Information security is one of the most important tasks that we must manage today because with the constant threats both internally and externally, information will always be susceptible and vulnerable to falling into the wrong hands..
There are several methods available to protect the information , from hosting the data in the cloud to establishing strong Firewall rules but we can choose practical, reliable methods with different security options . One of them is to encrypt and set a password for our devices and in this case TechnoWikis will talk about USB media, which are more vulnerable to be attacked anywhere. To avoid this we must encrypt its content and assign a password , only the user of said USB will have access to it. We will learn to use LUKS together with Cryptsetup for it.
What is LUKS and Cryptsetup
Cryptsetup is a utility whose purpose is to comprehensively configure disk encryption directly in the DMCrypt kernel module. Cryptsetup includes volumes of plain dm-crypt, volumes LUKS, loop-AES and TrueCrypt format with which the security options are wide, in addition to this, the utility veritysetup is included which is used to configure the kernel verification modules of DMVerity block integrity and as of version 2.0, integrity is added for the DMIntegrity block integrity kernel module configuration.
LUKS (Linux Unified Key Setup) is a standard designed for hard disk encryption in Linux environments. Thanks to LUKS, a standard disk format is offered that facilitates compatibility between the various distributions, but also allows secure password management for multiple users. LUKS stores all the necessary configuration information in the partition header, this makes it easy to transport or migrate data in a complete and trouble-free way..
LUKS advantages
Some of the advantages of using LUKS are:
- compatible through standardization.
- safe against attacks of all kinds
- support for multiple keys
- allows you to execute the effective revocation of the passphrase and more.
LUKS is able to manage multiple passwords, which can be effectively revoked and protected against dictionary attacks with PBKDF2.
1. Functions and syntax of LUKS, Cryptsetup
Some valid actions when using LUKS are:
Start LUKS partition
This option initializes a LUKS partition and sets the initial key, either through manual parameters or through a key file.
luksFormat <device> [<key file>]
With this parameter we can add <options> as:
[--cipher, --verify-passphrase, --key-size, --key-slot, --key-file (takes precedence over the second optional argument), --keyfile-size, - random use | --use-urandom, --uuid].
Open option
luksOpen <device> <name>
This option opens the LUKS partition <device> and configures a mapping <name> after the verification has been successful with the indicated key. With this parameter we can add <options> as:
[--key-file, --keyfile-size, --readonly]
Close option
It fulfills the functions of the "remove" parameter.
luksClose <name>
Suspend option
This parameter suspends the active device (all IO operations will be inactive) and proceeds with the deletion of the kernel encryption key. Kernel version 2.6.19 or later is required for this, after this operation, it will be necessary to use luksResume to reset the encryption key and resume the device or luksClose to remove the assigned device.
luksSuspend <name>
Addkey option
luksAddKey <device> [<new key file>]
This option adds a new key file or passphrase, for this you must provide a passphrase or password file, some of its options are:
[--key-file, --keyfile-size, --new-keyfile-size, --key-slot]
Additional LUKS parameters
Some additional parameters to use with LUKS are:
- Delete the supplied key or the LUKS device key file
luksRemoveKey <device> [<key file>]
- Print the UUID of the selected device
luksUUID <device>
- Dump the header information of a LUKS partition.
luksDump <device>
Additional Cryptsetup Parameters
Now, Cryptsetup handles the following syntax:
cryptsetup <options> <action> <arguments>
The options available with Cryptsetup are:
- Rename an existing mapping.
remove <name>
- Generate the state of the mapping.
status <name>
- Modify an active assignment.
reload <name>
- Resize a current mapping.
resize <name>
Now we will see how to install Cryptsetup and make use of this utility together with LUKS to protect USB devices and for this we will use Ubuntu 18..
