The other day I was writing an article that showed
how to get information from the network card in Windows operating systems
, something I don't usually do very often, since I generally manage Linux-based systems. This brought me the idea of "‹"‹writing an article about the
analysis of network connections in Linux
, but knowing that
netstat
will soon be replaced by
ss
, I have decided to directly use the
ss
command.

What is that about the net-tools and the iproute2 suite?
For those who are somewhat lost, the
netstat
command belongs to the net-tools network analysis tool suite, which was born in 2001. This suite was designed to work with older kernels, so
in many Linux distributions it is already has replaced net-tools with the new iproute2 suite
.
The iproute2 suite offers certain advantages over net-tools
, in which we will not go deeper with technical details, but if we clarify that they offer
better performance
, they have a more intuitive use and their development is active.
As we are still in a phase of transition to iproute2, there are many distributions that include both, although in others net-tools have already been removed and the package marked as obsolete.
To make a simple tutorial, we will only focus on the use of the
ss
command, which is part of the iproute2 suite. This command is used to
analyze network connections
, since it replaces the old
netstat
command.
Analyzing network connections in Linux with the ss command.
The
ss
command refers to
"Socket Statuts"
and is used to
obtain information about network connections, open ports and other statistics
.
The most basic use is
ss -a
, which will display all the information of all connections on the screen. From here we can add different modifiers to obtain the information we are looking for. I recommend reading the help with the
man ss
command or consulting the different modifiers with the
ss -h
command.
Examples of using the ss command to obtain connection information.
First, if what we want is to
list the connections depending on whether they use the TCP or UDP protocol
, we will have to use the following commands:
-
List TCP connections:
ss -ta
-
List UDP protocol connections:
ss -ua
We can also
filter the list based on whether they use the IPv4 or IPv6 internet protocol
:
-
Connections under IPv4:
ss -4
-
Connections under IPv6:
ss -6
Now we are going to refine a little more and
list only the connections whose status is
"LISTEN"
, that is, they remain listening. The most basic command in this case would be
ss -l
, which shows all the listening sockets, but we can combine it with other options to:
-
List TCP sockets to listen:
ss -tl
or we can also use the
ss -t state listening
command
-
List UDP sockets to listen:
ss -ul
or the
ss -u state listening
command
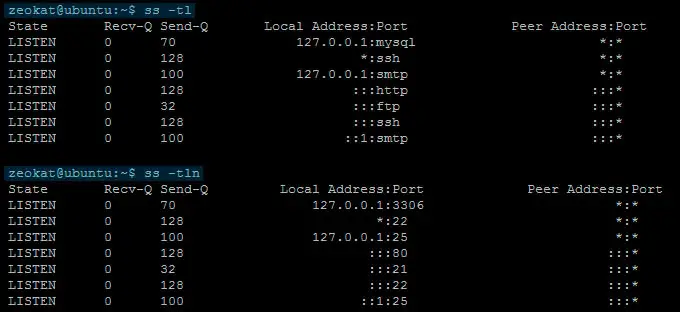
Sometimes I like to add the
-n
option to the previous commands so that the names of the services are not resolved. You can see the difference in the following image.
Examples of how to filter connections depending on the protocol (HTTP, FTP, SMTP or SSH) or depending on the port.
Now I am going to show you some examples to list the connections but filtering according to some of the most used protocols:
-
To list HTTP traffic
:
ss state established '( dport = :http or sport = :http )'
-
View active FTP protocol connections
:
ss state established '( dport = :ftp or sport = :ftp )'
-
List active connections SMTP
:
ss state established '( dport= :smtp or sport= :smtp )'
-
See if there are SSH connections
:
ss state established '( dport = :ssh or sport = :ssh )'
Within this section I must add the possibility to
list the connections depending on the port
, for example we can use
ss -nt dst :80
to list the connections whose destination port is port 80. When what we want to list are the connections whose port The source is 80, we will use the
ss -nt src :80
command.
We can
monitor several ports simultaneously
, for example with the
ss -nt '( dst :443 or dst :80 )'
command.
Finally, add a little trick that involves using
ss
conjunction with the
watch
command, to monitor connections in real time. We could use for example:
watch ss -ta
I hope this little tutorial has helped you and serves as a starting point to solve a connection problem, monitor your servers connections, etc.