There is nothing more delicate in the world of networks than the privacy of each user since, regardless of whether or not we handle information considered confidential or top secret, we are users who can register personal data such as bank accounts or card numbers on a daily basis. credit. Regardless of what type of user we are, privacy is a right that must be respected anywhere in the world and in any operating system or application used..
Google, the giant of the network and through which all our data pass, has issued an announcement about a recent investigation in which it was reported that certain applications developed by third parties are in the ability to scan the Gmail inboxes. The Google mail platform, in order to collect marketing data, and Google indicates that it examines these applications and suspends their developers that do not meet the privacy standards that have been described in their legal conditions.
This research was developed by the Wall Street Journal (WSJ) which is known worldwide for its research. This investigation took place at the beginning of this month of July, and it is mentioned that certain marketing companies were detected that executed automatic scans to the email inboxes automatically and sometimes it was the developers themselves who analyzed and they read the emails in the tray which is a serious security breach..
The investigation in question indicates that the marketing companies Return Path and Edison did not send reports on time and in an appropriate way to the users indicating that their emails could be read by a third party, something that must be approved by the user itself, But these companies maintain that their user agreements were properly disclosed, which leaves many questions to be resolved.
A point that gives us peace of mind, but does not omit responsibility, is that this investigation ensures that no malicious action was found in these applications as happens in many cases when malicious software is added and more. Something that as Gmail users we must keep in mind, is that Google allows certain third-party apps, such as trip planners, calendars and more , can add extra functions within each user's email to fully accomplish their goal, but with our permission, like this, these apps have unrestricted access to emails in Gmail..
The response from Google indicates the following: "We reviewed non-Google applications to ensure they continue to comply with our policies and suspend them when they do not," but the WSJ investigation reported that certain Return Path employees had access to more than 8 thousand emails for two years in order to configure the software of the company itself.