2. Install and configure Cryptsetup and the USB media in Ubuntu Linux
Step 1
For the installation of the utility, we access the terminal and there we execute the following:
sudo apt-get install cryptsetup
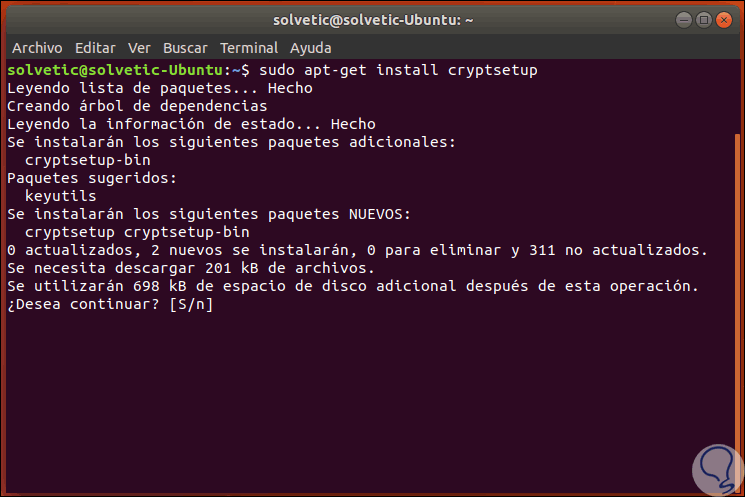
Step 2
Enter the letter S to confirm the download and installation. After this, we access the disk utility through the Ubuntu 18 search engine:
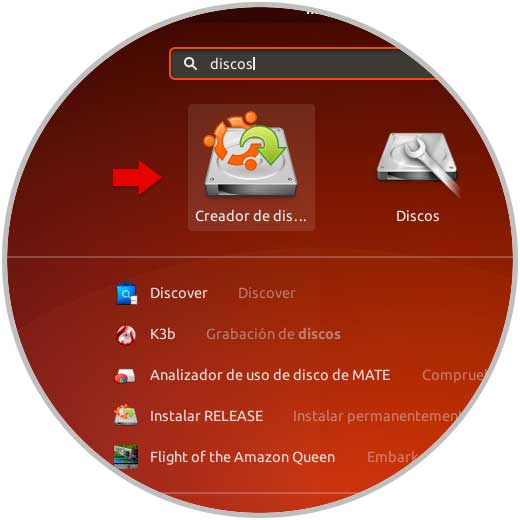
Step 3
Select "Disks" and in the window displayed select the USB media connected to the device:
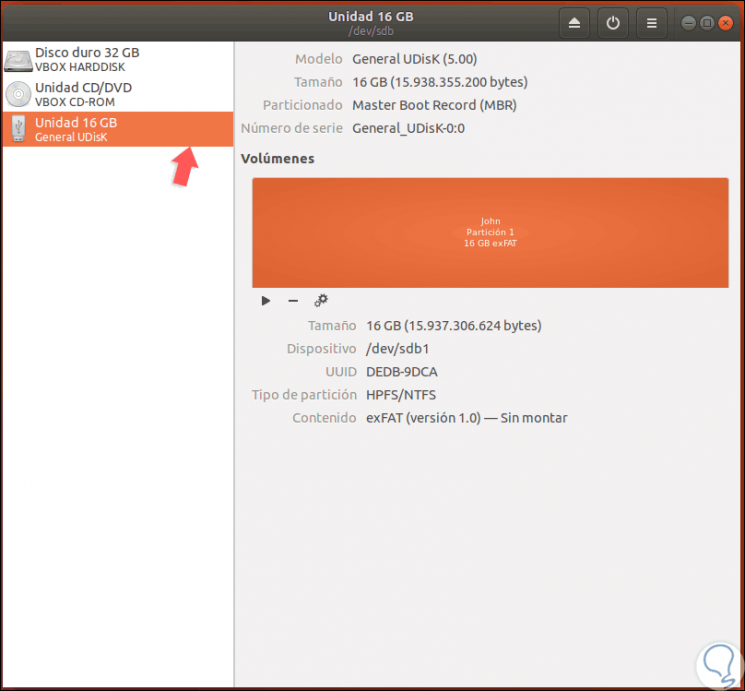
Note
In case the USB is mounted, it will be necessary to disassemble it to successfully execute the encryption operation.
