One of the most used protocols at the security level to establish connections in UNIX environments is the SSH (Secure Shell) protocol which offers us a series of functionalities and special features to protect the data and connections made..
SSH is a protocol that has been developed focusing on the security of communications between two systems through the client / server model and thanks to which users are allowed to connect to a host remotely.
One of the main features of SSH is that it encrypts the connection session, which prevents any user from obtaining unencrypted passwords.
Types of protection
When using the SSH protocol we will have the following types of protection:
- Once the initial connection is established, the client can verify that it is connecting to the same server to which it was previously connected
- The client sends the authentication information to the server through 128-bit encryption
- All data sent and received during the session are transferred by means of 128-bit encryption, which makes it difficult for them to be decrypted and read
- The client has the opportunity to forward X11 applications from the server., This is a technique called X11 forwarding which provides a secure means to use graphic applications over a local or external network
Now, in Linux operating systems we find the SSH configuration file in the path / etc / ssh / ssh_config and thanks to this file it will be possible to perform all security measures for SSH connections..
In the case of macOS systems, this file is in the path / private / etc / ssh / ssh_config and it has a symbolic link to / etc / ssh / ssh_config for compatibility purposes.
When editing this file we must keep in mind the following..
- Empty lines and lines that start with '#' are comments
- Each line begins with a keyword, followed by argument (s)
- The configuration options can be separated by blanks or optional blanks and a = sign
- Arguments can be enclosed in double quotes (") to specify arguments that contain spaces
1. How to edit the ssh_config Linux file
To edit this file in order to establish own values, we must execute the following with some editor:
sudo nano / etc / ssh / ssh_config
We will see the following:
The ssh_config file is organized by hosts and there each host contains specific settings for that particular host, there we can use wildcards such as * to match several host names with a single declaration.
Some of the parameters that we can use in this file are:
Host
Restrict statements that are only for hosts that match one of the patterns given after the keyword.
Match
Restrict statements so that they only apply to hosts that match the specified criteria
AddressFamily
Specify which family of addresses to use when connecting, the valid arguments are: any, inet, inet6.
BatchMode
With this value the password query will be disabled, thus avoiding accidental blocking in a password request
BindAddress
Specifies the use of the address specified on the local machine as the source address of the connection.
ChallengeResponseAuthentication
Lets you indicate if challenge-response authentication is to be used. This is primarily an inherited method and has been replaced by KbdInteractiveAuthentication
CheckHostIP
Tell ssh to additionally check the host IP address in the known_hosts file.
Cipher
Refers to the encryption that will be used to encrypt the session in protocol version 1.
Ciphers
Specify the encryption allowed for version 2 of the protocol in order of preference.
Next, we will see some practical tips to improve the security of SSH connections to Linux and thus obtain the best access features.
2. How to block SSH Linux files
The first step before editing the file, is to make sure that both the ssh_config file and the sshd_config file have the owner and user configured as root, this because they are the Linux super user and nobody better than this is the owner.
