Within the administration tasks there is a security level that is fundamental for the security of the entire infrastructure and are the system ports. For this we must take into account that each application that requires connecting to the computer , either through the Internet or through the local network , will need some connection ports for this purpose, these ports are called listening ports, and this type of Connections can have two senses that are incoming and outgoing..
The status of a port can be open, filtered, closed or unfiltered, but we must pay close attention to the open ports since certain security policies of the organization can be violated through these ports.
TechnoWikis will explain some ways on how we can see the ports currently open in Linux and thus determine whether or not administrative actions are taken..
1. How to validate ports on Linux using netstat
The netstat (network statistics) command has been developed in order to display a list of all active connections of a device including both incoming and outgoing.
The basic way to run netstat on Linux is with the following line:
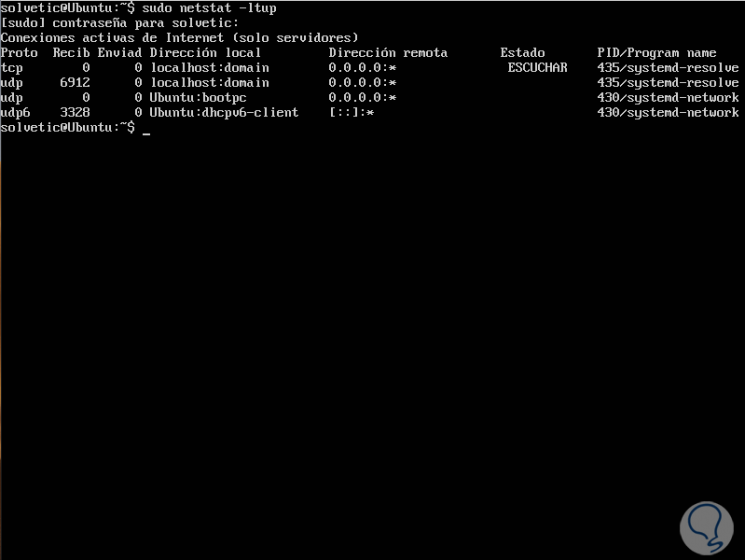
sudo netstat -ltup
The parameters used are:
- The -l value tells netstat to print all listener connectors.
- The -t value displays all TCP connections.
- With the value -u we will see all UDP connections.
- With -p, printing of the application or program name listening on the port is enabled.
The result will be as follows:
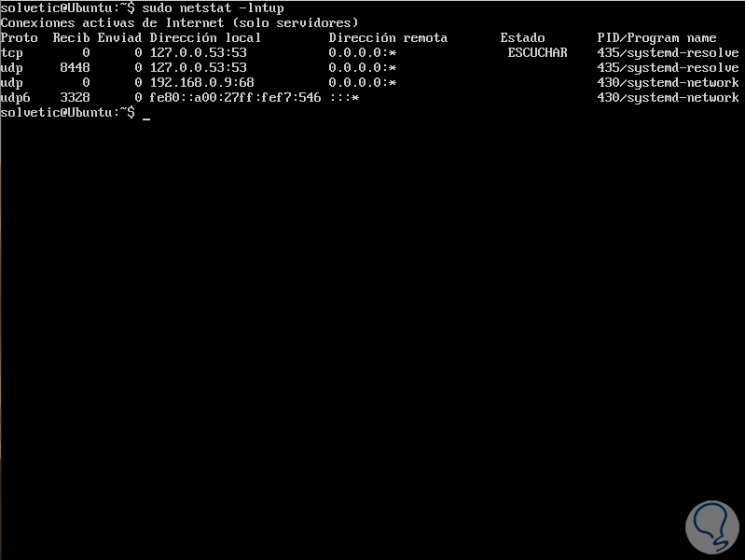
If we want to print numerical values ​​instead of service names, it will be necessary to add parameter n:
sudo netstat -lntup
We will see the following:
With netstat it will be possible to use the grep command to determine which application is listening through a particular port, for example, if we want to see what ports Apache uses:
sudo netstat -lntup | grep "apache2"
But it will also be possible to specify the port to validate:
sudo netstat -lntup | grep ": 80"
Some of the additional parameters to use with netstat are:
Display all connections and ports in listening mode
Deploys the applications and executable files that are responsible for creating connections on the listening ports
Generate Ethernet statistics
Display ports and addresses in numerical format
View the identity of each process (PID) involved
Shows connections through protocols such as TCP, UDP, TCPv6, or UDPv6
Generate statistics by protocols
It is used with -b, and thus be able to see sequences of components involved in creating a connection
2. How to validate ports using the ss Linux command
The SS command is integrated in the IPROUTE2 package and is used to display the statistics of the sockets, this type of sockets can be of type TCP, UDP, PACKET, DCCP, RAW, UNIX and more.
The information we can obtain with the SS command is:
- Information about TCP and UDP sockets with much more complete details.
- Connections established by SSH, FTP, HTTP, HTTP and more.
- Connections to the X server equipment.
- Filter by status such as SYN-RECV, SYN-SENT, TIME-WAIT using addresses and ports.
- Determine what type of TCP sockets are in FIN-WAIT-1 state.