Step 4
Now, click on the pinion icon at the bottom and in the options displayed select “Format partitionâ€:
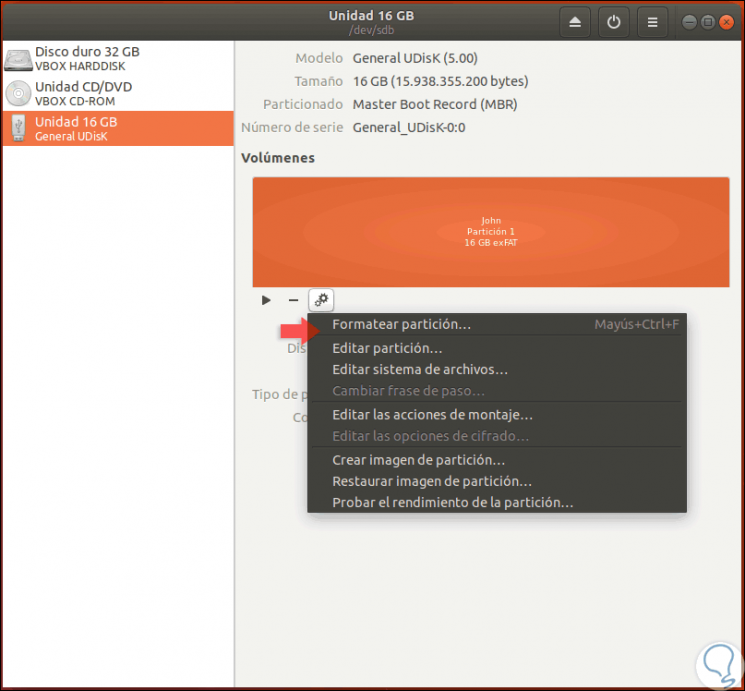
Step 5
The following window will be displayed where we must configure the following parameters:
- In the "Delete" field we can select whether or not we overwrite existing data.
- In the “Type†field, we must select the option “Encryption, compatible with Linux systems (LUKS + Ext4)†in order for LUKS security policies to be applied.
- We enter and confirm the password for the USB.

Step 6
Once this is defined, press the “Format†button and the following warning will be displayed:
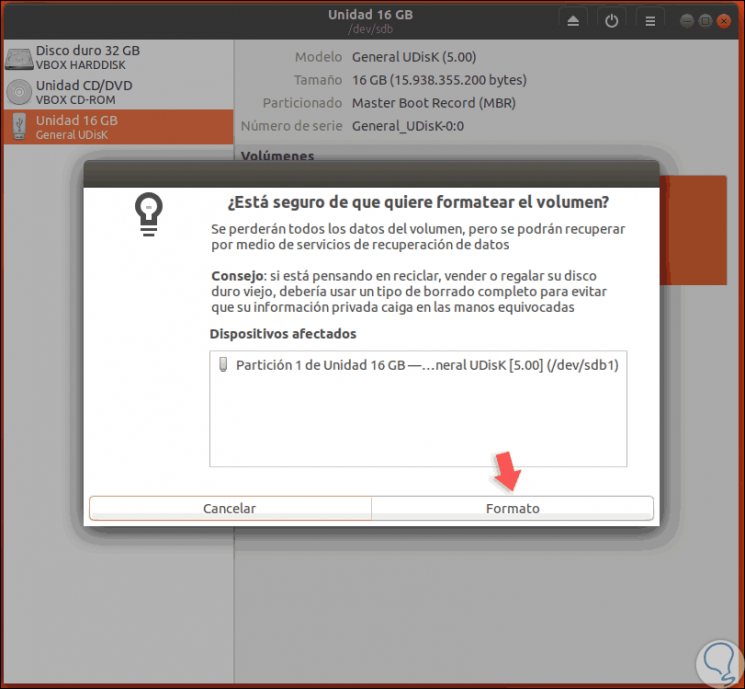
Step 7
There we confirm the action by clicking on the “Format†button again and we will see that the USB format process starts:
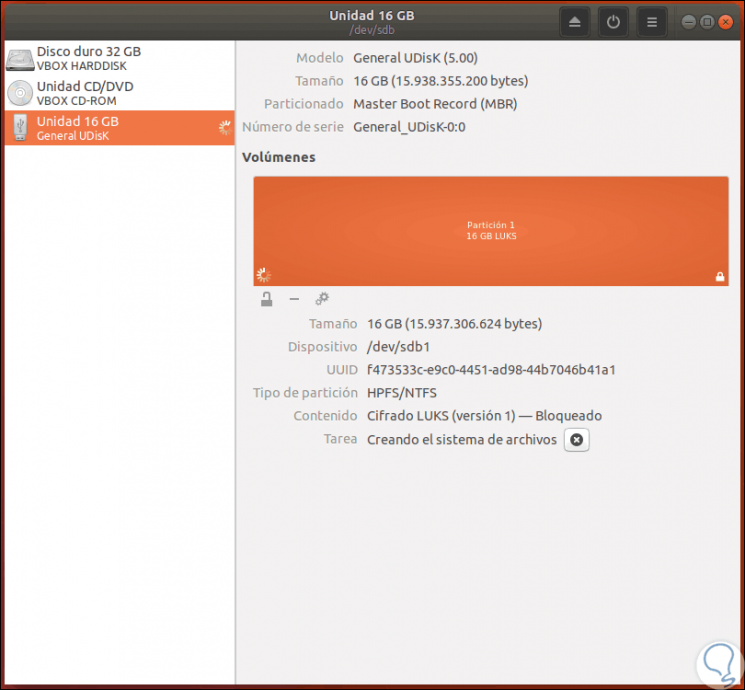
Step 8
Once this process is finished, we disconnect and reconnect the USB device back to the computer and when trying to access it the following window will be displayed. There we enter the password that we have assigned in the formatting process and click on the “Unlock†button to access the media content.
