When using multiple operating systems, it is ideal to always have tools that allow us to maintain centralized and direct control over it. One of the most delicate issues is unquestionably the security and integrity of the files since this guarantees us the availability and reliability of this..
Today TechnoWikis will talk about a practical tool called AIDE through which it will be possible to check the integrity of a file or directory in the various Linux distributions and thus be sure of the complete reliability of the selected file .
What is AIDE?
AIDE ((Advanced Intrusion Detection Environment) is a file and directory integrity checker in Linux environments allowing us as administrators to maintain specific control over them.
Its operation consists in the creation of a database designed from the rules of regular expressions that are available in the configuration files. Once this database is initialized, it can be used to verify the integrity of the required files.
AIDE file attributes
AIDE is responsible for building the database of the files specified in aide.conf, which is the AIDE configuration file. The AIDE database stores several file attributes, within which we have:
- number of links and link name.
Likewise, AIDE creates a cryptographic checksum or hash of each file using one or a combination of the following message summary algorithms: sha1, sha256, sha512, md5, rmd160, tiger, haval, crc32 and also, acl attributes, xattr, selinux and e2fsattrs can be used when explicitly enabled during compile time..
AIDE has several message summary algorithms which are used to verify the integrity of the file. All the usual file attributes can also be checked for inconsistencies within it. AIDE is able to read databases from older or newer versions.
AIDE features
When using this tool we have the following characteristics:
- Algorithms compatible with message summary such as: md5, sha1, rmd160, tigger, crc32, sha256, sha512, whirlpool (additionally with libmhash: gost, haval, crc32b)
