The security of Linux information is a key aspect that thousands of users since many of the data we handle daily are classified as confidential and if they fall wrong hands simply be in trouble privacy..
Nowadays the information methods have advanced a lot and some of the platforms that we use for this offer us special security protocols, but in view of the fact that almost by default the data is housed in the cloud, these can be a factor of risk as the cloud is global. While it is true that it allows us to access this data from anywhere, it also implies that if the correct security measures are not in place, simply a person with the appropriate tools can violate the cloud and access our data.
We can protect Linux data from the access to the account such as the physical devices where the information is hosted, but without a doubt one of the most effective methods is to encrypt the data to prevent access, and this is no longer like a few years ago where we should have been. encrypt the entire hard drive, it is now possible to reduce this task to encrypting only portions or a specific object..
To help us with this task we have Gocryptfs and TechnoWikis will explain how it works and what this utility is about.
To stay up to date, remember to subscribe to our YouTube channel! SUBSCRIBE
1. What is Gocryptfs and use of parameters
Gocryptfs makes use of a file-based encryption system which is implemented as a mountable FUSE file system, this allows each of the files in Gocryptfs to be stored in an encrypted file on the hard drive. The files that are encrypted with this utility can be stored in different folders on the hard drive, on a USB memory or within the Dropbox folder if we wish.
One of the advantages of using Gocryptfs is that since this is a file-based encryption system and not with the disk encryption method, it is that each of the encrypted files are able to be synchronized much more comprehensively when using utilities such as Dropbox or rsync. Gocryptfs is based on EncFS and allows to improve security, as well as to deliver optimal performance in the tasks that are required..
Gocryptfs ciphers
Gocryptfs offers us encryption like:
- GCM encryption for all file content
- EME wide block encryption for file names with one IV per directory
Gocryptfs works on Linux systems and on macOS it is still in the testing phase.
Gocryptfs parameters
There are a series of variables of this utility to be used, these are:
- -aessiv: implement AES-SIV encryption mode
- -allow_other: allow access to other users, subject to file permission verification
- -config string: makes use of the configuration file that we indicate instead of using CIP-HERDIR / gocryptfs.conf.
- -d, -debug: enable debug output