To do this, the Return Path email scanning software marked each personal email as commercial, while the other company involved in this investigation, Edison Software, which was created to help users manage their email better In this way, I provide access to your employees to read thousands of Gmail messages in order to apply and manage the "Smart reply" function.
Recall that Google has suffered from several demands for reading emails between 2010 and 2016 and after these demands, Google announced in 2014 that it would stop reading emails from students, government employees and the private sector, while, In June 2017, Google announced that it stops all types of email reading.
In the following link from Google, we can read the complete answer provided by Google through Suzanne Frey who is the director of the Security, Trust and Privacy division of Google Cloud:
Google response
Now, well, as Gmail users we can also take certain privacy measures that will help to have a more secure and comprehensive email and TechnoWikis will explain some useful ways to achieve it.
1. How to monitor or stop applications that use Gmail
Step 1
This point is vital since it will be possible to really know which applications have the necessary permissions to use Gmail and there we can decide which ones will be authorized.
To check which applications have permission in Gmail, we must go to the following link:
Gmail permissions
There we will log in and see the following:
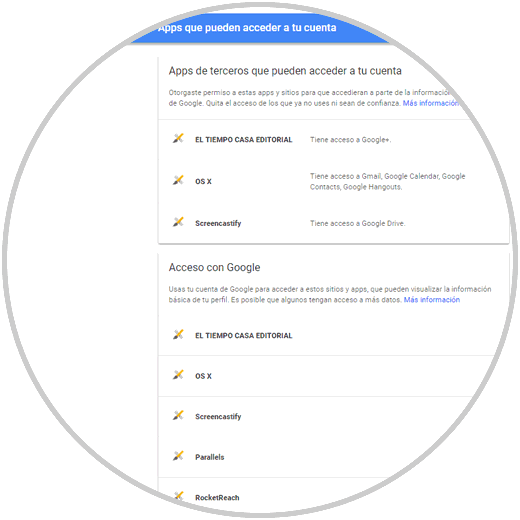
Step 2
There we can click on any application in the list to which access will be denied and to do this click on the Remove access button:
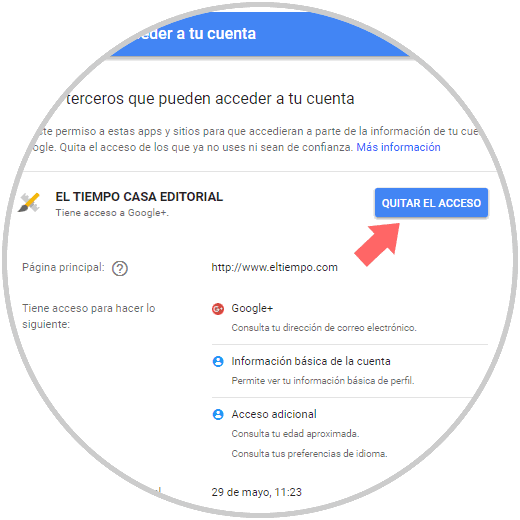
Step 3
The following window will be displayed where we confirm the action by clicking on Accept:
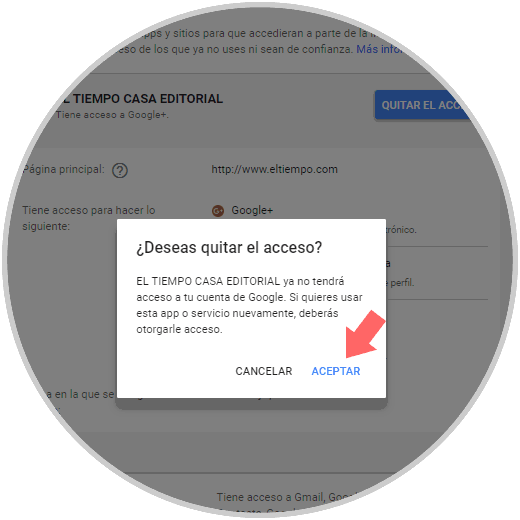
Step 4
Google can also control what elements we can use to manage the information, for example, Google Security Control which shows the applications with access to our information and is able to mark the S that are considered at risk, and it will be possible Remove said access.
To use this security method we will go to the following link:
Google Security Verification
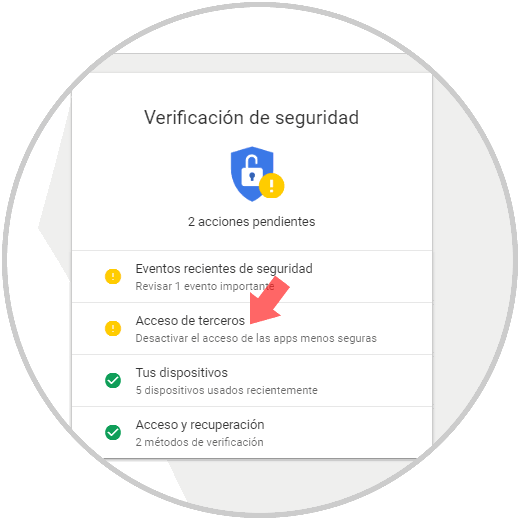
Step 5
There we click on Third Party Access and there we will see the level of risk of each application and it will be possible to remove its access by clicking on the Remove access button:
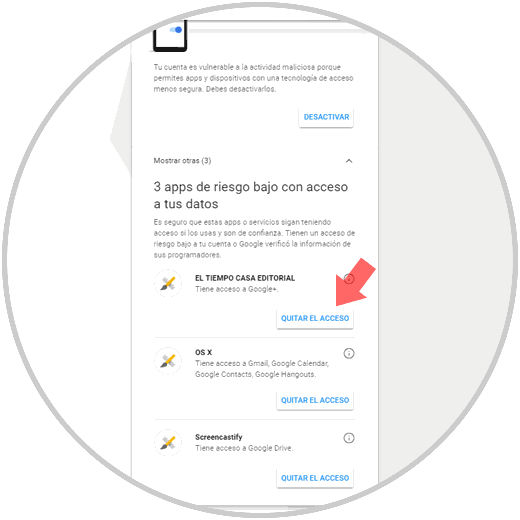
Finally, and as an extra point of security, both in Gmail for mobile systems and in desktop Gmail, we must carefully review the permission options before granting access to a non-Google application.
Step 6
Whenever we try to install an application, it requests the necessary permissions to carry out its task effectively. Within these permissions we find access to mail, calendar, contacts and more, we must be cautious when granting such permissions and thus prevent them from accessing our email.
