The security, privacy and confidentiality of the information that is transmitted through the network should always be one of the actions to take care of with more responsibility since in the world-wide network there are millions of threats that can jeopardize the integrity of this information and even more, of our daily tasks on any type of equipment. There are several solutions to improve security during browsing, but one of the most traditional and used is to configure and make use of VPN networks..
What is a VPN?
VPN (Virtual Private Network) is a technology that prevents everything we do on the network from being vulnerable to any type of spying since it is anonymously browsed, with a VPN network it will be possible to create a local network without We are forced to make the computers that make up this network physically connected to each other, hence their virtual name.
To increase browsing security, all the network traffic used will go from our device to the Internet provider, but from there it is automatically redirected to the VPN server , which guarantees anonymity fully since the IP address that is reflected is that of the VPN provider but not that of our team.
The use of VPN networks can be implemented for reasons such as:
- Access sites with geographical restrictions
- Avoid the history that various companies use when browsing the Internet
- Add security enhancements
- Being able to perform P2P downloads
- Compatibility with various desktop and mobile operating systems
Now, at the VPN level, we can increase your security even more thanks to Tor which gives us practical solutions to be totally sure that our connection is 100% secure. TechnoWikis will explain how to configure a VPN in Windows 10 and then use the Tor browser to protect all information sent and received during the session..
Before we begin, we must clarify the reason why we must first connect to the VPN and then use Tor, the simplest reason is for configuration issues since it is more complicated to carry out the tunnel configuration process through the Tor network and then connect from there to the VPN provider.
What is Tor
Tor is a network where a group of servers are integrated, whose key objective is to improve privacy and security when using the Internet. Users who use Tor will connect through a series of virtual tunnels instead of the classic direct connection, which allows information to be shared through public networks without compromising their privacy.
Tor can also act as a tool to avoid censorship, allowing users to access blocked destinations or content but at this point TechnoWikis advises to follow the guidelines of each country at the level of justice so as not to violate any law that may affect the navigation. With the Tor network, a building block can be implemented so that software developers are able to create new communication tools focused on integrated privacy ..
Tor's services allow users to publish websites and other services without being forced to reveal the location of the site , as well as access to social networks in public places where security is much more vulnerable. Tor was created to avoid the so-called traffic analysis which is used to access who is talking to who in a public network, hence security is critical in this type of networks, and this type of analysis can seriously affect the Privacy of a person and is also used to send promotions about tastes and preferences.
To understand a little how this traffic analysis works, we must understand that Internet data packages are composed of two parts that are:
- A header that is used for routing.
In summary, the data payload is the information sent, such as an email message, a web page, etc., and even if we encrypt this data payload, traffic analysis can access this information thanks to the header, which reveals the origin, destination, size, time and more data of the information sent.
To avoid this, Tor is responsible for distributing all transactions in various places on the Internet, so that no point is directly linked to the destination since the data packets in the Tor network choose a random route in order to avoid detection the point of origin
When we use a VPN network together with Tor, the software or the client of the user is responsible for incrementally constructing a circuit of encrypted connections using the relays of the network, so that no individual relay can know the complete route that a user has taken. specific data package.
