One of the fundamental components in any equipment designed to use an operating system, regardless of its developer, is the CPU or processor which has been advancing in giant steps offering us new processing speeds , new technologies, more cores and all this in order to optimize and improve the system startup and the execution of the programs we have installed there..
All this is innovative and it fills us with excitement when we buy a computer with an excellent processor since we are sure that it will be a good investment but what happens if the processor, be it Intel, AMD or other, presents within its design security vulnerabilities that They put our information and our confidentiality at risk, there the subject changes course and makes us think about how it is possible that such situations happen in renowned processors and large companies worldwide.
Well, this vulnerability is a reality that was discovered a few days ago, on January 4, where Specter and Meltdown vulnerabilities were discovered which are linked to the processor design where an attacker is allowed to access system information and of the memory where vital elements are housed as encryption keys or passwords..
The worst of all this issue is that these vulnerabilities affect Intel, ARM and AMD processors, so we are all open to being victims of these vulnerabilities and that is why today at TechnoWikis we will thoroughly analyze what these vulnerabilities are, how they attack and how we can protect our servers and equipment from them.
Recall that these vulnerabilities will attack all types of equipment both at home and business level and currently the patches that will serve to protect us against Specter and Meltdown are being released by the developers of operating systems and applications..
What is Specter

Specter is a vulnerability that has the ability to fool the processor in order to initiate the speculative execution process because modern processors make use of branch prediction and speculative execution maximizes processor performance. .
Specter attacks allow a victim to speculatively induce certain operations that would not occur during the correct execution of the program and this allows confidential information to be filtered through a side channel to the attacker very simply.
The disclosure notices of these vulnerabilities have discovered two variants with different levels of complexity and impact of Specter on the processor and with it on user security.
These variants are:
Variant 1 (CVE-2017-5753)
This vulnerability affects the Intel, AMD and ARM processors, allowing the attacker to cheat the programs without any error, following best practices, to filter all user information stored on the computer.
This was discovered on January 3 of this year by the Google Project Zero team and this variant makes excessive use of speculative execution in order to perform limit-check bypass tasks which causes the kernel code to be redirected with control of the attacker speculatively.
A list of the systems that can be attacked by this variant are:
- Red Hat Enterprise Linux 5
- Red Hat Enterprise Linux 6
- Red Hat Enterprise Linux 7
- RHEV-M 4.0
- RHEV-M for Servers
- Red Hat Enterprise Linux OpenStack Platform 7.0 (Kilo) for RHEL 7
- Red Hat Enterprise Linux OpenStack Platform 6.0 (Juno) for RHEL 7
- Red Hat Enterprise MRG 2
- Red Hat OpenStack Platform v 8/9/10/11/12
- Debian Linux wheezy
- Debian Linux Jessie
- Debian Linux stretch
- Debian Linux buster, sid
- SUSE Linux Enterprise Server for Raspberry Pi 12 SP2
- SUSE OpenStack Cloud 6
- Openstack Cloud Magnum Orchestration 7
- SUSE Container as a Service Platform ALL
- SUSE Linux Enterprise High Availability 12 SP2 / SP3
- SUSE Linux Enterprise Live Patching 12
- SUSE Linux Enterprise Module for Public Cloud 12
- SUSE Linux Enterprise Server 11 SP3-LTSS
- SUSE Linux Enterprise Server 11 SP4
- SUSE Linux Enterprise Software Development Kit 11/12 SP3 / SP4
- SUSE Linux Enterprise for SAP 12 SP1
- SUSE Linux Enterprise 11
- SUSE Linux Enterprise 12
- OpenSuse Linux based upon SUSE 12/11
- Fedora Linux 26
- Fedora Linux 27
- Amazon Linux AMI
Variant 2 (CVE-2017-5715)
This variant is responsible for triggering the speculative execution using the branch target injection. It is based on the presence of a specific sequence of instructions defined precisely in the privileged code, as well as on the situation that memory accesses can cause allocation in the microprocessor data cache including speculatively executed instructions that are never They will be compromised.
Thanks to this variant, an attacker without any privileges would have the ability to cross the boundaries of the system and the equipment to read the privileged memory by conducting targeted side channel cache attacks and thus see the security of the user penetrated.