- Supported file attributes: File type, Permissions, Inode, Uid, Gid, Link name, Size, Block number, Number of links, Mtime, Ctime and Atime
- It has support for Posix ACL, SELinux, XAttrs and extended file system attributes if the support is compiled into plain text and database configuration files to simplify
- It has support for regular expressions to selectively include or exclude files and directories in order to be monitored
It is capable of compressing the gzip database if zlib support is compiled in a separate static binary for client / server monitoring configurations.
AIDE is included in the following UNIX distributions
It is important to clarify that AIDE cannot provide absolute security over the change in a file, since like any other system file, the AIDE database and / or binaries can also be altered using the appropriate tools..
1. Installing AIDE on Linux
AIDE is available in official repositories for the most popular Linux distributions, for this we can install it using a package manager according to the distro selected as follows:
apt install aide (Debian / Ubuntu) yum install aide CRHEL / CentOS) dnf install aide (Fedora) zypper install aide (OpenSUSE) emerge aide (Gentoo)
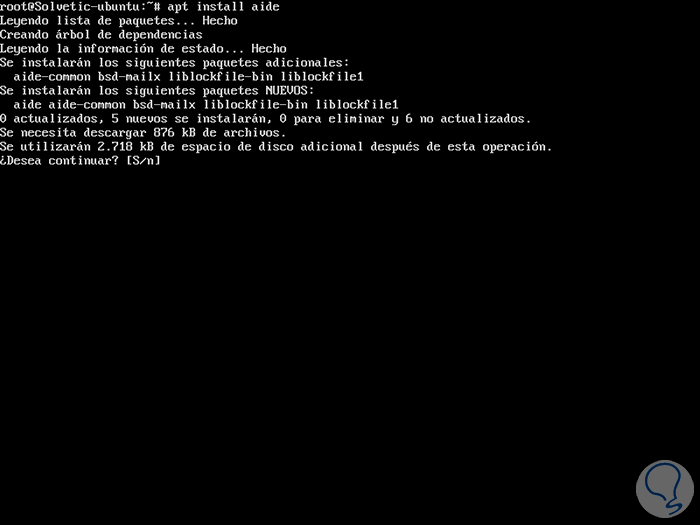
In this case we use Ubuntu. There we enter the letter S to accept the download and installation of AIDE. Once installed we will see the following:
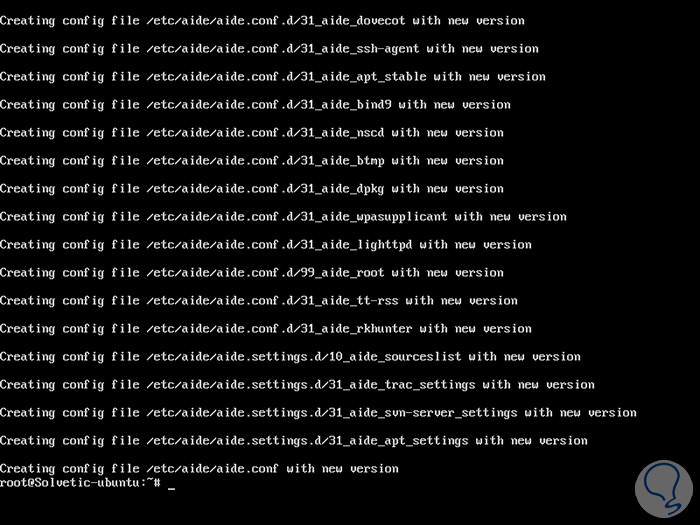
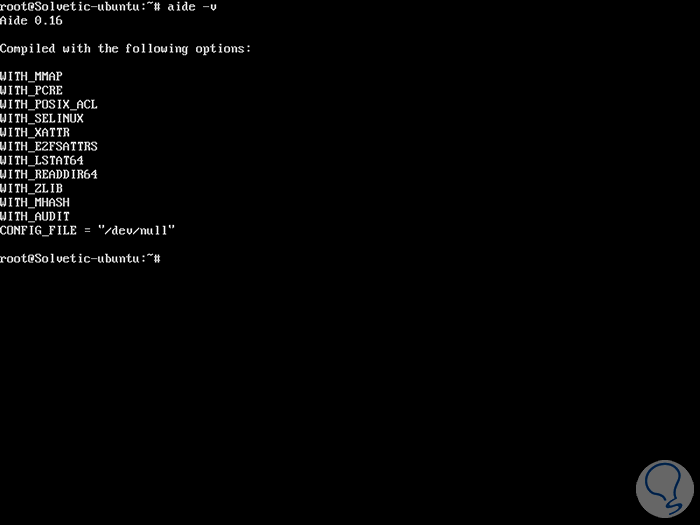
As we can see, the main configuration file is /etc/aide/aide.conf. To visualize the installed version, as well as the compilation time parameters, we can execute the following:
aide -v
2. Access to the AIDE Linux configuration file
We can access the AIDE configuration file by executing the following line with the desired editor:
nano /etc/aide/aide.conf
We will see the following:
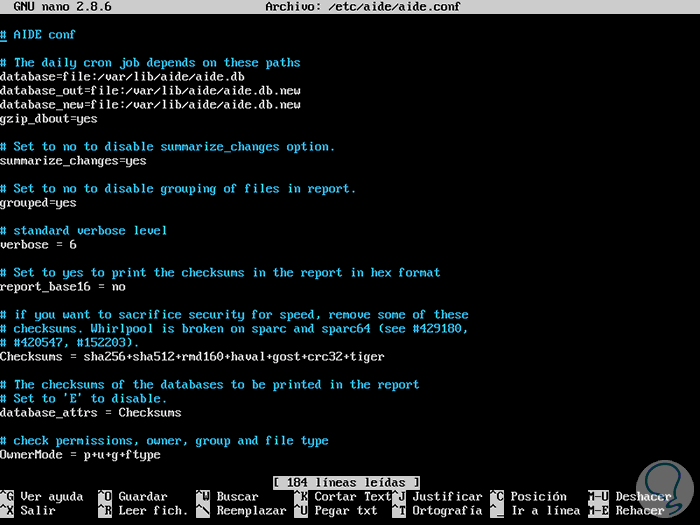
In this file we find directives that define the location of the database, the location of the report, the default rules, the directories or files that will be included in the database and many more.
