As administrators , IT support personnel or in charge of the networks and systems area, we have something fundamental to help us keep track of every event that occurs within the system both at the level of users and of applications or of the system itself and these are the events
Each event registers a series of elements that help us to determine in detail each activity with values ​​such as date, time, ID, user and event occurred allowing us a much more centralized management and administration .
We can see that each record belongs to a different category such as system, security, etc..
In Linux environments we have at our disposal the Rsyslog utility with which it will be possible to manage this events simply and completely.
What is Rsyslog
Rsyslog (rocket-fast system for log) is a utility designed to offer high performance, excellent security features and a modular design that allows it to be scalable to suit every need of the company.
Rsyslog is able to accept inputs from a wide variety of sources, transform them and generate results for various destinations optimizing IT management..
RSYSLOG is able to deliver more than one million messages per second to local destinations when limited processing including remote destinations is applied.
Rsyslog features
When using Rsyslog we will have features such as:
- $ LocalHostName [name] directive: This directive allows us to overwrite the host name of the system with the one specified in the directive. If the directive is given several times, all but the last will be ignored.
- Support for Hadoop HDFS added.
- It has an impstat module to run periodic statistics on Rsyslog counters.
- It has the imptcp plugin.
- It includes a new type of "string generator" module, used to accelerate the output processing.
- Supports OSX and Solaris.
- Ability to create custom message analyzers.
- Multi-ruleset support for imudp.
- New transactional output module interface that provides superior performance.
- Compatible with TCP, SSL, TLS, RELP protocols
- Supports MySQL, PostgreSQL, Oracle and more
- Filter any part of the syslog message
- Fully configurable output format
- Suitable for business-class relay chains
Rsyslog filtering
Rsyslog can filter syslog messages based on the selected properties and actions, these filters are:
- Facility or Priority Declarants
The facility filter is represented by the internal Linux subsystem that is responsible for producing the records, we have the following options:
- auth / authpriv = Are the messages produced by authentication processes
- cron = They are records associated with cron tasks
- daemon = These are messages related to the services of the running system
- kernel = Indicates Linux kernel messages
- mail = Includes mail server messages
- syslog = Are the messages related to syslog or other daemons
- lpr = Covers printers or print server messages
- local0 - local7 = Count custom messages under administrator control
Priority or severity levels with Rsyslog are assigned to a keyword and a number as follows:
- notice = Notification - 5
1. How to configure and verify the status of Rsyslog on Linux
Step 1
The Rsyslog daemon is automatically installed on most Linux distributions, but if not, we must execute the following commands:
On Debian systems
sudo apt-get install Rsyslog
On RedHat or CentOS systems
Step 2
We can verify the current status of Rsyslog by running the following line:
On Linux distributions that use Systemd
systemctl status rsyslog.service
In older versions of Linux
service rsyslog status /etc/init.d/rsyslog status
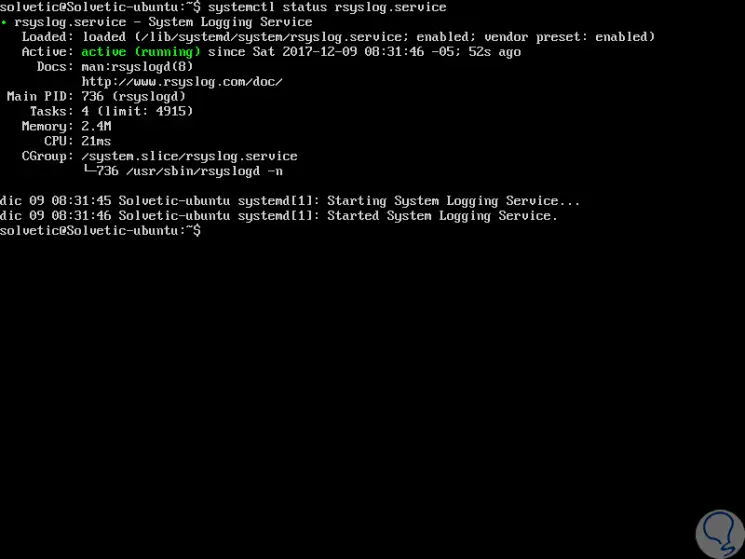
Step 3
In case the Rsyslog service status is inactive, we can start it by executing the following:
In new versions of Linux
systemctl start rsyslog.service
In older versions of Linux
service rsyslog start /etc/init.d/rsyslog start
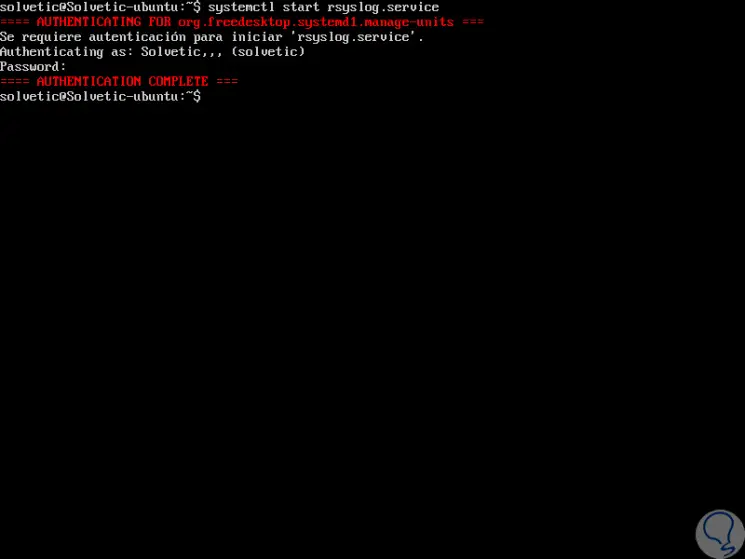
2. Rsyslog configuration on Linux
To configure an rsyslog program to be executed in server mode, we must edit the configuration file in the /etc/rsyslog.conf directory.