To do this we execute the following:
sudo chown root: root / etc / ssh / sshd_config sudo chmod og-rwx / etc / ssh / sshd_config
3. How to confirm the SSH version 2 Linux protocol
Version 2 of SSH has an improved key exchange algorithm which is not vulnerable to the security hole in version 1 thus improving the overall security of the connections, so it is ideal to confirm that the new Protocol 2 is being used in Protocol 1 place and for this we must confirm the following line in the ssh_config file:
Protocol 2
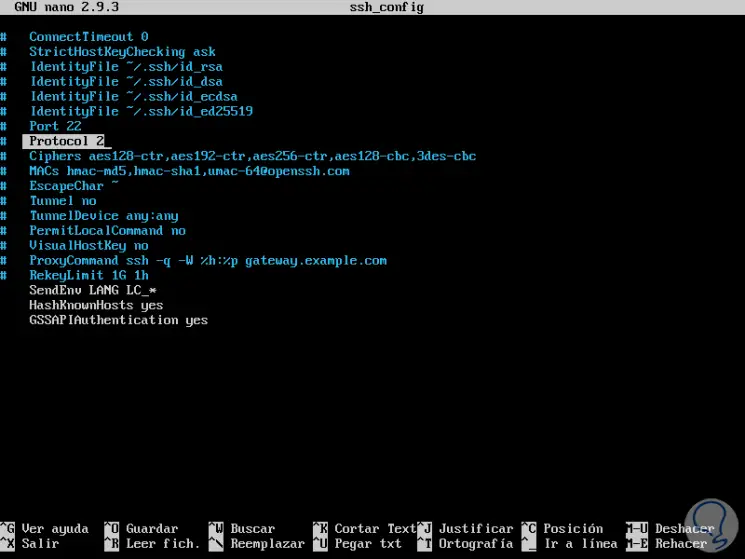
There we can also configure the protocol implicitly through Ciphers, which will automatically set Protocol to 2 to use modern Ciphers, for this we validate the following line just below the Protocol line:
Ciphers aes128-ctr, aes192-ctr, aes256-ctr
4. How to disable empty SSH Linux passwords
It is important to validate that each SSH account must use a password when logging in by blocking empty passwords which would allow simple access causing security risks in the system, to validate this we will use the following line or, if it does not exist, we add it by putting the symbol first #:
PermitEmptyPasswords no
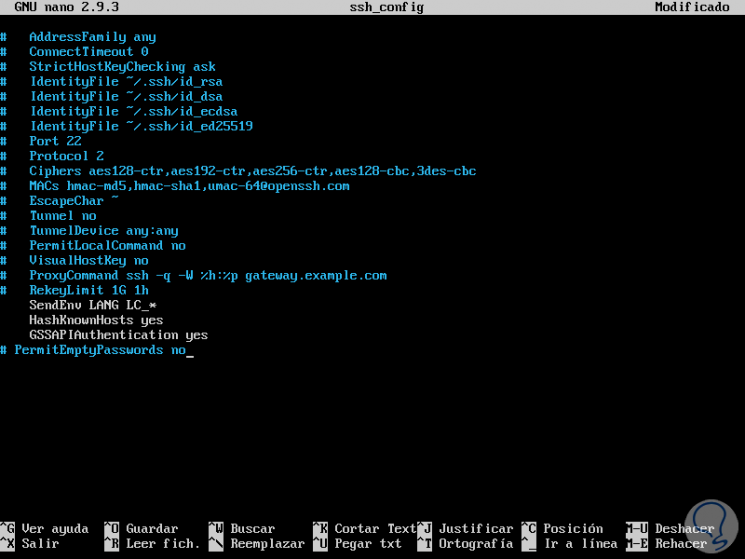
5. How to disable SSH Linux root login
By avoiding the login of the root user it will be possible to block specific accounts and not allow the use of these in the whole system, the options for PermitRootLogin include "yes", "without-password", "forced-commands-only" or " do not". The default value is "yes." To completely stop the root login we will use the following line:
PermitRootLogin no
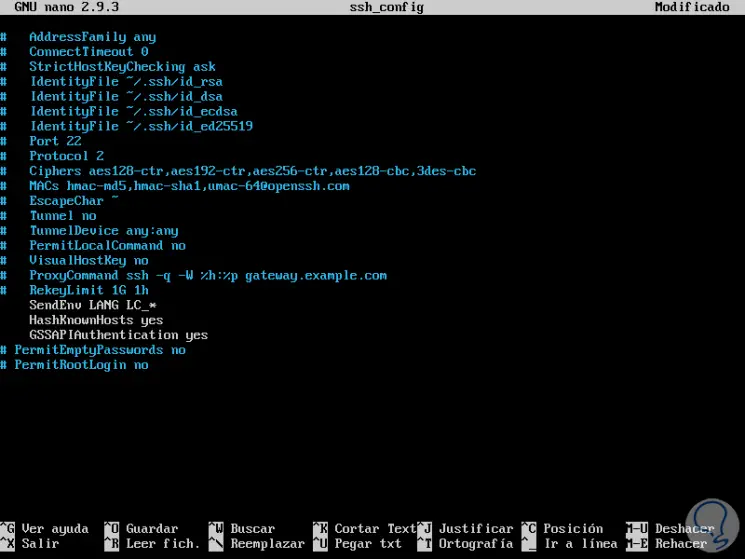
6 . How to set up a new SSH Linux port
By default the port assigned for SSH is 22, so attackers know with certainty through which port they will access to carry out their attacks so that a good security method is to change this port by default and only indicate to authorized users The new port
For this, we must locate the Port line and add the following syntax:
Port XXXXX
7. How to restrict SSH Linux access