features
Within the characteristics of Tor we have the following:
- SSH Tunnelling Socks Proxy
1. How to set up a VPN network
Step 1
We can use the VPN network integrated with Tor which is OpenVPN, for this we must go to the following link:
VPN Tor
Step 2
Once there, we will create our account and be redirected to the next window. There we click on the "Free VPN" button
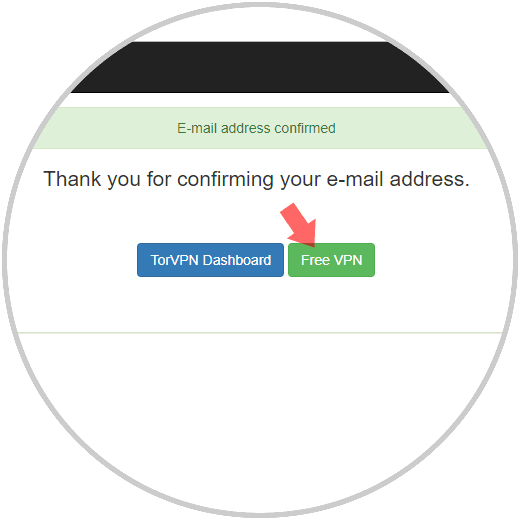
Step 3
In the next window we will enter the captcha and click on the "Give Me Free Access" button
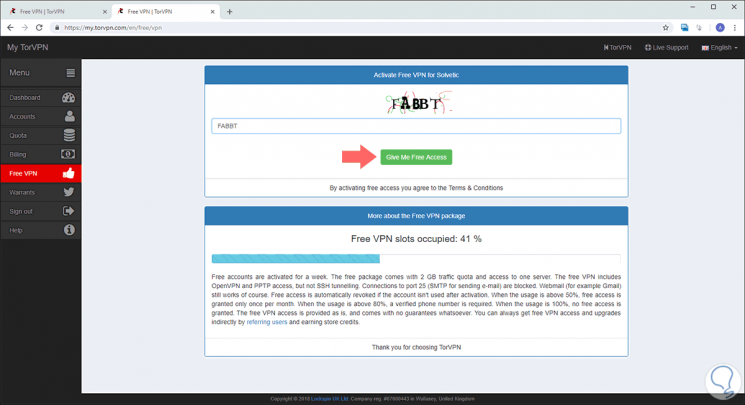
The following will be displayed:
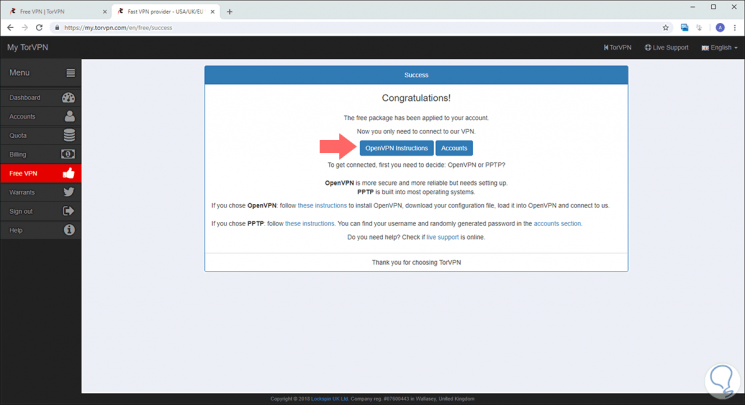
Step 4
As we can see, OpenVPN is available as a VPN network to use, there we click on the "OpenVPN Instructions" button to be redirected to the following window:
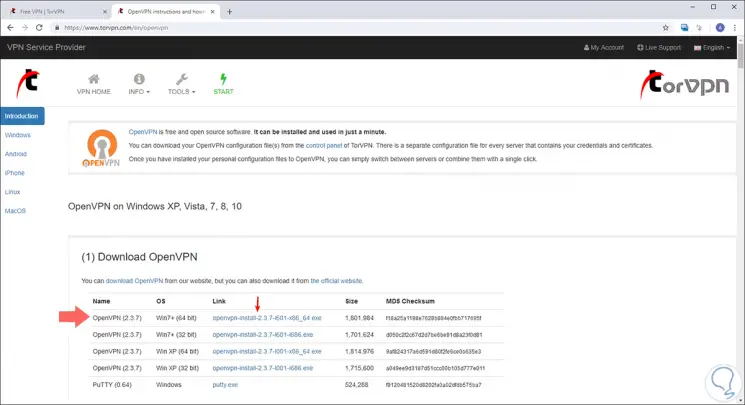
Step 5
There we proceed to download the executable and once we download it, the following wizard will be displayed. Click on "Next"
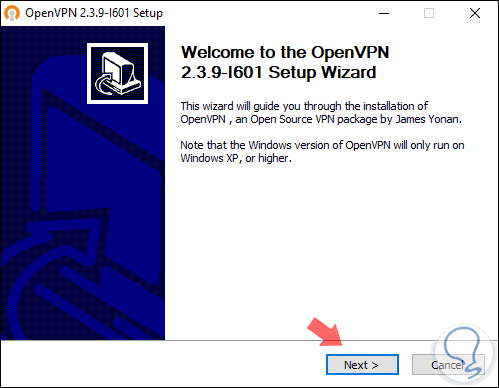
Step 6
Next we will accept the license terms: Click on the "I Agree" button