Step 1
We can access using the desired editor:
sudo nano /etc/rsyslog.conf
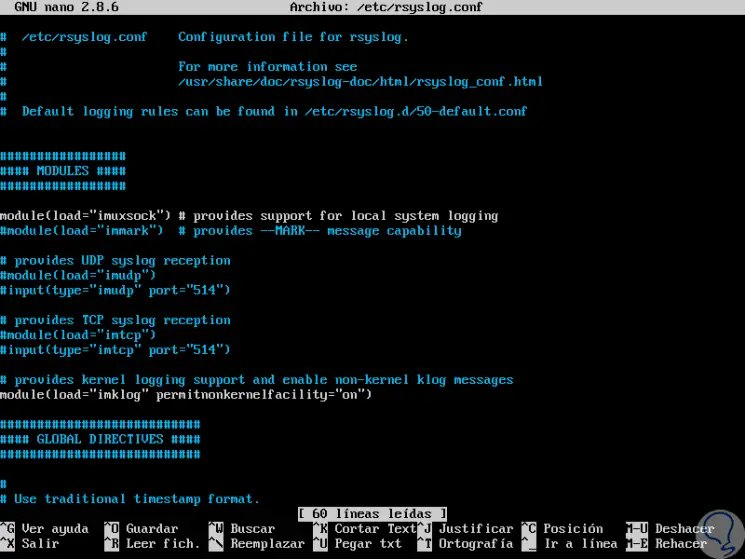
Step 2
There we will make the following changes. Locate and uncomment, removing the sign (#), from the following lines to allow the reception of UDP log messages on port 514. By default, the UDP port is used by syslog to send and receive messages:
$ ModLoad imudp $ UDPServerRun 514
Step 3
The UDP protocol is not reliable for exchanging data over a network, so we can configure Rsyslog to send log messages to a remote server through the TCP protocol. To enable the TCP reception protocol, we will remove the following lines:
$ ModLoad imtcp $ InputTCPServerRun 514
Step 4
This will allow the rsyslog daemon to link and listen to a TCP socket on port 514.
Both protocols can be enabled in rsyslog to run simultaneously on Linux.