In case the access to the SSH server is composed of several users, it is possible to apply certain restrictions by creating groups where these users are included, this is possible by adding keywords such as:
AllowUsers (Allows user access) AllowGroups (Allow group access) DenyUsers (Restricts user access) DenyGroups (Restricts group access)
For example, we can execute the following in the configuration file:
AllowUsers TechnoWikis tests DenyGroups test
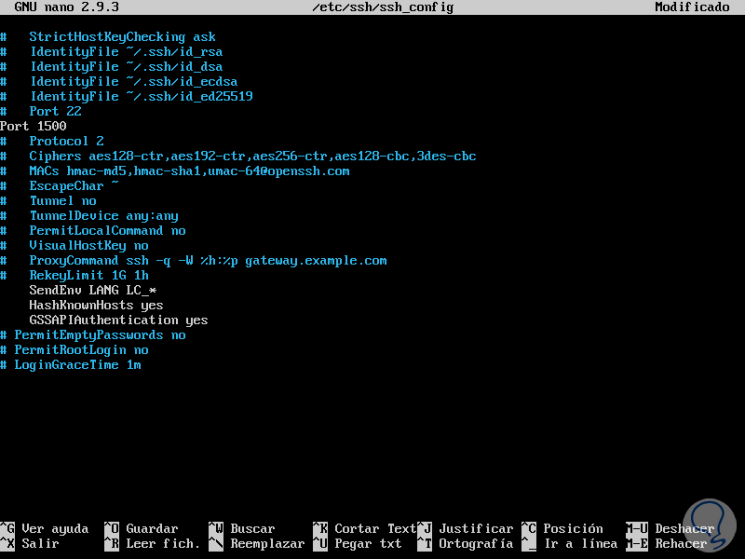
8. How to update the grace time of SSH Linux
By default, the amount of time that a user can remain inactive without logging in is two minutes, this in order to help prevent unauthorized connections to the system, this time we can edit it on the LoginGraceTime line by increasing or decreasing this weather:
LoginGraceTime 1m
9. How to create an SSH Linux alias
Within the SSH configurations it is possible to specify an alias, these allow to connect to a specific server through a port and defined users, for example, we can add the following:
Host dev HostName dev.solvetic.com Port 3333 User TechnoWikis
In this specific case we must access as follows:
ssh [email protected] -p 3333
10 . SSH Linux Secure Key Authentication
ssh will be much more secure and useful when used with public / private key pairs for authentication issues, instead of using passwords. The ssh_config file can declare a specific key for a specific host using the IdentityFile key, in this case we would enter the following:
Host dev HostName dev.solvetic.com Port 3333 User TechnoWikis IdentityFile ~ / .ssh / dev.solvetic.key
For this case the connection would be as follows:
ssh -i ~ / .ssh / dev.solvetic.key [email protected] -p 3333
Some additional parameters are:
Compression
There we can use values ​​such as yes or no to enable compression deactivation for a host.
LogLevel (Record Level)
It allows defining the level of detail in the records for the ssh client, the options are QUIET, FATAL, ERROR, INFO, VERBOSE, DEBUG1, DEBUG2 and DEBUG3.
StrictHostKeyChecking
Set a preference to add hosts to the known_hosts file.
Thus, we have different options to improve security and SSH connectivity in Linux.