In a world that revolves around online operations, it is of the utmost importance, almost vital, to have the necessary security measures to prevent user data, as well as the infrastructure already defined, from being violated and could be stolen, destroyed, edited or any action that prevents its optimal functioning..
A few weeks ago we saw a new threat that was detected nothing more and nothing less than in the processors recognized worldwide. Which puts us in a somewhat complex situation since if our processors, which are more than important within any computer equipment, become a platform for a threat to be propagated in the system, what else should we review in pro of the security of our information?
Specter and Meltdown were vulnerabilities that leaked through the processor and have been developed to allow any attacker with the necessary knowledge to capture information from the processor to which, in theory and in practice they should not have access, including passwords and passwords. which is a high level of security
The worst of this is that Specter and Meltdown attack Intel and AMD equally, which are renowned manufacturers with high reputation at the processor level which makes us the majority of users in potential victims. With Specter, attackers are allowed to cheat the processor in order for it to start the speculative execution process. Thanks to this, the attackers can read the secret data inside the processor which is available to the attackers while trying to guess what function the team will execute soon.
With Meltdown, attackers are allowed to access the secret information of each user through the operating system such as Microsoft Windows, Linux in many of their distributions or Apple. For this reason, at TechnoWikis we want to carry out an analysis on how we can check if our Linux operating system is prone or not to these two vulnerabilities and, if necessary, take the necessary security measures which involve downloading and installing the latest security patches. from developers or make use of special tools for this purpose..
1. How to check Meltdown or Specter Linux vulnerability basic mode
In the case of Linux, we have the option to run a simple test of verification which was offered by the Linux kernel developers and this test gives us the possibility to verify the status of the distribution at the level of these Meltdown and Specter vulnerabilities.
Step 1
Although it is a basic line, it is not available for all Linux distributions.
The line to be executed is as follows:
grep. / sys / devices / system / cpu / vulnerabilities / *
As we have indicated, in some systems this analysis is not available, this implies that the kernel does not have that directory or sysfs files. This is a warning of a problem and it will be necessary to update the kernel to the latest version. In case of not having this directory we will see the following error:
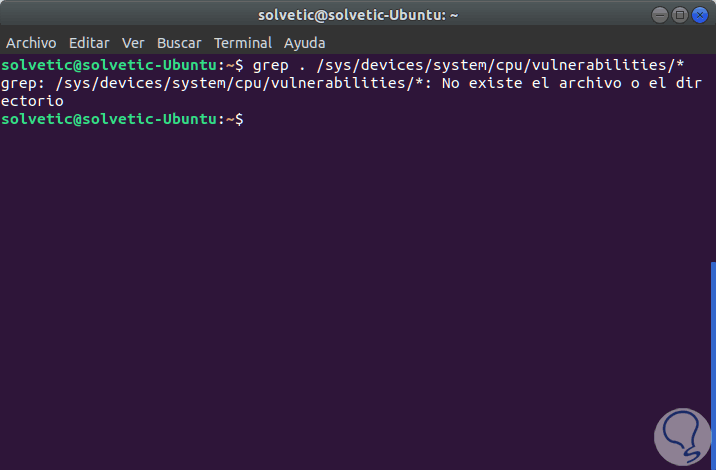
Step 2
As we see our system does not have the available vulnerabilities directory and although it has been indicated that the solution lies in updating the system kernel this has not worked. Now, this process works correctly in CentOS or RedHat, but for this we must update the kernel to its most current version, in this case it will be 4.15.0.