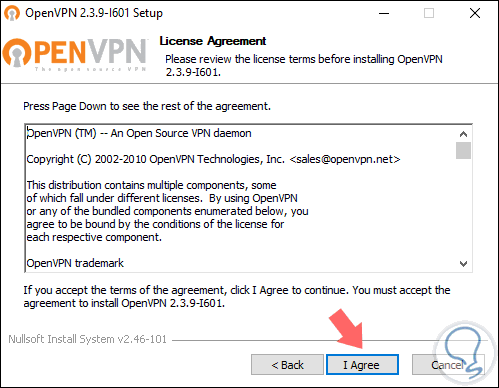
Step 7
We will see the OpenVPN components to be installed:
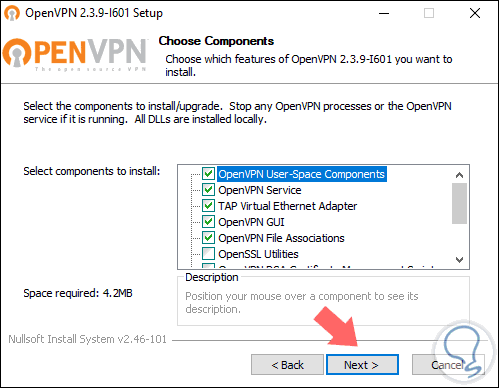
Step 8
Click on "Next" again and the OpenVPN installation process will begin:
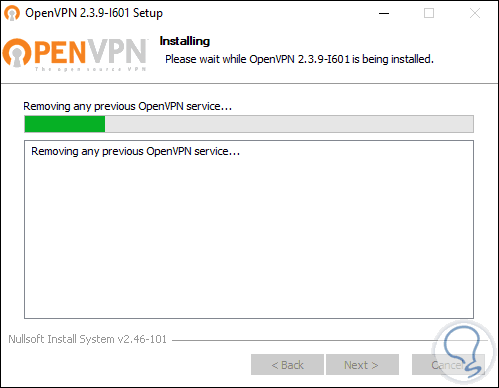
Once finished we will be able to access it, this OpenVPN network has some restrictions for which they recommend updating to the Pro version.
2. How to download and use TunnelBear
If you do not want this, we can use TunnelBear which is available for free at the following link:
Bear tunnel
features
Some of the features of TunnelBear are:
- Integration of the Watch mode which allows, if the connection is interrupted, that TunnelBear blocks all unsecured traffic until we establish the secure connection again.
- It automatically connects to the nearest tunnel to avoid wasting time.
- Possibility to set the automatic start to always be connected.
- TunnelBear does not record any activity of clients connected to this VPN network.
- We have 500 MB per month for free.