If it is necessary to specify which senders are allowed access to the rsyslog daemon, we must add the following lines:
$ AllowedSender TCP, 127.0.0.1, 192.168.0.5/24, * .domain.com
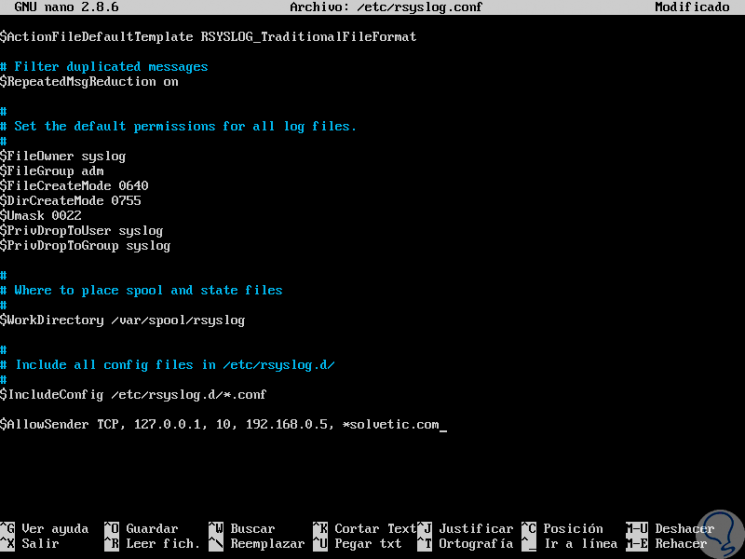
Step 5
At this point it will be necessary to create a new template which will be analyzed by rsyslog daemon before receiving the incoming records. This template should tell the local Rsyslog server where to store incoming log messages. This template will go after the $ AllowedSender line:
$ template Incoming-logs, "/ var / log /% HOSTNAME% /% PROGRAMNAME% .log" *. *? Incoming-logs & ~
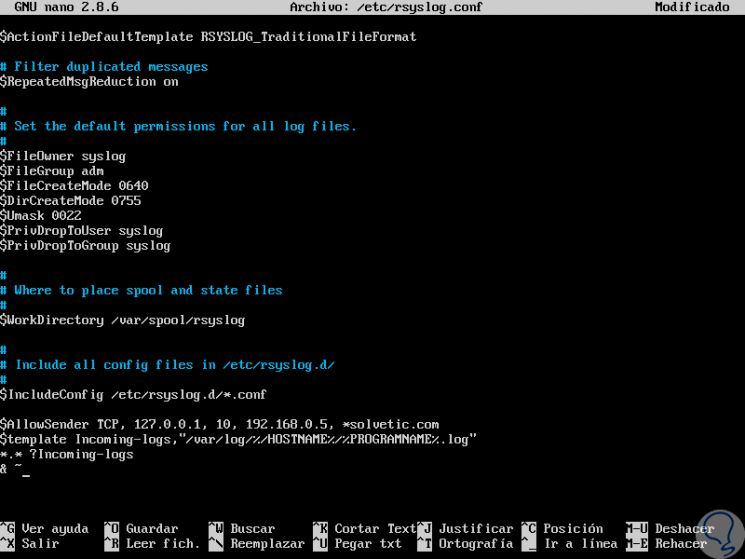
Step 6
To register only the messages generated by kern we will add the following. With the above, the records received are analyzed by the template and will be stored in the local file system in the / var / log / directory, in the path:% HOSTNAME% and% PROGRAMNAME%.
kern. *? Incoming-logs
Step 7
We can save the changes using the following key combination:
+ O Ctrl + O
We leave the editor using:
+ X Ctrl + X
3. Restart the service and verify Rsyslog ports on Linux
Step 1
When we make some type of change we must restart the service by executing any of the following options:
sudo service rsyslog restart sudo systemctl restart Rsyslog
Step 2
To check the ports used by Rsyslog we will execute the following:
sudo netstat –tulpn | grep rsyslog
Step 3
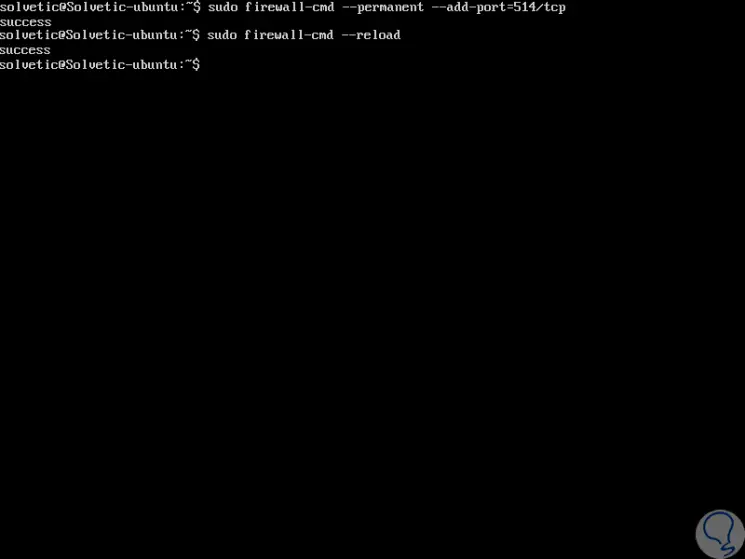
As we have indicated, the port used will be 514, we must enable it in the firewall for use with the following lines.
In RedHat and CentOS
firewall-cmd --permanent --add-port = 514 / tcp firewall-cmd –reload
In Debian
ufw allow 514 / tcp ufw allow 514 / udp
If we use IPTables:
iptables -A INPUT -p tcp -m tcp --dport 514 -j ACCEPT iptables -A INPUT -p udp --dport 514 -j ACCEPT
In this way we have installed Rsyslog on Linux for the management of the various types of records that are constantly generated in it..