One of the most used protocols over time for everything related to remote connectivity has been SSH which has its origins since the year 1995 offering a secure access method from an external network where vulnerabilities are so common. Every day we can see how new threats are created, new types of attacks and although we do not have or store extremely sensitive information we can be victims of attacks such as the one that happened a few months ago, WannaCry, where thousands of computers were infected and their information “hijacked†and for whose release amounts of money were required..
Regardless of the type of users we are, we must know that the SSH protocol was created with the objective of granting secure access permissions to our macOS Mojave system and thus guarantee that only the authorized user (s) can have such accessibility from anywhere.
Through this tutorial TechnoWikis wants to explain in detail what it is and how to implement SSH in macOS Mojave..
What is SSH?
SSH (Secure Shell), was established as a software package through which secure system administration and file transfers are allowed through insecure networks such as our current networks, the utility of SSH is so broad that today It is used in multiple data centers and in thousands of companies worldwide.
The SSH protocol makes use of special encryption in order to ensure the connection between a client and a server, thus, all authentications of both users, commands, results and file transfers are always encrypted in order to protect all these elements. against attacks on the network.
When using SSH there are several alternative options in order to obtain a solid authentication, and there are benefits such as improving the security and integrity of communications using strong encryption. SSH is positioned as a secure alternative to unprotected login protocols such as telnet or insecure file transfer methods such as FTP.
The SSH protocol is implemented in special situations such as:
- Provide secure access for users and automated processes in companies
- Perform file transfers interactively and automatically
- Being able to execute remote commands
- Manage the network infrastructure and other components of the mission-critical system in a centralized way regardless of where we are.
SSH operation
It is important to know in detail how SSH really works since this way we can know well what we are installing and everything that happens internally when connecting using this protocol. The SHH protocol works based on the client-server model, with which the connection is established by the SSH client that connects to the SSH server.
After this connection, the SSH client redirects the connection configuration process and makes use of public key cryptography in order to verify the identity of the SSH server and verify that everything is within the correct parameters, then this, the protocol SSH is responsible for taking strong symmetric hash and encryption algorithms in order to guarantee the privacy and integrity of the data that will be transmitted between the client and the SSH server..
When we talk about security, there are several options that we can implement for user authentication, with passwords and public key authentication being the most used, so that SSH uses the public key authentication method which is mainly used as a security base. for automation or unique logins.
Automatic secure shell (SH) file transfers can be used to integrate applications and also to create automated systems and configuration management in a simplified but completely comprehensive way with the best security features.
Once a correct connection between the SSH client and the server has been established, the data that is transmitted through these channels will be encrypted based on the parameters negotiated in the configuration and, during this negotiation, the client and the server arrive to an agreement on the symmetric encryption algorithm to be used and based on that the encryption key to be used will be generated.
Traffic between these channels is always protected with industry-standard encryption algorithms such as AES (Advanced Encryption Standard), and the SSH protocol also includes a special mechanism that guarantees the integrity of the transmitted data using standard hash algorithms such as the already known SHA -2.
SSH Outstanding Features
Apart from the great benefits we have mentioned about SSH, some of its features are:
- Strong cryptography using algorithms such as AES, ChaCha20, RSA, ECDSA, Ed25519 and many more
- Supports X11 forwarding which also encrypts X Window System traffic
- Port forwarding which allows the forwarding of TCP / IP connections to a remote computer using an encrypted channel. Strong authentication including public keys, single-use passwords and more, thanks to which it is protected against various security flaws such as IP and identity impersonation, DNS impersonation and more. Several authentication methods are supported with SSH such as public key authentication, single-use passwords with s / key and authentication using Kerberos.
- Interoperability between implementations
- Agent Forwarding, which is useful for using an authentication agent that runs on the user's device in order to maintain the authentication keys of that particular user. SSH is responsible for automatically resending the connection to the authentication agent using any type of connection without the need, insecure, to host the keys on the local computer
- Full SFTP support is available, using the sftp command as a client and the sftp-server subsystem as a server
- Optional data compression which improves the performance of network links with low speed.
1. How to verify SSH in macOS Mojave
The first action we must take is to verify that the SSH protocol is not enabled in macOS Mojave. To perform this check, we must access the terminal using one of the following methods:
- Using the key combination ⇧ + ⌘ + U and in the displayed window we select Terminal
- On the route Go / Utilities / Terminal
- Using Spotlight, there enter the terminal and choose the respective utility.
In the terminal we will execute the following to validate the SSH status in macOS Mojave:
sudo systemsetup -getremotelogin
We enter our password and this will be the result.