To know in detail how to update the kernel in CentOS 7 we can visit the following link:
Update Kernel
Once the kernel has been updated we can execute the following command already indicated:
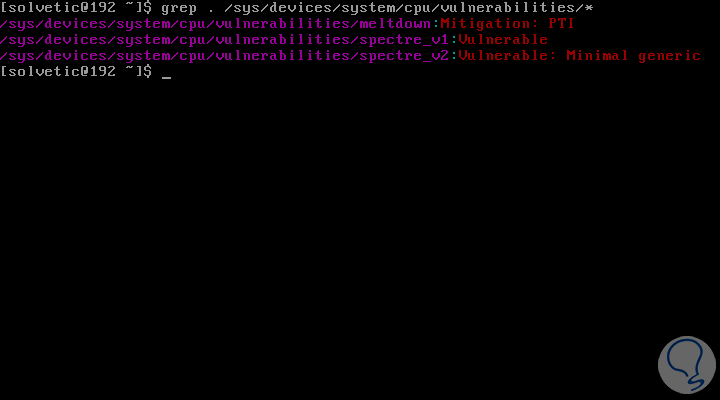
grep. / sys / devices / system / cpu / vulnerabilities / *
As a result, we will see the following report indicating whether or not we are vulnerable to these threats:
2. Check Meltdown or Specter Linux vulnerability using a script
If we find the following error in our distribution we should not worry as we have the opportunity to validate these vulnerabilities in a complete and much more detailed way. To do this we will use a script that was developed to obtain accurate data on the type of security of our system and clearly tell us whether or not we are susceptible to the threat.
To obtain this script, we must have Git installed in the operating system, if not, we will execute the following:
Once installed, we will clone the script repository in any directory, in this case Downloads, like this:
cd / Downloads
git clone https://github.com/speed47/spectre-meltdown-checker.git
When the cloning process is finished, we will enter the newly created directory and execute the downloaded script like this:
cd specter-meltdown-checker ./spectre-meltdown-checker.sh
The result is a bit extensive and in the first section we will see whether or not we are vulnerable or not to the different variables of these vulnerabilities:
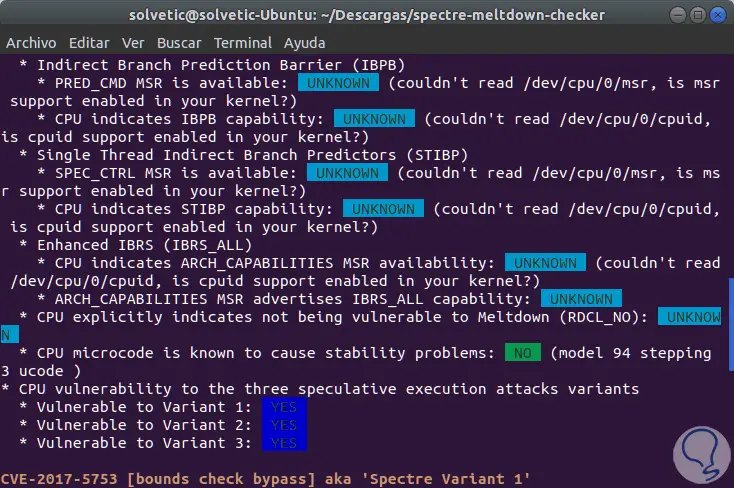
In this case we see that we are vulnerable to all the variables of these threats. In the final part we will see more detailed information about the different types of threats:
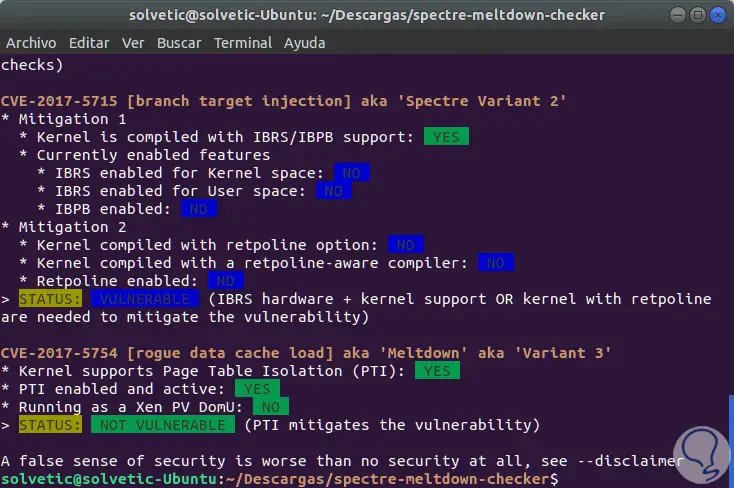
That easy, but totally useful, we can analyze whether or not our system is vulnerable to Specter and Meltdown. In the following link we find more detailed information about these vulnerabilities and we will see how we can protect ourselves