With the following command we will deploy all listening ports for TCP and UDP connections in numerical value:
sudo ss -lntu
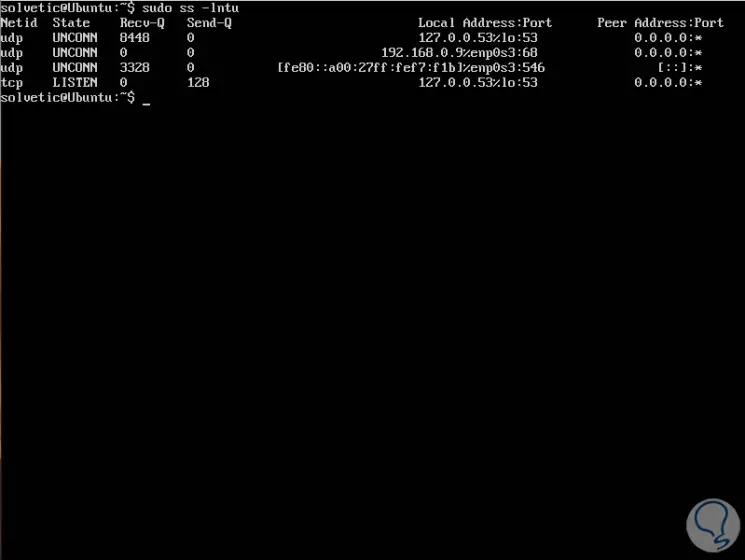
3 . How to validate ports using the Nmap Linux command
The Nmap (Network Mapper) command is one of the most complete solutions not only to validate the listening ports but also to carry out many more administration tasks at the network level since with it it is possible to execute ping sweeps, scan ports, identify services, perform IP address detection and operating system detection and more tasks.
It is one of the most practical utilities for administrators because thanks to Nmap we can explore local or external networks, perform security scans, network audits, search live hosts, operating systems, packet filters and more.
To install Nmap we must execute one of the following commands:
sudo apt install nmap (Debian / Ubuntu) sudo yum install nmap (CentOS / RHEL) sudo dnf install nmap (Fedora)
After this, to scan all open or listening ports on Linux, we will execute the following command:
sudo nmap -n -PN -sT -sU -p- localhost
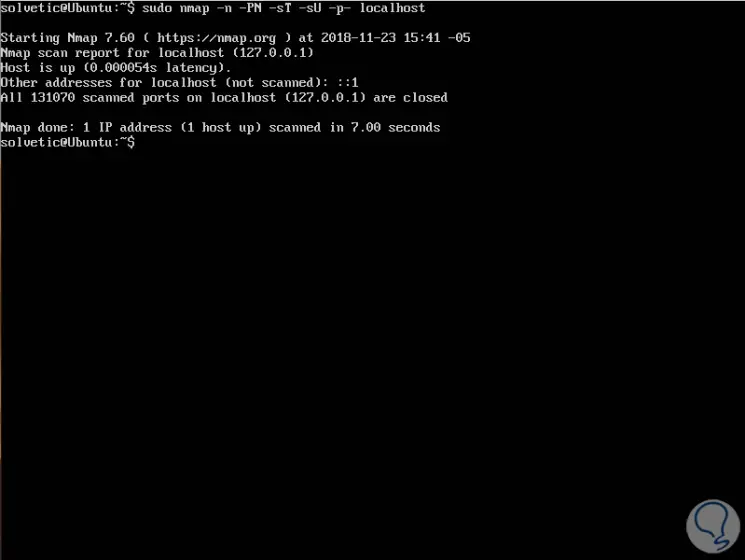
Some of the parameters to use with Nmap are:
Run a serious scan with a span of 300 seconds between scans
Run a serial scan with a 15 second span between scans
Perform a serial scan with a 4 second span between scans
4. How to validate ports using the Lsof Linux command
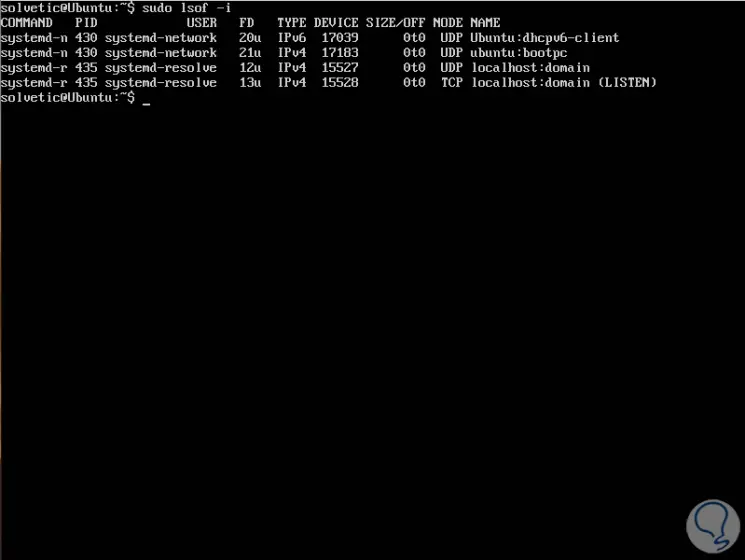
The lsof command is a tool through which it will be possible to list the files opened in the system with details such as which files keep a certain process (PID) or user open and with details such as the port used by those services.
To list all the Internet and network files, we must use the -i option, with this command a combination of service names and number ports is displayed:
sudo lsof -i
If we want to see which application uses a specific port we can execute the following:
sudo lsof -i: 80
With any of these options it will be possible to visualize the open ports in Linux and have a better control over them.