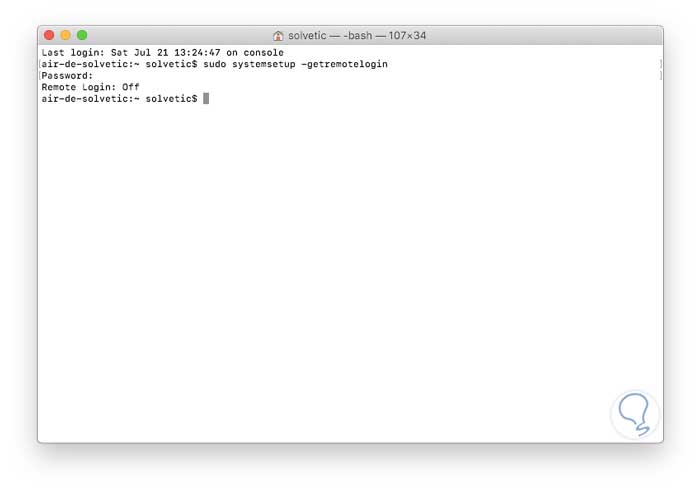
We can see that by default this protocol is disabled. For its activation, we will use the parameter -setremotelogin thanks to which it will be possible to define and enable remote access via SSH to Mojave, for this we execute the following line:
sudo systemsetup -setremotelogin on
As such, this command does not return any results so that we run sudo systemsetup -getremotelogin again to verify that SSH activation has been performed. We can see that his status is now On.
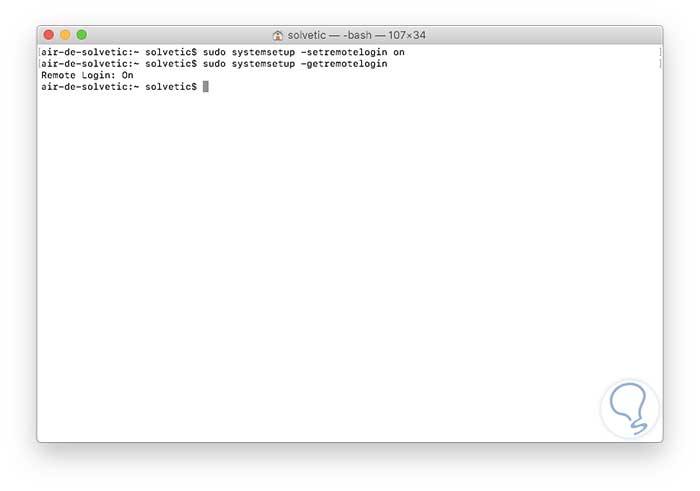
2. How to enable the user to access macOS Mojave via SSH
Step 1
With SSH enabled in the system, the next step is to enable access to users who have credentials on the computer, for this we will use the syntax with any of them:
ssh username @ ip_equipo
We must know in detail the name of the users to authenticate and to obtain the IP address of the device we will use one of the following options:
From the terminal executing the ifconfig command:
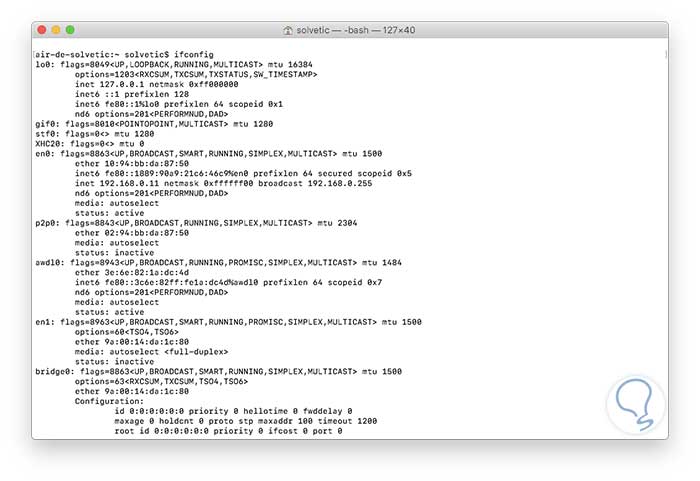
Step 2
From System Preferences / Network:
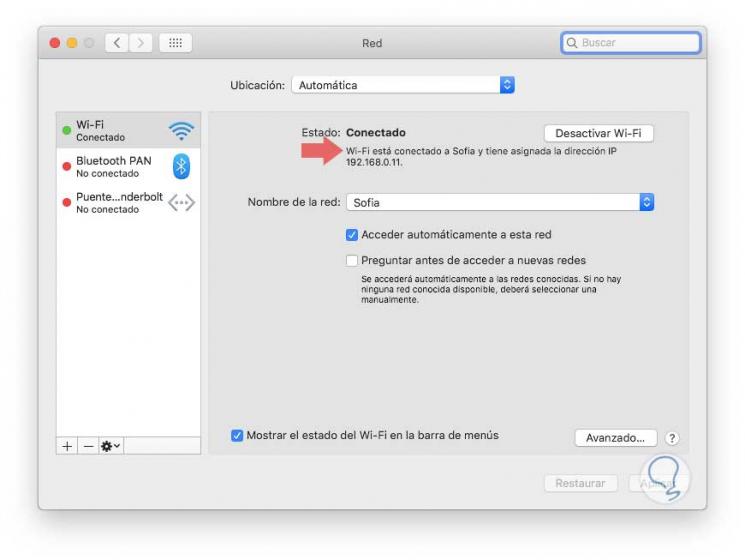
Step 3
Now, knowing the IP address, we will enable the desired user, in this case the solvetic user, by entering the following:
ssh [email protected]