The affected systems are the same as indicated above.
To prevent these variants in Linux we can carry out the following process.
In CentOS or RedHat environments we first execute the following lines:
join me -r sudo yum update
Once the system is updated, we proceed to restart the system by executing the line:
sudo reboot
Then we confirm that the kernel has been updated using the command again:
join me -r
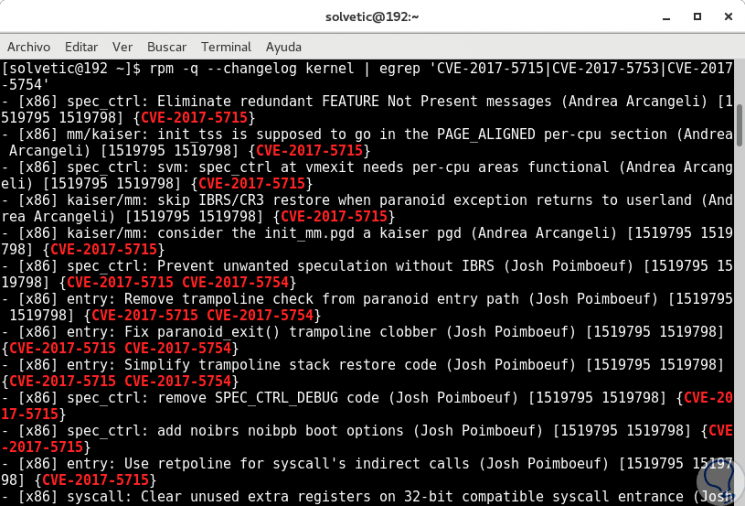
Finally we verify that the variants are applied in the system by executing the following:
rpm -q --changelog kernel | egrep 'CVE-2017-5715 | CVE-2017-5753 | CVE-2017-5754'
In the case of using Ubuntu or Debian we can execute the following lines:
sudo apt-get update sudo apt-get upgrade sudo shutdown -r 0
Specter Attack Forms
Specter makes use of some attack techniques such as:
- Exploiting speculative execution. With this technique, Specter attacks the processor's task at the level of speculative execution instructions with sequences that should not have been executed during the correct execution of the program and these sequences will finally be reversed creating transient instructions which the attacker takes advantage of to filter user information affected.
- Attacks using native code :. This attack creates a program that contains secret data within its access memory and once this program has been compiled, binaries and shared libraries are analyzed in the system in order to filter user information.
Finally, another attack program is written that exploits the speculative execution function of the CPU to carry out the sequences previously found as transient instructions.
- Attacks using JavaScript. This attack is used to violate the browser's test zone by mounting a portable JavaScript code through it.
Hardware affected by Specter
Currently it has been discovered that Specter is in the ability to violate hardware such as:
- Ivy Bridge based processors
In summary, the Specter attack is composed of the following phases:
- Phase 1. First, the attack begins with a configuration phase, where the adversary performs operations that cause the processor to fail so that speculative misuse can be carried out.
During this phase, the attacker can prepare the side channel that will be used to extract the victim's information.
- Phase 2. In this phase, the processor speculatively executes one or more instructions that transfer confidential information of the victim's context in a side channel microarchitecture.
This allows the attacker to perform an action, such as syscall, socket, and in other cases the attacker can take advantage of the speculative execution of his own code to obtain sensitive information from the same process by the user.
- Phase 3. In this phase confidential data is recovered from Specter using techniques such as flush + reload or evict + reload. This recovery process consists in measuring how long readings of memory addresses take in the cache lines that are monitored periodically.
What is meltdown

The other attack that affects the security of users is Meltdown which allows an attacker to access the user's private information through the installed operating system, such as Microsoft Windows or High Sierra.
Its name has been assigned by the ability to violate the security limits normally imposed by the system hardware.
Meltdown's vulnerability has been cataloged as CVE-2017-5754 where it is mentioned that Meltdown has the ability to penetrate the basic isolation between user applications and the operating system no matter what it is. This attack allows a program to access memory and, thus, also the confidential information of other programs and the operating system itself.