Step 1
For its installation we execute the downloaded file and once installed the following will be displayed:
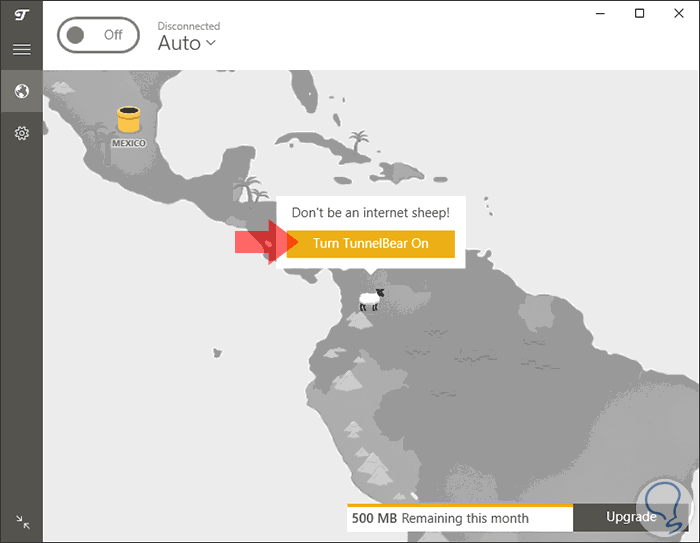
Step 2
There we click on the "Turn TunnelBear On" button to start the VPN connectivity process:
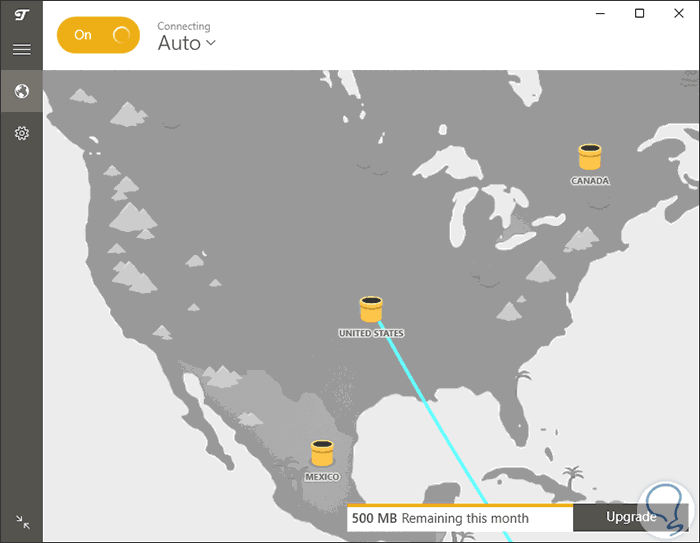
Step 3
Once connected we will see the following. Thus we have connected to the VPN network.
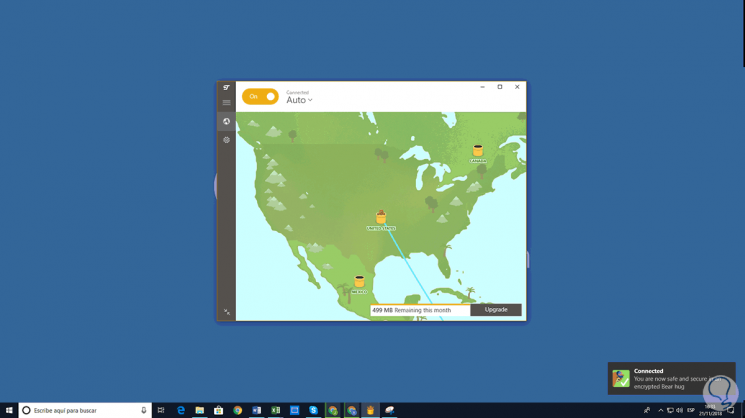
3. How to use and install Tor Browser
The Tor browser, Tor Browser, is responsible for protecting all Internet traffic when it is run, so Tor will only protect applications that are configured to send your Internet traffic through Tor. This Tor browser gives us the opportunity to use Tor on Windows, Apple MacOS or GNU / Linux without the need to install any additional software.
Your download is available at the following link:
Tor Browser
Some actions are recommended when using this browser such as:
- Do not enable or install add-ons
- Validate that the connection is HTTPS
- Do not open downloaded documents online
Tor nodes
Tor acts as a group of layered proxy servers which route zigzag traffic around the Internet before it reaches the final destination, for which 3 nodes are used:
- The entry node which knows the IP address of our equipment.
- The central node which prevents the output node from detecting which input node has been used in order to collate the origin point.
- The exit node which knows which site the connection is being established, but without revealing our identity.
The Tor browser, Tor Browser, is based on Firefox and has been optimized for information security and privacy.