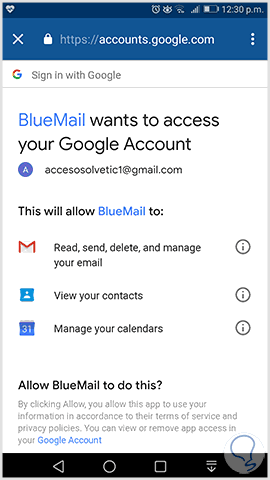
2. How to manage Gmail comprehensively
Step 1
Gmail has a group of tools to verify and adjust the security settings, both for Gmail and for the rest of the services and it is useful to access it and see what options apply to avoid such problems using Gmail.
For this we will access the following link.
Gmail protection
We log in and we will see the following:
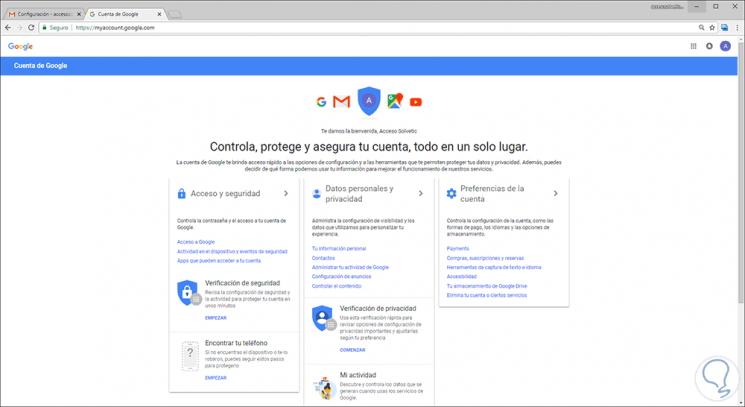
Step 2
We can see the following sections:
Access and security
From this section it will be possible to control the password and access to the Google account.
Personal data and privacy
From this section you can manage all the visibility settings and the data that are used in order to customize the experience of using Gmail.
Account Preferences
There it will be possible to set the values ​​of the Gmail account
Some options available internally in these options are:
Checking recovery information
When we create a new account, Google asks us to enter a recovery phone number and an email address in order to retake the account in case of loss or forget the password.
Recent security event check
This option is useful for managing recent security events with the account, there we will see situations such as when you logged into the Gmail account from different devices and the changes that have been made such as the password, telephone or email recovery. There we can manage these values ​​and define if someone has used this without permission.
Checking connected devices
From here we can verify all the devices connected to the Gmail account such as PCs, tablets and smartphones, in case you see an unknown device in the list, it must be removed.
Account Permit Verification
As the name implies, it allows you to verify the permissions of the Google account, there we will see a list of applications and websites that are authorized to access the Gmail or Google account.