This ruling was also discovered on January 3 by the Google Project Zero team and other additional teams.
This vulnerability affects Intel x86-64 processors but not AMD x86-64 processors.
Meltdown may affect system such as:
- Red Hat Enterprise Linux 5
- Red Hat Enterprise Linux 6
- OpenSuse Linux based upon SUSE 12/11
We currently have the solution for this vulnerability for the following Linux distributions with their kernel version like this:
- RHEL 6.x [2.6.32-696.18.7] /7.x [3.10.0-693.11.6]
- CentOS 6.x [2.6.32-696.18.7] /7.x [3.10.0-693.11.6]
- Fedora 26 [4.14.11-200] / 27 [4.14.11-300]
- Debian stretch [4.9.0-5-amd64] / jessie [3.16.0-5-amd6] / wheezy [3.2.0-5-amd64]
- Arch Linux [update to current rolling]
- Gentoo Linux [update to current rolling]
- Ubuntu Linux v16.04 [4.4.0-109-generic or 4.13.0-26-generic] /v17.10 [4.13.0-25-generic] /14.04 [3.13.0-139-generic]
- SUSE - SLES 12 SP3 [4.4.103-6.38.1] / SLES 12 SP2 [4.4.103-92.59.1] / SLES 11 SP4 [3.0.101-108.21.1] / SLES 11 SP3-LTSS [3.0.101 -0.47.106.11.1]
To protect ourselves from this vulnerability CVE-2017-5754 we can execute the following:
join me -r sudo yum update sudo reboot
sudo dnf --refresh update kernel
join me -r sudo apt-get update sudo apt-get dist-upgrade sudo shutdown -r 0
How Meltdown works
Recall that one of the central security features at the operation level in modern operating systems is memory isolation which ensures that users' applications do not have access to the memories of other users and programs and thus prevent applications from of users can read or write in kernel memory.
In modern processors, the isolation between the kernel and user processes is normally executed by a processor bit supervisor which defines whether a memory has the ability to access the kernel page or not.
Meltdown has been developed as a new attack that has the power to overcome memory isolation completely by providing a simple way for any user process that can read the kernel memory of the running machine, including all the physical memory allocated in the memory. kernel region
Meltdown works on all major operating systems today and this vulnerability exploits the side channel information available in most modern processors such as Intel or AMD.
Meltdown gives an attacker the ability to execute code on a vulnerable processor in order to obtain a dump of the entire kernel in the address space, including any allocated physical memory.
The cause of the simplicity and scope of Meltdown are side effects caused by out-of-order execution, that is, it is a feature of current processors that has been developed to overcome the latencies of occupied execution units.
The work phases of Meltdown are:
- Phase 1. In this phase a request is made for an illegal memory location in the processor kernel.
- Phase 2. In this phase a second request is made in order to conditionally read a valid memory location only if the first request contains a certain active value.
- Phase 3. In this phase, the speculative execution task is carried out where the processor completes the background work for the previous two requests before verifying that the initial request is invalid. As soon as the processor understands that the requests involve memory out of bounds, it denies both requests.
- Phase 4. There is a new request for the valid memory location.
Thus we can define the following with the Meltdown vulnerability:
The content of a memory location chosen by the attacker, which is inaccessible to the attacker, is loaded into a system registry.
A transient instruction accesses a cache line based on the secret content of the record.
The attacker uses Flush + Reload to determine access to the cache line and, therefore, access the information stored in the chosen memory location.
Once we have understood how these vulnerabilities work, we will see how we will protect our equipment from them, although we must clarify that to date no attack has been reported that causes concern for both users and administrators.
To keep up, remember to subscribe to our YouTube channel! SUBSCRIBE
1. How to protect yourself from Specter and Meltdown on Linux systems
In the case of Linux, we will use spectre-meltdown-checker.sh which is a shell script to determine if the Linux kernel is vulnerable against the 3 CVEs we have mentioned of these vulnerabilities.
Note
This script must be executed as root user.