Step 1
Once the Tor Browser executable is downloaded, we proceed to its execution and the following window will be displayed where we will define the language to use:
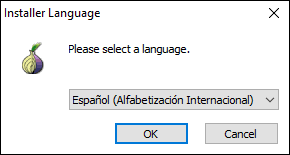
Step 2
Click on "Ok" and now define where the Tor browser is to be installed:
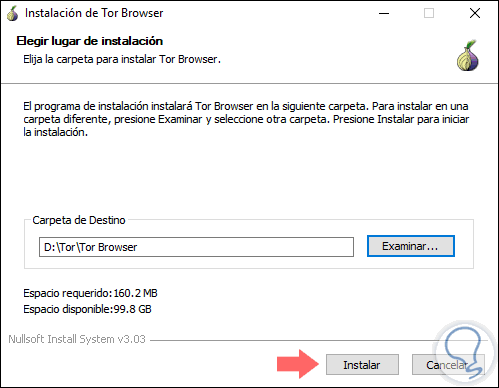
Step 3
Click on the "Install" button to start the Tor installation process:
Step 4
Once this process is finished we will see the following:
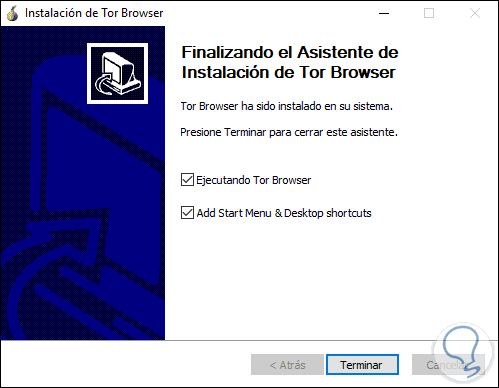
Step 5
There it will be possible to run the Tor browser or create the shortcuts. Once the browser opens we will see the following:
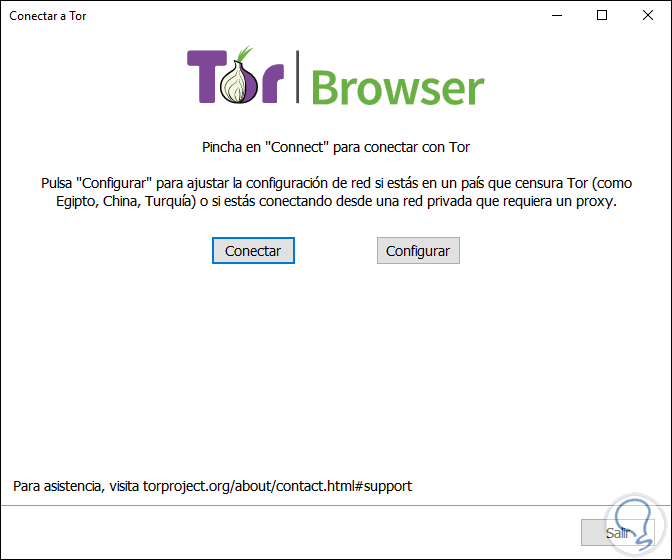
Step 6
There we see the options as we will connect to the browser, there we select the most appropriate option, in this case as we have connected to the VPN network click on "Connect"
