When a server arrives at our hands it is not usual for the client to tell us what programs have been installed and configured, we will have to find out ourselves. Today we will focus on
identifying the MTA installed on the server
. When I say MTA installed, I mean the MTA that is active and working in the system.

Before continuing, clarify that this tutorial is aimed at Linux environments
(although some of the methods are applicable in Windows)
and we will show different methods to achieve our goal. Some of these methods require access to the system shell and others do not.
Among less experienced users it is very common to use scripts that install a
web server
automatically and even install and configure the mail server automatically. Later, if you have to resolve any issue on that server, as a first step we will have to discover the installed software. So without further ado we will see
how we can find out the MTA of the system
.
What is an MTA?
If you have come here I assume that you know what an MTA is, but to be sure I will make a small introduction. The word MTA comes from the English
«Mail Transfer Agent»
and is nothing more than a
software that allows us to configure an email server
.
An MTA implements both the sending and receiving functions, although later we can configure it to perform one or both functions.
The MTAs use the TCP port 25 by default for the SMTP protocol
(Simple Mail Transfer Protocol)
, which is the most used.
There are different programs designed to function as an MTA, but some of the best known are:
postfix, sendmail, exim, qmail, Microsoft Exchange Server, etc.
How to identify the MTA installed on a Linux server.
As we said at the beginning, we will show different methods and start with the fastest ones using the system terminal.
Searching for MTA tracks in the / etc / passwd file.
A simple way that can give us clues about the installed MTAs is to use the
cat /etc/passwd
command to read the contents of this file.
In general, the mail servers maintain their own user and their working folder is associated with the path
/var/spool/
, where the programs that need to work with queues are located, as is the case with the mail servers. We see for example the contents of the
/etc/passwd
where we can identify
Postfix
as MTA:
nginx:x:111:117:nginx user,,,:/nonexistent:/bin/false
mysql:x:112:118:MySQL Server,,,:/var/lib/mysql:/bin/false
postfix:x:113:120::/var/spool/postfix:/bin/false
This method is not infallible, but it can give us clues. To be sure we can use the following methods.
Using the lsof command.
The first and easiest option is to use the
lsof
command to find out the
PID
of the process that is listening on port 25. We execute the
sudo lsof -i :25
command and it will show us something similar to:
zeo@zeohost:~$ sudo lsof -i :25
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
master 1452 root 12u IPv4 17410 0t0 TCP localhost:smtp (LISTEN)
master 1452 root 13u IPv6 17411 0t0 TCP localhost:smtp (LISTEN)
Sometimes, in the
COMMAND
column we already see the name of the MTA, but in this case it is not so, so we will have to do a second check with the
PID
.
We see that the PID in our example is 1452. Now we execute the
ps p 1452
command and we will see something like:
zeo@zeohost:~$ ps p 1452
PID TTY STAT TIME COMMAND
1452 ? Ss 0:02 /usr/lib/postfix/sbin/master
If we pay a little attention, we can see that the MTA in operation in the system is Postfix.
Using telnet to connect to the host through port 25.
A second option is to use telnet and connect to the host using port 25. For this we execute the
telnet localhost 25
command and when the connection is established, a message usually appears showing the name of the MTA as we can see below:
zeo@zeohost:~$ telnet localhost 25
Trying ::1...
Connected to localhost.
Escape character is '^]'.
220 vozidea.com ESMTP Postfix (Debian)
quit
221 2.0.0 Bye
Connection closed by foreign host.
To close the connection, write the
quit
order and press
Entrar
.
Identify the mail server used by analyzing the email headers.
Another way to find out the mail server you are using is to analyze the email headers.
For this, we simply need a Gmail email account and have the ability to receive an email from our server in this Gmail account.
To send this email we can use the following options:
-
Use the registration or password recovery system of any script that we have installed on the server
(WordPress, phpBB, Drupal, etc)
.
-
Send the email from the console with the command:
echo "Hola, soy el cuerpo del correo" | mail -s "Email de prueba" [email protected]
echo "Hola, soy el cuerpo del correo" | mail -s "Email de prueba" [email protected]
-
We could create a small script in PHP to send a test email.
Once we have received the email in our Gmail account, we open it and access the
"Show original"
option, accessible from the drop-down menu next to the time the email was received.
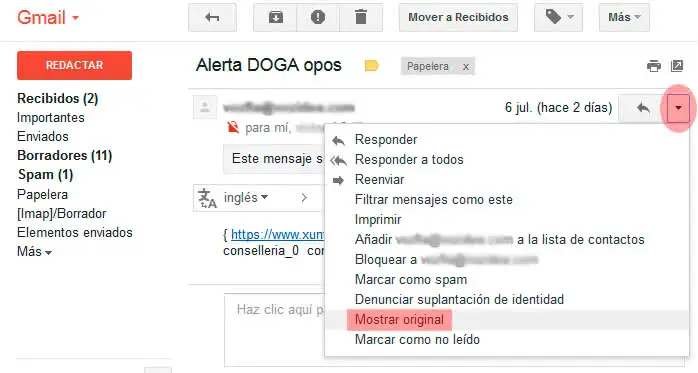
Now
in the original message we can examine the headers
, but the one that interests us is the one that begins with
Received: by ...
since there we can identify the MTA as seen in the following example:
Received: by ns540796.ip-144-211-11.net (Postfix, from userid 10004) id D073A431BC; Sat, 8 Jul 2017 06:58:08 -0400 (EDT)
Surely there are more methods to identify the installed MTA, but with the methods shown throughout this tutorial it should be enough. If you know any other interesting method, do not hesitate to comment.