Currently one of the current devices that most of us have and that becomes a useful tool for its practicality and capacity are USB devices, called external disks, USB sticks or SD drives, these allow us to store large amounts of data and even install operating systems from them..
Although this is functional and novel, USB devices are a means by which viruses, malware and the worst can be transmitted, can be used to steal information , a situation to which every administrator is exposed is that any of the users connect a USB media on your local computer and can perform the following:
- Download of multimedia elements in which malware, ransomware, etc. may be hidden.
- Copy of confidential documents
- Installation of unauthorized programs
- Replication or propagation of information throughout the network and more.
In this case, the most suitable solution is to block the use of USB devices on the server and thus add a level of security within the organization.
In TechnoWikis we will analyze how to achieve this with some steps and thus avoid problems in the short, medium or long term..
1. Check if the driver is in the Linux kernel
To disable USB media support on the server, first of all, it will be necessary to identify if the storage controller is loaded in the distribution kernel, in this case Ubuntu 17, and validate the name of the controller responsible for this storage medium .
Step 1
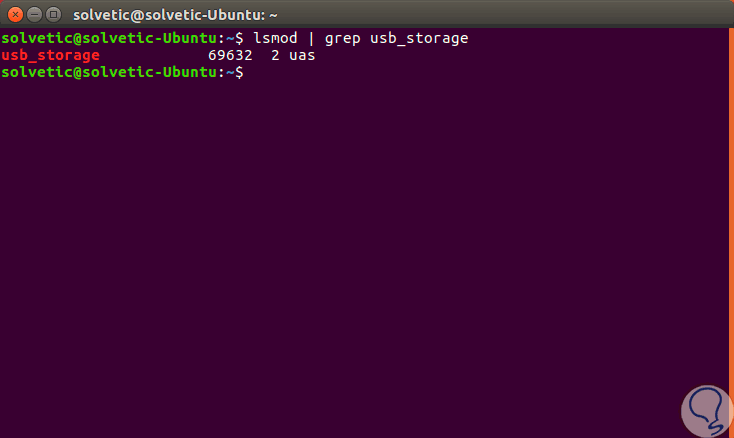
To verify this we will execute the following. Thanks to the "lsmod" command it is possible to validate that the "usb_storage" module is in use by the UAS module.
lsmod | grep usb_storage
Step 2
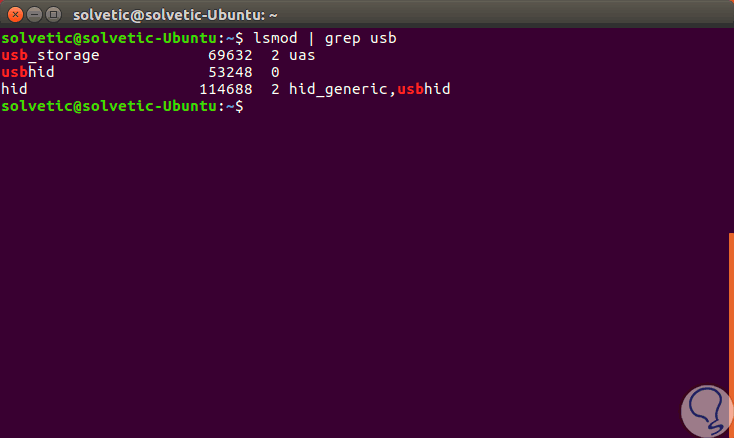
The next step will be to download both kernel USB storage modules and verify if the removal process has been completed successfully, for this we can execute the following commands:
modprobe -r usb_storage modprobe -r uas lsmod | grep usb
2. Edit policies in Linux
Step 1
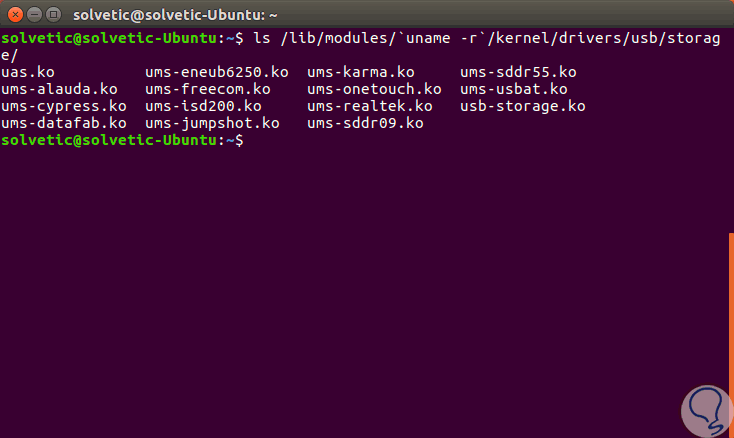
The next step will be to list the content in the USB storage module directory of the current kernel using the following command:
ls / lib / modules / `uname -r` / kernel / drivers / usb / storage /
Step 2
There we must identify the name of the usb storage controller which in most cases has the following format:
usb-storage.ko.xz usb-storage.ko
Step 3
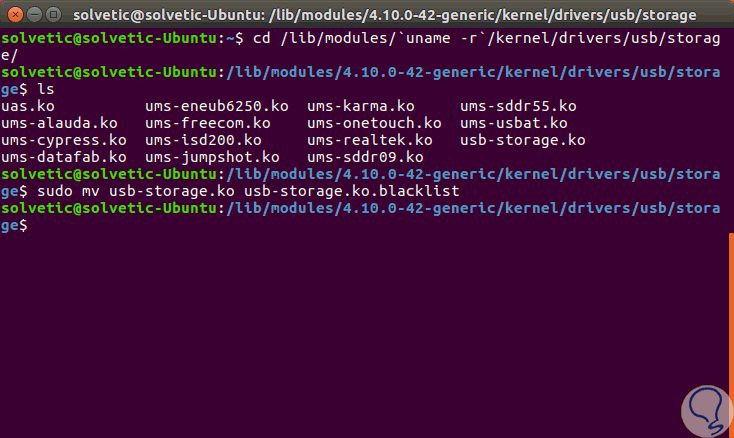
Now, to block the USB storage module in the kernel, it will be necessary to change the path of the usb storage modules from the directory to the kernel and then rename the usb-storage.ko.xz module to usb-storage.ko.xz. blacklist or usb-storage.ko to usb-storage.ko.blacklist, using the following commands:
cd / lib / modules / `uname -r` / kernel / drivers / usb / storage / ls sudo mv usb-storage.ko usb-storage.ko.blacklist
Note
In this case our device is identified as usb-storage.ko.
Step 4
In the case of Debian we must execute the following commands for blocking the usb storage module:
cd / lib / modules / `uname -r` / kernel / drivers / usb / storage / ls sudo mv usb-storage.ko usb-storage.ko.blacklist
Thus, when any USB media is connected to the computer, the kernel will not be able to load the respective input kernel of this storage controller.
Step 5
At the moment we want to revert the changes just rename the device to its original name by executing the following:
cd / lib / modules / `uname -r` / kernel / drivers / usb / storage / mv usb-storage.ko.blacklist usb-storage.ko
3. Block USB devices with chmod in Linux
The goal of TechnoWikis is to give the best solutions and therefore we will explain another simple method to achieve the blocking of USB devices in Linux.
We know very well that each USB is mounted in / media / or if the distribution uses systemd, it will be mounted in / run / media /, therefore, we must edit the permissions of these routes so that only the root user has access and nobody else , for this we will execute the following:
sudo chmod 700 / media /
Or in her case:
sudo chmod 700 / run / media /
With this method, the unit will be mounted, but no notification will be displayed to the user, nor will it be able to directly access its contents, only the root user.