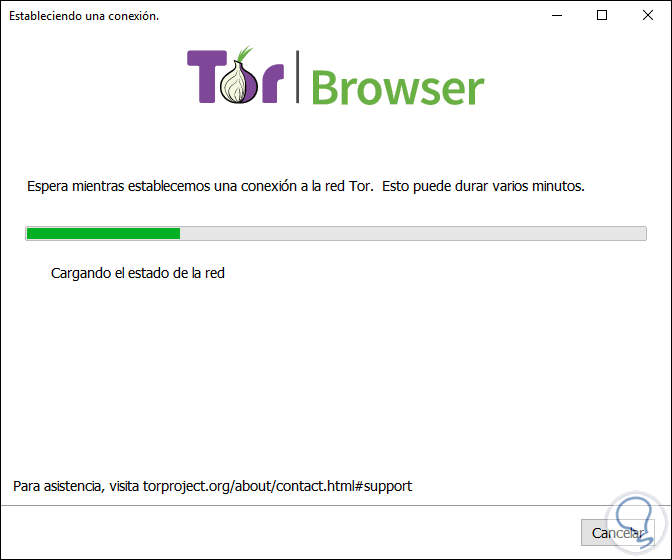
Step 7
Once the connection is established we will access the Tor browser through a VPN network:
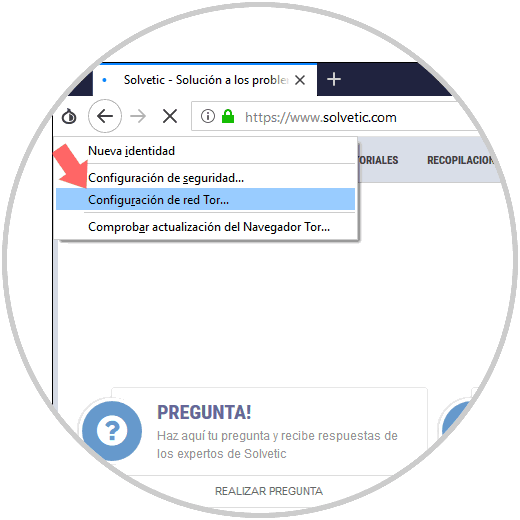
Step 8
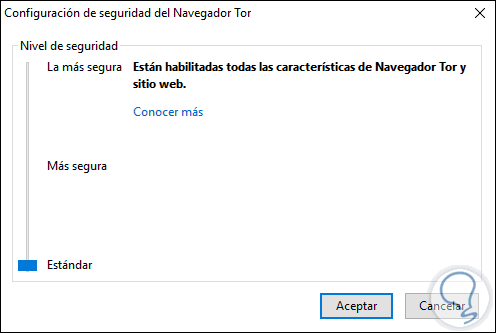
There we can configure some security parameters if necessary through the option "Security Settings"
Step 9
We can also configure the Tor network based on current needs:
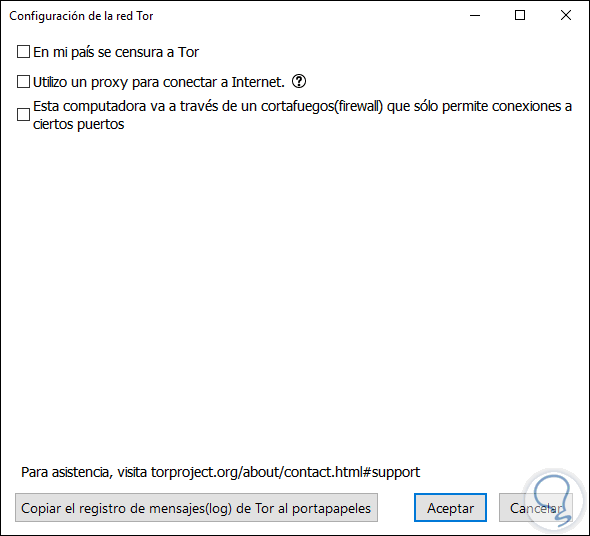
Step 10
To check the VPN network, we can go to the following link and click on the Start Test line:
VPN validation
In the results, we can see the assigned IP address, as well as the current location of this on the computer:
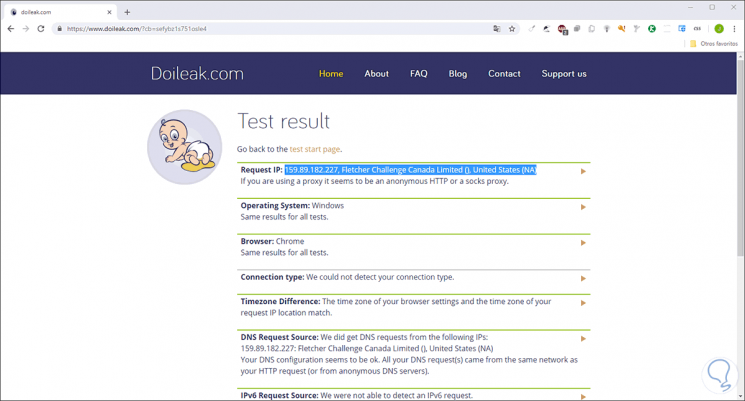
As we can see, thanks to the integration of VPN with Tor it will be possible to ensure maximum browsing our network and thereby improve privacy levels.