Once we carry out this process, the user will have access to the equipment and in case of being an administrator user must provide the respective access credentials:
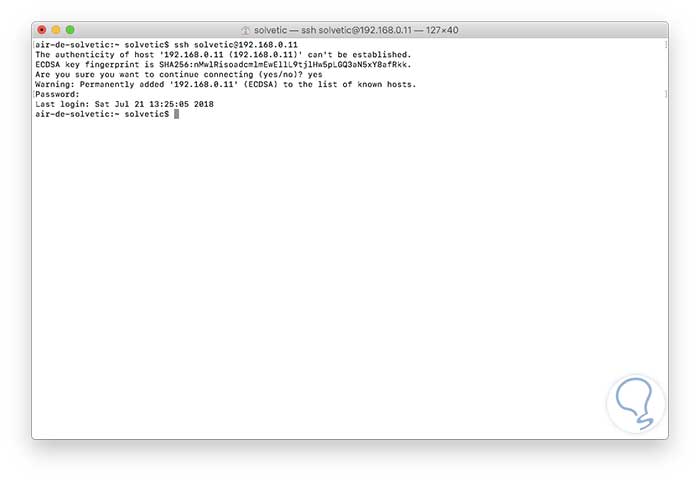
As we see, it is required that we enter yes when asked if we want to establish the connection.
In this way the user will have access using SSH to macOS Mojave.
3. How to access macOS Mojave externally
Step 1
The next step is to validate that the remote connection to macOS Mojave works as expected, for this we will use an SSH client called Putty which is available at the following link:
Putty
Once we execute it, we must configure the following:
- In the Host Name (or IP address) field we define the IP address of the macOS Mojave device
- The default Port field is 22 and is left as is
- The connection type in the Connection Type field must be as SSH
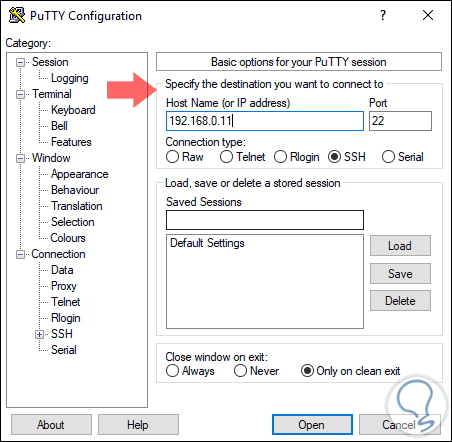
Step 2
Click on the
Open button and the following security warning will be displayed:
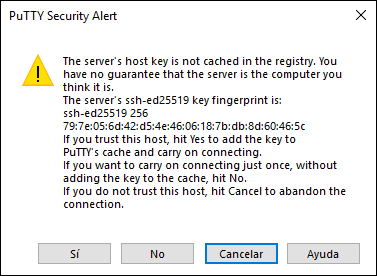
Step 3
There as we see the password assigned for the connection is reflected, click on the
Yes button and now we will enter the credentials of the selected user:
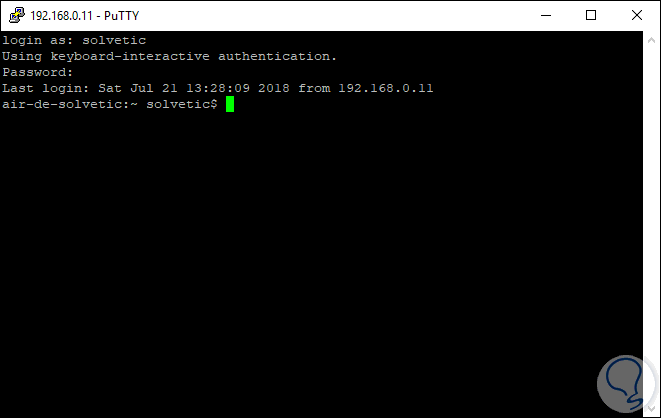
Note
In this case we are connecting from Windows 10.