3. How to manage and understand the rules of AIDE
AIDE manages rules such as:
p
Permissions - Permissions
selinux
Selinux security context
xattrs
Displays the extended attributes of a file
From these rules it will be possible to create custom rules in the AIDE configuration file. For example, we can create the following rule:
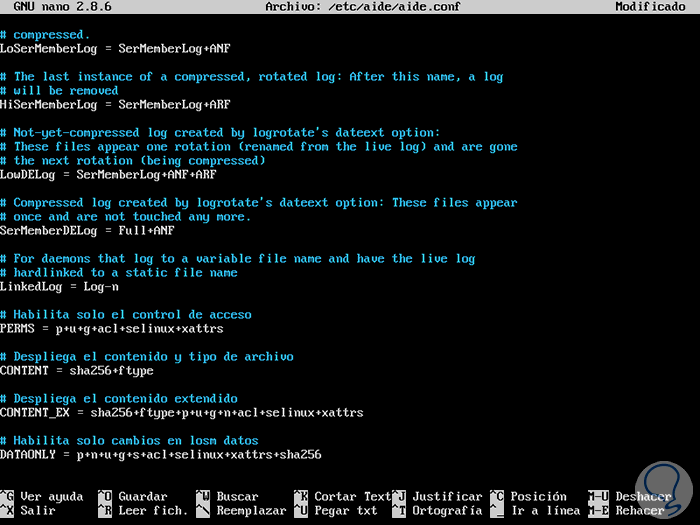
PERMS = p + u + g + acl + selinux + xattrs
In this case the PERMS rule is implemented for access control, which will detect any change in the file or directories according to file or directory permissions, user, group, access control permissions, file attributes and more.
Another rule that we can implement is one that only verifies the content of the file and the type of file selected, for example:
CONTENT = sha256 + ftype
If we want to verify the extended content, the file type and the access we can create a rule like:
CONTENT_EX = sha256 + ftype + p + u + g + n + acl + selinux + xattrs
A rule that helps us detect changes in the directory only at the data level is:
DATAONLY = p + n + u + g + s + acl + selinux + xattrs + sha256
These rules must be added at the bottom of the AIDE configuration file:
We save the changes using the Ctrl + O keys and exit using Ctrl + X.
4. How to define rules for viewing AIDE files and directories
With AIDE it will also be possible to create rules for certain files or directories to analyze. For this we access again the path /etc/aide/aide.conf and we can create the following rules:
/root/\..* PERMS (This rule verifies permissions in the root directory) / root / CONTENT_EX (This rule verifies all root files for any changes) / etc / DATAONLY (This rule allows us to detect any change in the / etc directory)
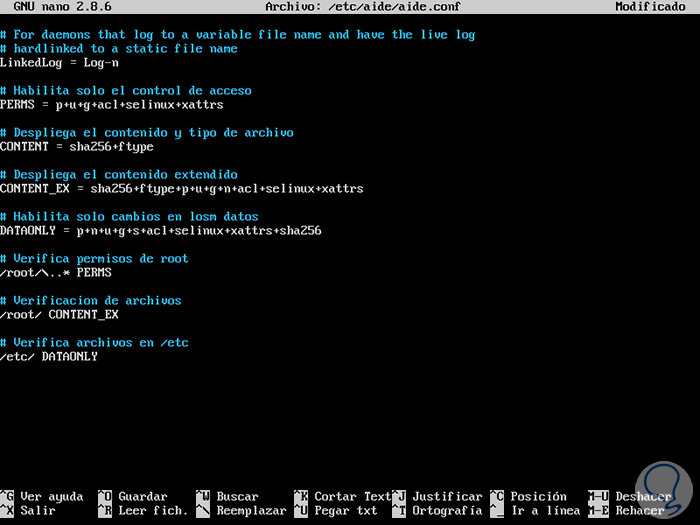
We can save the changes in the AIDE configuration file.
