port to survive a restart of the server, at the end of the command line you must add the " -permanent " rule :
# firewall-cmd --zone = <zone> --add-port = <port_number> / <protocol> --permanent
For example, if we want to open port 80 permanently, the command would be like this:
# firewall-cmd --zone = public --add-port = 80 / tcp --permanent
2. For the changes to take effect, you must restart the firewall with this command:
# firewall-cmd --reload
Check open ports with Nmap in CentOS7
3.- One of the tools that allows us to consult the ports that we have open is Nmap. To do this, we installed Nmap with the following command:
# yum install nmap
See the local open ports, execute:4.- To see the ports that we have open with nmap, we can see them in two ways: "See open ports in local", that even if we have them open they do not necessarily go to the internet or "see the open ports in the server" that here if we can see the ones that go to the internet through the IP of our server. Therefore, we will apply a ditinto command for each of them according to what we need to know when checking them:
# nmap localhost
The result is as follows:
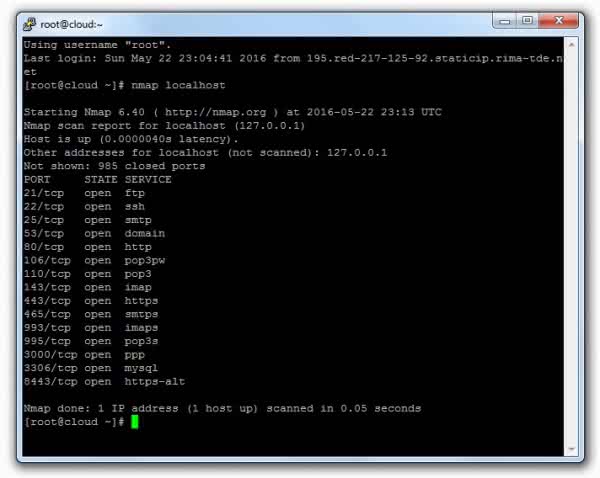
See the open ports on the internet, execute:
# nmap 108.61.155.194
The result is as follows:
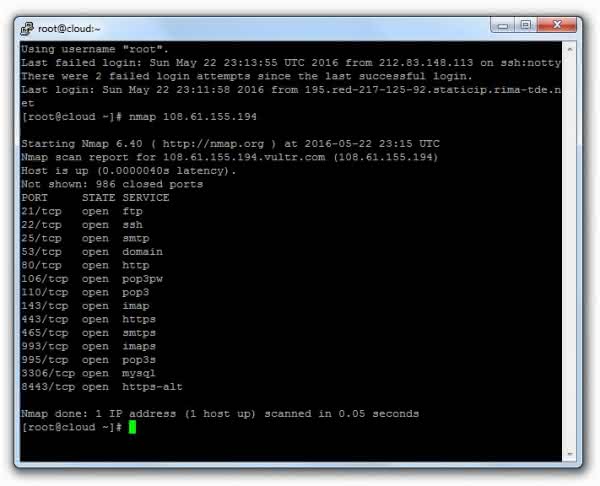
Use and examples of Nmap
NMAP has many combinations and parameters but I will show only a few examples:
Scan all ports of a host with extended information (verbose):
# nmap -v 192.168.1.100
Scan a single port on a host:
# nmap -p 80 192.168.1.100
Search open TCP ports on a machine:
# nmap -sT 192.168.1.100
Search open UDP ports on a machine:
# nmap -sU 192.168.1.100
Scanning of a host's protocols (in addition to TCP, UDP, shows availability of ICMP, IGMP ...):
# nmap -sO 192.168.1.100
Scan a range of ports:
# nmap -p 80-200 192.168.1.100
Scan a range of ports and specific ports, both TCP and UDP:
# nmap -p U: 53,161,8888, T: 1000-2000,80,25,8888,8080 192,168.1,100
These would be some examples for a basic use of Nmap. This tool is a world and it would take an entire book to take advantage of 100%. If you have more time and want to deepen the operation of Nmap, you can see many more examples and consult the reference guide on the official website of Nmap where there is extensive documentation. Until another.