Step 1
To install this script first we will go to directory / tmp like this:
cd / tmp /
Step 2
Once we are in that directory we proceed to obtain the script by executing the following line:
wget https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh
How to verify whether or not we are vulnerable to Specter or Meltdown
To check the security of our distribution we can execute the following line:
sudo sh specter-meltdown-checker.sh
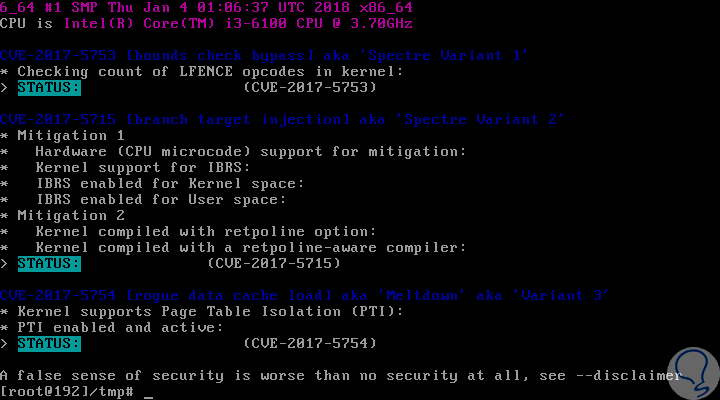
It's that simple We can verify whether or not our system is vulnerable to these new threats.
2. How to protect yourself from Specter and Meltdown on Windows systems
In this case we will use Windows 10 and for this we must access Windows PowerShell as administrators by right clicking on the application and selecting the option “Run as administratorâ€.
Step 1
Once the PowerShell terminal is open, we proceed to execute the following line:
Install-Module SpeculationControl
Step 2
In the questions displayed we will enter the letter S to confirm:
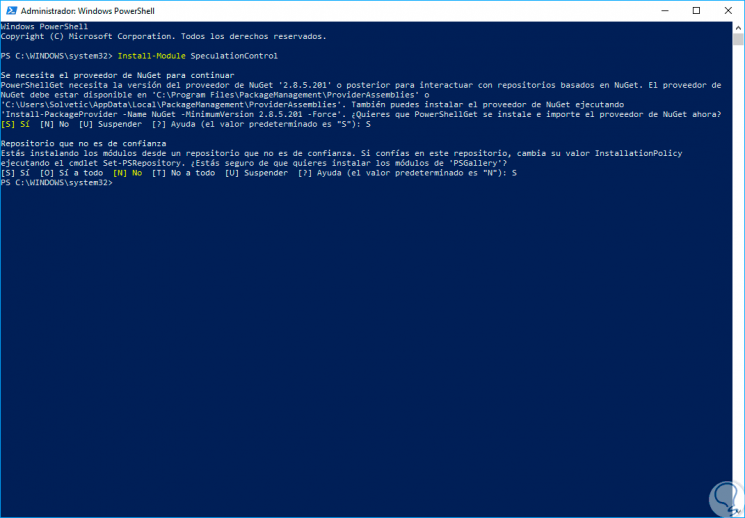
Step 3
The standard Windows execution policy will not allow us to run this script, for this, in order to run the script, we must save the current configuration so that it can be restored later and then change the execution policy so that it can be run the script For this we will execute the following two commands:
$ SaveExecutionPolicy = Get-ExecutionPolicy Set-ExecutionPolicy RemoteSigned -Scope Currentuser
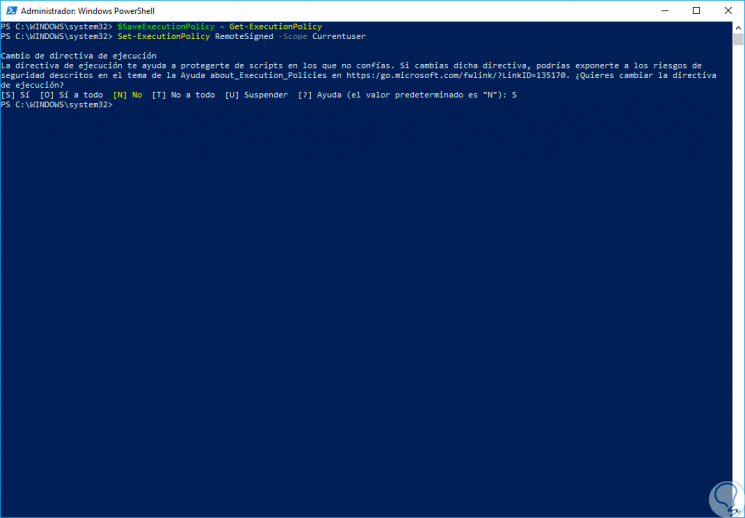
Step 4
Now, we can execute the script by executing the following:
Import-Module SpeculationControl Get-SpeculationControlSettings
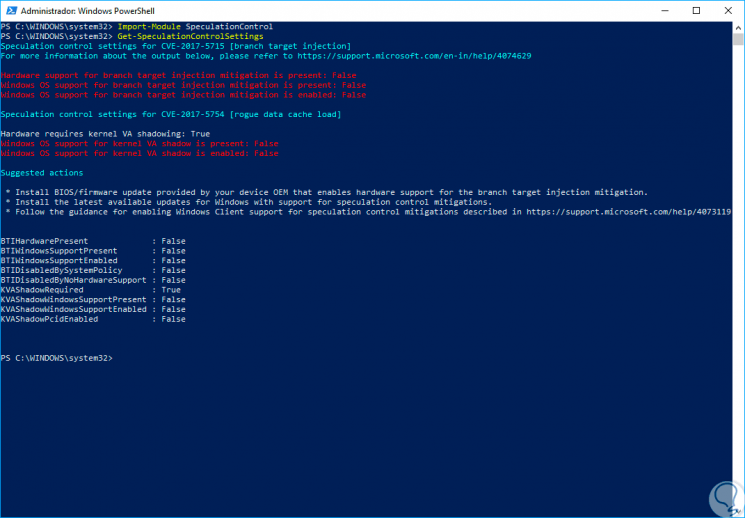
Step 5
We can see detailed information of the system and we must look at two lines in particular:
Windows OS support for branch target injection mitigation
This line indicates the Microsoft software update and if its value is true it means that the computer is protected against attacks by Meltdown and Specter.
Hardware support for branch target injection mitigation
This line refers to the firmware or BIOS / UEFI update required by the equipment manufacturer if its value is true means that we will be protected against the Specter vulnerability.
Step 6
To restore the execution policy to its original configuration after checking the security of the system, we can execute the following line:
Set-ExecutionPolicy $ SaveExecutionPolicy -Scope Currentuser
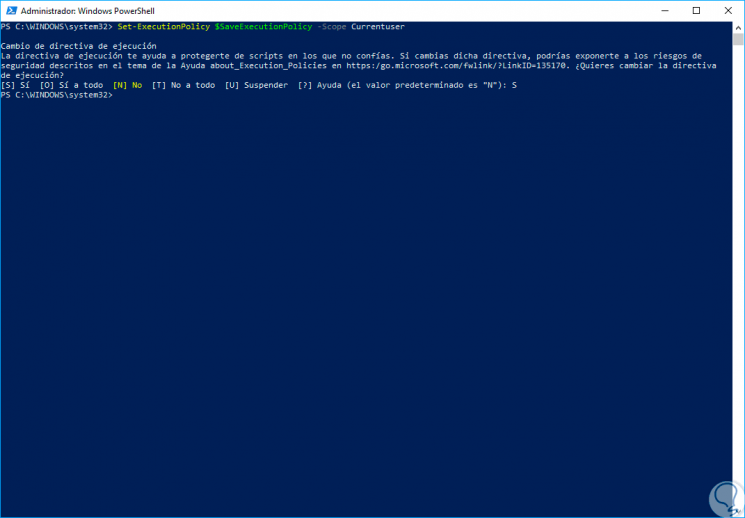
Step 7
It is not important to remember the importance of keeping the operating system updated as developers will be launching security patches to prevent these security flaws:
3. Official Specter and Meltdown information by manufacturers
In the following links we can find information about these vulnerabilities in each of the sites of the main developers and thus have more detailed information on how to prevent and be one step ahead of the problem:
As we can see, although vulnerabilities will always be present we can take the necessary measures to be alert to any failure and thus prevent our information from being affected.