Step 4
By accessing SSH through Putty, we can list libraries:
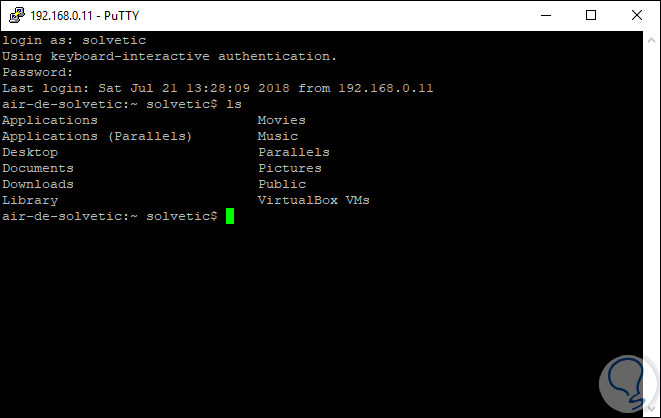
Step 5
It will also be possible to access content within macOS Mojave:
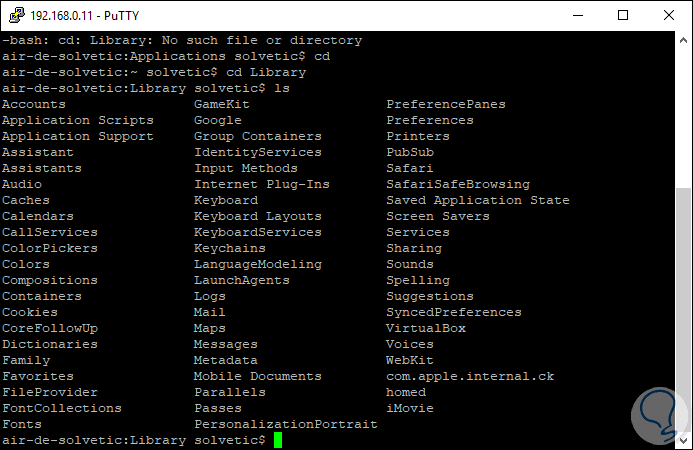
4. How to disable SSH in macOS Mojave
At the moment in which we consider that it is not necessary to use SSH for connections in Mojave, we can proceed to disable it, for this we execute the following in the terminal:
sudo systemsetup -setremotelogin off
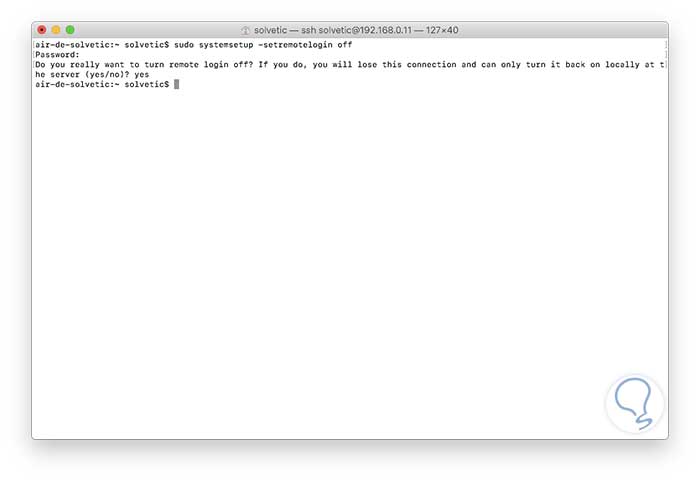
Enter yes to confirm the disabling of SSH. Thus, SSH, either locally or remotely, allows us to access the equipment and carry out support or administration tasks as if we were there:
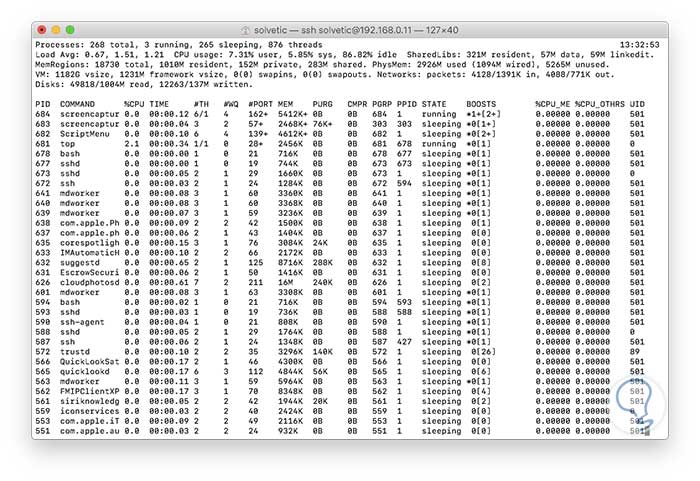
This way you will know how to activate and use SSH in macOS Mojave.