SSH is a standard network tool that can be used to establish connections to remote devices - a so-called remote access. Read here how this works with Ubuntu and why the tool is so versatile. By the way: The exact meaning of the abbreviation SSH is Secure Shell.
How is SSH?
SSH, or Secure Shell, means both a network protocol and the software required for its use . The whole thing serves to establish a secure connection to another computer in the network in order to be able to operate it. An SSH server runs on the remote computer and an SSH client on your local computer . As soon as you have established the connection, you are logged into the command line on the remote computer - and can then operate it just as if you were sitting in front of it. And best of all : As " Secure " suggests, this connection is completely encrypted.
SSH enables you to remotely control "normal" computers or to work on them. For example, you could connect to a computer in the office or carry out updates on children's devices via remote access. But it is more interesting, especially for home users, for network devices that do not have their own monitor or input devices. For example, you can connect to most NAS via SSH , to Raspberry Pis and routers and here and there even to webcams, printers and the like .
While this is specifically about Ubuntu, the nice thing about SSH is that it is very universal and is available almost everywhere. Even from a smartphone or Windows, it is no problem to activate remote access to the Ubuntu computer in the basement. Or vice versa!
The result of a connection is always identical: you end up in a command line on the remote computer, logged in as one of the users there..
Establish an SSH connection
In the case of Ubuntu, SSH in the form of OpenSSH is already installed , and the server and client can be used immediately. Otherwise the installation is limited to a simple " apt-get install openssh-server openssh-clien t ". Of course, you need two computers for testing , in the simplest case two normal Ubuntu systems. The second computer can of course also be a virtual machine. Just make sure that this then has the "network bridge" as the network interface so that the VM can also be reached via the network.
Assuming the remote computer has the IP address " 192.168.178.100 " and there is a user " admin " there, establish the connection as follows:
- Open a terminal via the start menu and enter the command "
ssh [email protected] ". Since you have not yet had any contact with the server, the computers naturally do not yet "know" each other. - When you connect for the first time, you will be asked whether you really want to connect to the computer and whether you trust the displayed signature. You could now manually synchronize this signature with the server, but as long as you are connected to known, own computers, simply confirm by typing " yes ".
- You will then be asked for the password of the user " admin " - enter the normal password here that you would also use directly on the server. And with that you are already in the command line of the server. To leave this again, type " exit ".
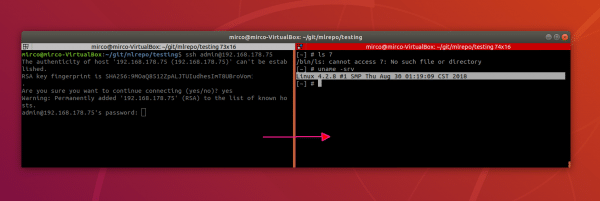 On the left the command line of the client with the login process, on the right the remote command line of the server (here a QNAP NAS).
On the left the command line of the client with the login process, on the right the remote command line of the server (here a QNAP NAS). Key authentication
You can also make the connection much more convenient and / or secure : Instead of a name-password combination, you can also use a key . The principle is actually very simple: You create a key pair on the client from a public and private key . The private key must remain secret as you can use it to unlock the door to the remote computer. The public key is basically the keyhole that you build into the door of the server. The concept is very similar to real doors: you will keep your house key "secret" as much as possible, but of course everyone can see your keyhole..
Start a command line on the client computer and then generate the key via " ssh-keygen " (for SSH key generator). First you should specify the file that will be created - just leave the default there and confirm with [Enter] . You can then enter a password in order to add an additional barrier when establishing the connection. If you omit the password, i.e. simply confirm with [Enter] , there is no password query. Ultimately, two files are created in the hidden directory ".ssh" under your user directory: "id_rsa" and "id_rsa.pub" . The "rsa" in the file name stands for the cryptography used, but you don't have to worry about it. The file extension "pub" stands for "Public", so it is the public key.
To copy this to the server, use the following command: " ssh-copy-id -i .ssh / id_rsa.pub [email protected] ". The " -i " indicates that the identity is to be copied, which means the public key specified below. It is of course copied via SSH, this time with a name-password combination. You can then establish connections using the " ssh [email protected] " command without having to enter a password (provided you did not assign a separate password when creating the key). By the way: If you ever want to run scripts that first have to establish an SSH connection, this passwordless variant is of course much more suitable.
And just to dispel all security concerns: A passwordless connection can only be established if your private, secret key is available on the client computer in the form of the "id_rsa" file.
SSH based applications
Now you could say to yourself: When do I need a command line? But SSH can do a lot more, as two really great, useful examples should show: X2Go and Xmouse . Xmouse is a clever Android app that turns the smartphone / tablet into an input device for an Ubuntu computer. You can use it to send keyboard keys remotely , manipulate windows and, above all, use the device as a touchpad , i.e. as a mouse replacement. This is great for drawing on the computer, for example, if you don't have an expensive graphics tablet. Two things are primarily at work in the background: The " Xdotool " tool runs on the Ubuntu computer ", which, among other things, can simulate all kinds of keyboard commands and implement commands from the smartphone. The actual connection is via SSH! The big advantage: You do n't have to run a special Xmouse server on the Ubuntu computer, just SSH, anyway is available by default.
 Xmouse is a clever remote control that works over SSH.
Xmouse is a clever remote control that works over SSH. The real killer argument can be found under the keyword " X11 Forwarding ". X / X11 generally stands for graphical applications under Linux - and these can also be transferred via SSH. For example, you could run an image editing program such as Gimp on the remote computer, but control it remotely. You will then simply see the Gimp window seamlessly on the local desktop. And that works on Windows too! Manually it is associated with a bit of fiddling, but the wonderful open source tool X2Go (incidentally a project from Germany) makes it easy: X2Go has to be installed on the client and server and then makes it possible to establish connections via a very simple graphical user interface, which can either display individual programs or the entire desktop of the remote computer on the local monitor.
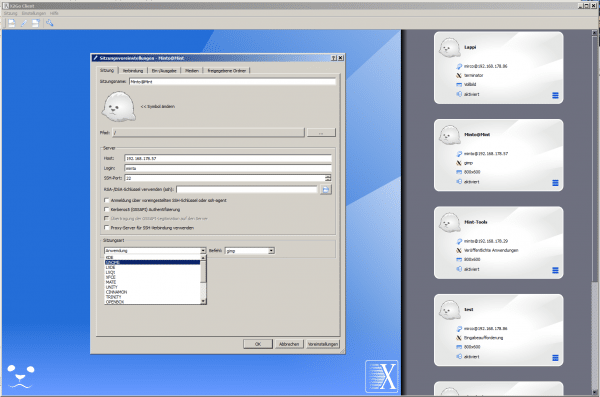 With X2Go you can display entire remote desktops in the window.
With X2Go you can display entire remote desktops in the window. What is the difference between SSH and OpenSSH?
If you deal with the topic of SSH, you will come across the keyword "OpenSSH" relatively quickly. What sounds very similar is also very similar - but different. When SSH was developed it was originally an open source project. However, a company was founded from this, so that the original SSH-1 protocol was quickly privatized more and more. So that SSH remains freely usable for everyone, the Internet community has developed OpenSSH based on the original protocol.
SSH-1 is now obsolete, so SSH-2 was developed. The open source community has also worked on OpenSSH, so there are now these two competing products. OpenSSH is in the public domain and can be used free of charge, but only has support from the Internet community in the event of errors or questions. SSH-2 is chargeable, but because it is marketed by the company, it has a corresponding 24-hour support and is therefore much more suitable for companies.