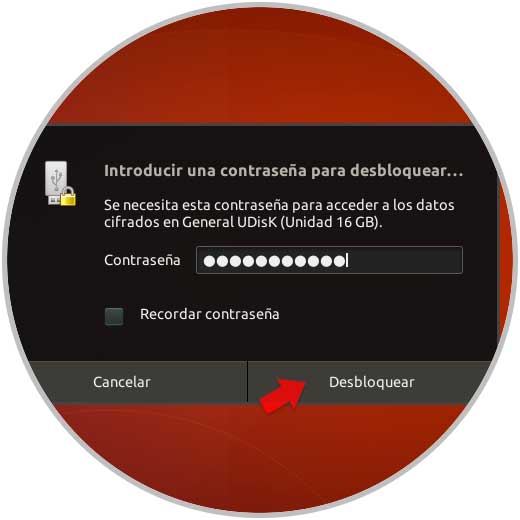
Step 9
To verify that the USB is protected, we can see a lock icon in the lower right corner of the media access:
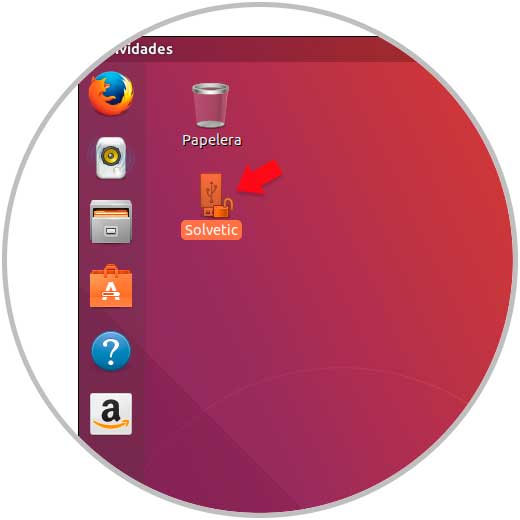
Step 10
Now, at the moment we want to modify the LUKS password, we must go back to the Disks utility and there click on the gear icon and this time select the option “Change pass phraseâ€:
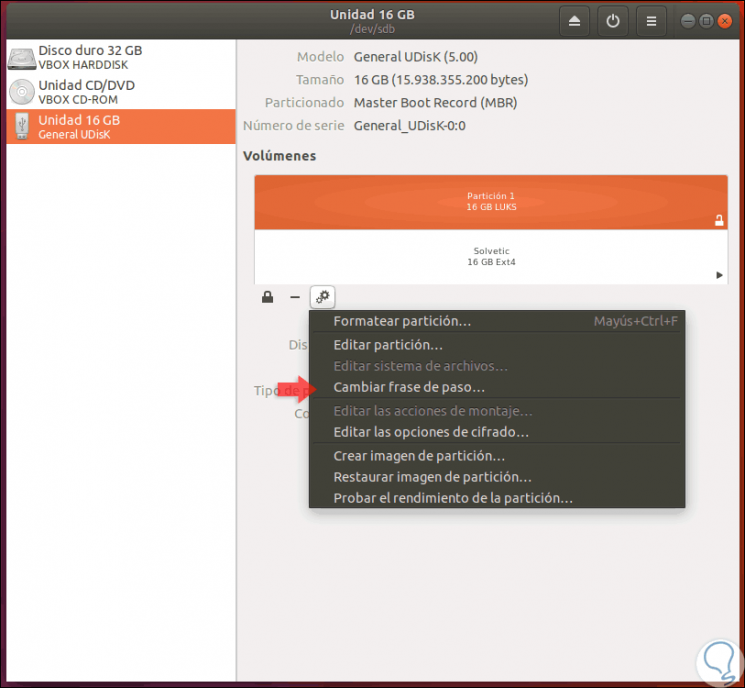
Step 11
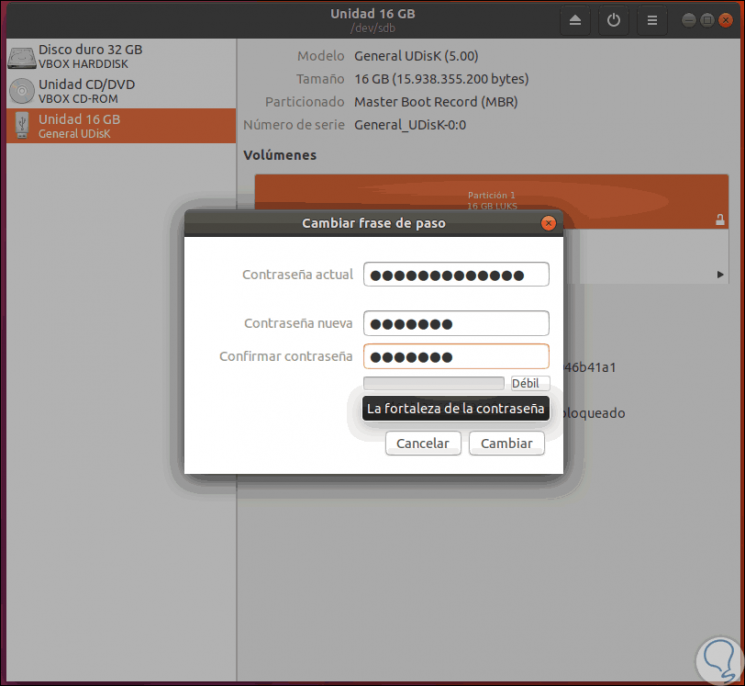