5. How to use AIDE to verify files and directory integrity in Linux
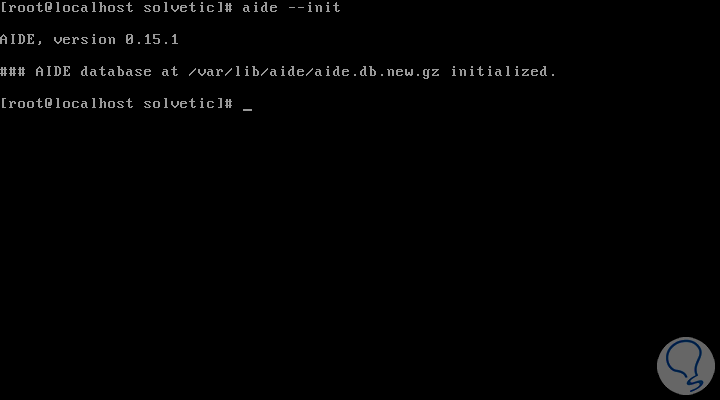
Once the rules to be used with AIDE have been defined, the next step will be to build the database against the checks that will be made using the --init parameter.
With the following command a database will be created that contains all the files that we define in the AIDE configuration file:
Aide --init
Once this is done, proceed to change the name of the database to /var/lib/aide/aide.db.gz before continuing, for this we can use the following command:
mv /var/lib/aide/aide.db.new /var/lib/aide/aide.db.gz
It is recommended to move this database to a secure location but we must be sure to update the configuration file so that it can be read from there.
Next, we must compile a new Aide configuration file. We execute the following command:
update-aide.conf
Now we will copy this new file to the / etc / aide directory:
cp /var/lib/aide/aide.conf.autogenerated /etc/aide/aide.conf
After the database is created, we can verify the integrity of the files and directories using the –check flag:
aide --check
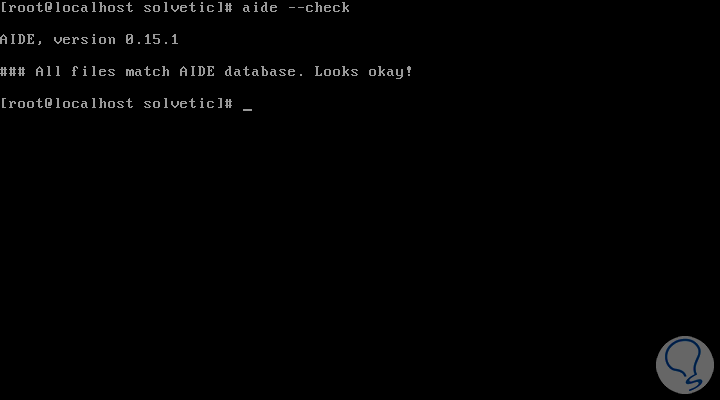
6. How to evaluate AIDE
To test the operation of AIDE we will execute the following lines:
mkdir / root / aide-test touch / root / aide-test / testsolvetic touch / root / aide-test / testsolvetic1
With them we are creating a new directory and files in the system. Subsequently we execute the following line for validation and verification:
Aide –check
The result will be as follows:
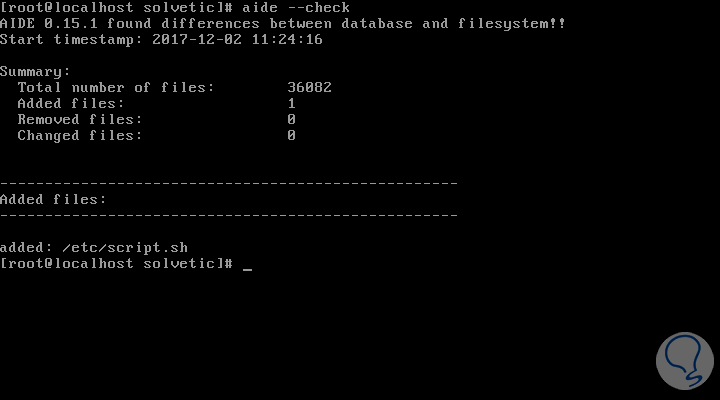
There we can see that a difference is found in the file and indicates what type of action was, addition, deletion or change.
In this way, AIDE is a useful tool to determine in real time the changes that have occurred in the system.