Step 3
The first step to take is to click on the Security Verification section with the aim of Gmail giving us a summary about the status of our Gmail account. There we can click on each section to see its results in detail.

Step 4
Since we are talking about privacy in Gmail, one of the most useful options is to click on the Privacy Settings section which will display the following wizard:
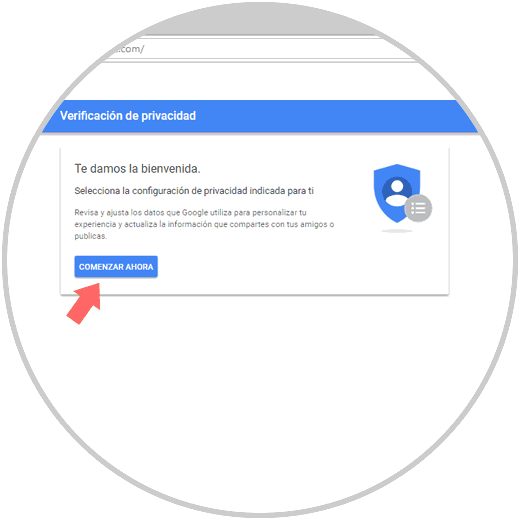
Step 5
Click on the Start now button and we will see this:
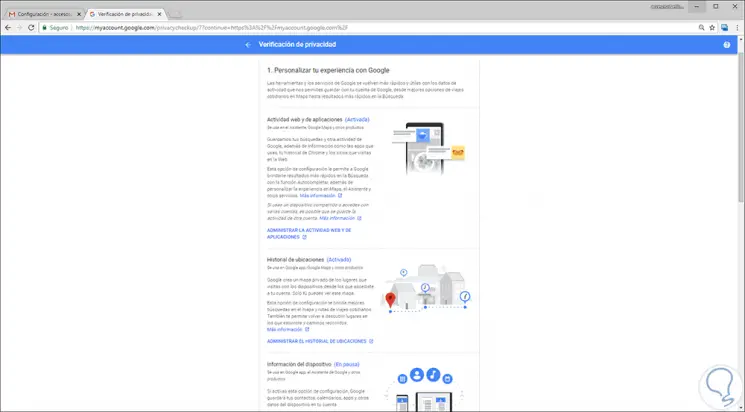
Configurations
There it will be possible to manage the following associated with the privacy of the account:
- Web activity and applications
Step 6
Just click on one of these lines to access the complete information of each aspect to verify:
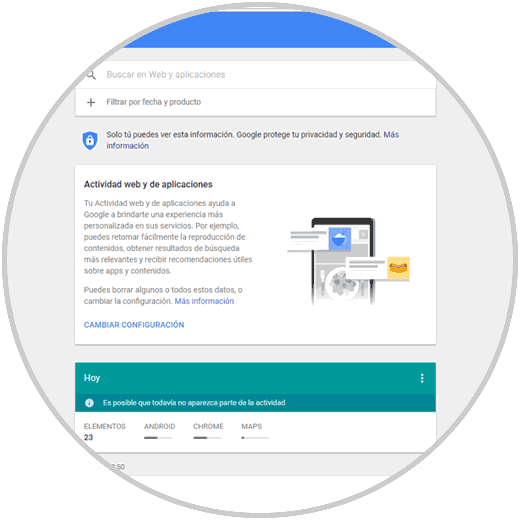
Step 7
At the bottom of the privacy settings we have the option Control personal information that other users can see in which you can establish what kind of details the other users of us can see:
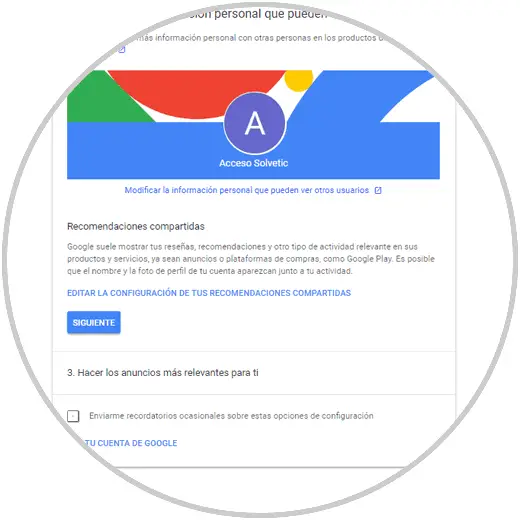
Step 8
There it will be possible to edit this information as necessary:

Step 9
Finally, in the third section, we find the administration of ads with which it is allowed to enable or disable the ads based on our interests:
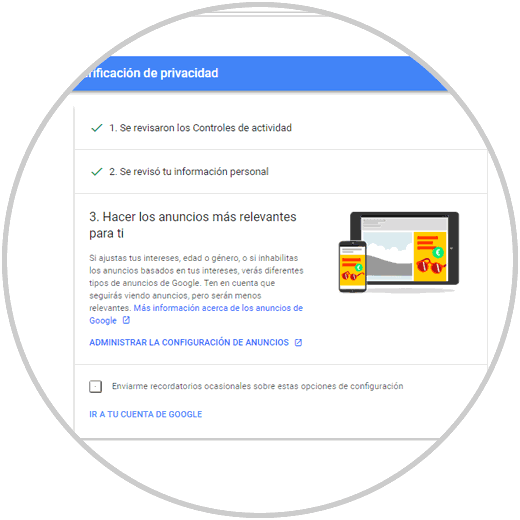
Step 10
When accessing this configuration we can deactivate it permanently by pressing on the switch or click on each taste that is hosted there:

Step 11
When clicking on a taste, just click on the Disable button so that it is removed from there:
We can see that part of the privacy depends on us as Gmail users and therefore it is advisable to perform these checks frequently to see the status of the Gmail account.