When you do this, in the pop-up window we will enter the current password and the new one to assign. Click on "Change" to complete the process. In this graphic way we have the opportunity to encrypt and password protect the desired USB media.
3. Use LUKS and Cryptsetup through command console in Ubuntu Linux
Step 1
Another option to use these tools is through the terminal, so, to encrypt and add password to a USB device we must execute the following:
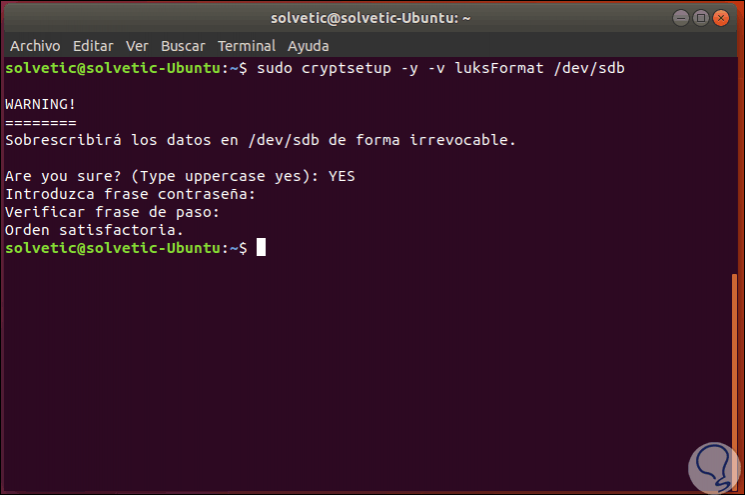
cryptsetup -y -v luksFormat / dev / sdb
Note
We must change / dev / sdb for the path of the USB medium to protect.
Step 2
Pressing Enter, we must enter the term YES to conform the action and set the respective password:
Step 3
This command will initialize the volume and establish an initial key or passphrase, it is important to note that the passphrase is not recoverable, now, we execute the following command to create an assignment:
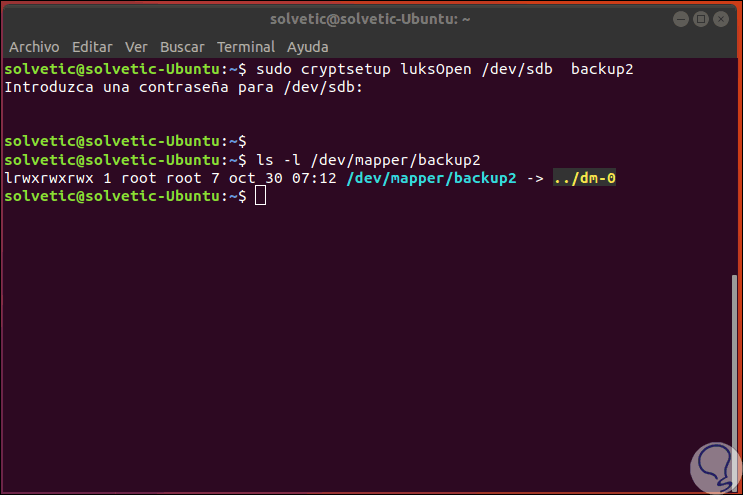
sudo cryptsetup luksOpen / dev / sdb backup2
Step 4
There we must enter the password, after this it will be possible to see the assignment name / dev / mapper / backup2 when the verification has been successful with the luksFormat command, to see these details we execute:
ls -l / dev / mapper / backup2
Step 5
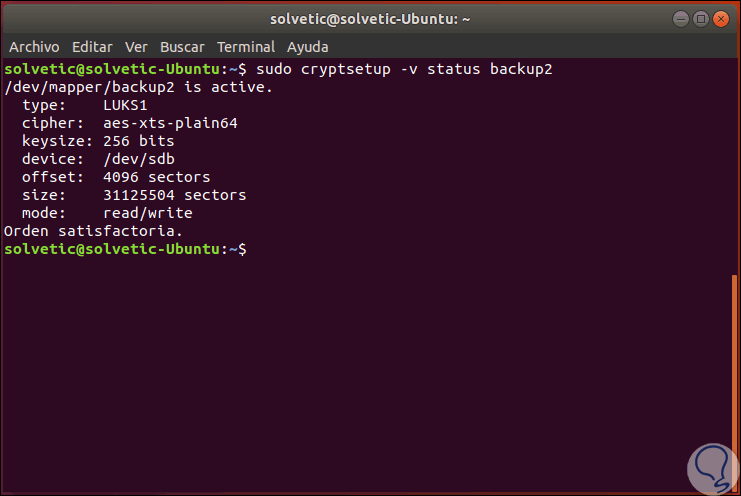
If we want to see the encryption status we execute the following:
sudo cryptsetup -v status backup2
Step 6
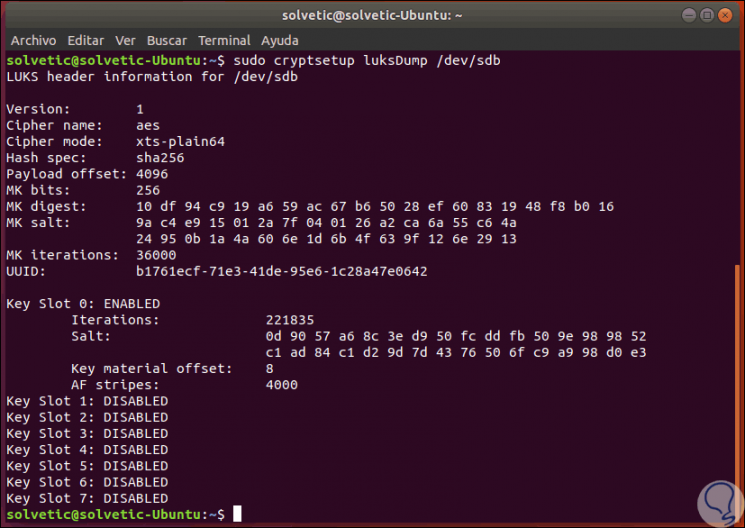
There we find details like. If we want to dump the LUKS headers, we must use the following command. There we will see much deeper details about encryption.
sudo cryptsetup luksDump / dev / sdb
We can see the different options to protect and encrypt a USB device in Linux and thus add another layer of security which will never be left over.