- -dev, -nodev: This option enables (-dev) or disables (-nodev) device files in a gocryptfs mount (default: -nodev)
- -exec, -noexec: enable (-exec) or disable (-noexec) executables in a gocryptfs mount
- -forcedecode: Forces decoding of encrypted files even if integrity check fails
- -fsck: Checks the consistency of CIPHERDIR, in case of being detected corruption, the exit code is 26
- -fusedebug: enable FUSE library debug output
- -h: access the help of the utility
- -hh: displays all available options
- -info: prints the content of the configuration file to be read by the human being, eliminating confidential data.
- -init: Initialize the encrypted directory.
- -masterkey string: makes use of an explicit master key specified in the command line
- -nonempty: Allows mounting on non-empty directories
- -noprealloc: Disable pre-allocation before writing data
- -passwd: change directory password
- -plaintextnames: Do not encrypt file names or symbolic link destinations.
- -raw64: use base64 encoding without padding for filenames
- -speed: Run the encryption speed test.
1. Install Gocryptfs on Linux
Step 1
To install this encryption utility we are going to execute the following command:
On Ubuntu or Debian: sudo apt install gocryptfs On CentOS or Fedora: sudo dnf install gocryptfs In Manjaro: sudo pacman -Syu gocryptfs
Step 2
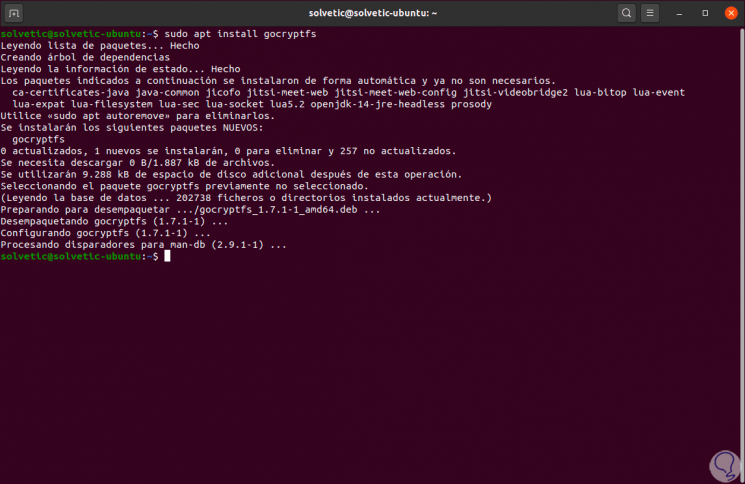
In this case we will install it in Ubuntu:
sudo apt install gocryptfs
Step 3
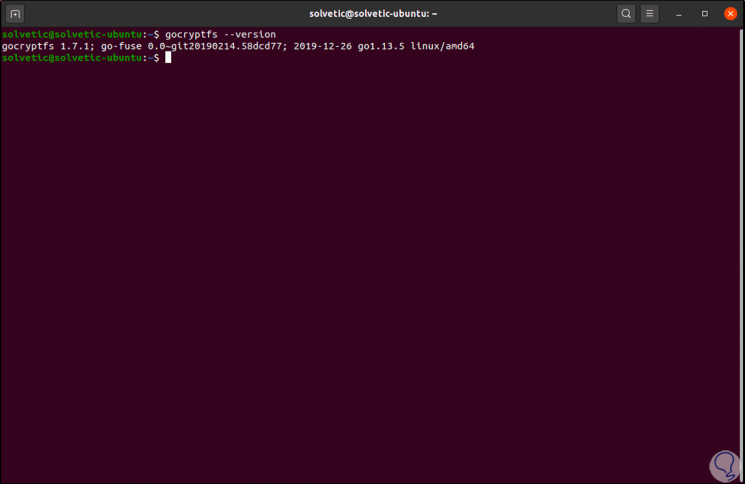
Once installed we can validate the version used with the following command:
gocryptfs -version
2. Create Gocryptfs encrypted directory on Linux
Step 1
Basically the process of use to encrypt a file is the following:
- Create a directory where the files and subdirectories to be encrypted will be stored
- Make use of Gocryptfs to initialize said directory.
- Create an empty directory which will act as a mount point to later mount the encrypted directory on it.
- At the mount point, it is possible to view and use the decrypted files and create new ones if it is the case
- Unmount the encrypted folder when the process is complete
Step 2
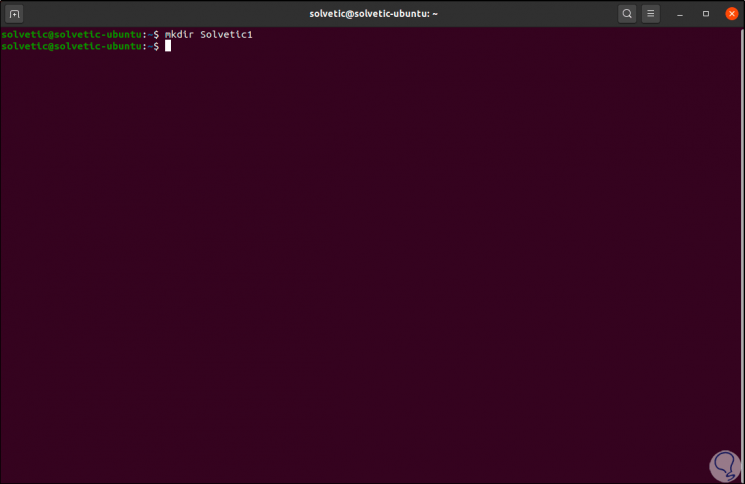
We will create the directory with the command "mkdir":
mkdir TechnoWikis1
Step 3
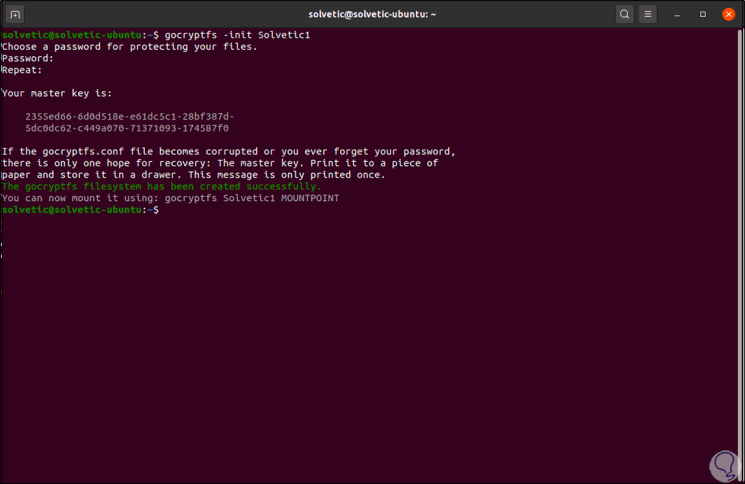
Now we are going to initialize this new directory, there the Gocryptfs file system will be created within the associated directory:
gocryptfs -init TechnoWikis1
Step 4
By pressing Enter we enter and confirm the password to use and as a result we will obtain the master keys of the directory. We can copy this master key and paste it in a safe place.
Step 5
Now we will go to the directory that we have created with the command "cd":
cd TechnoWikis1
Step 6
Once there we enter the following:
ls -ahl
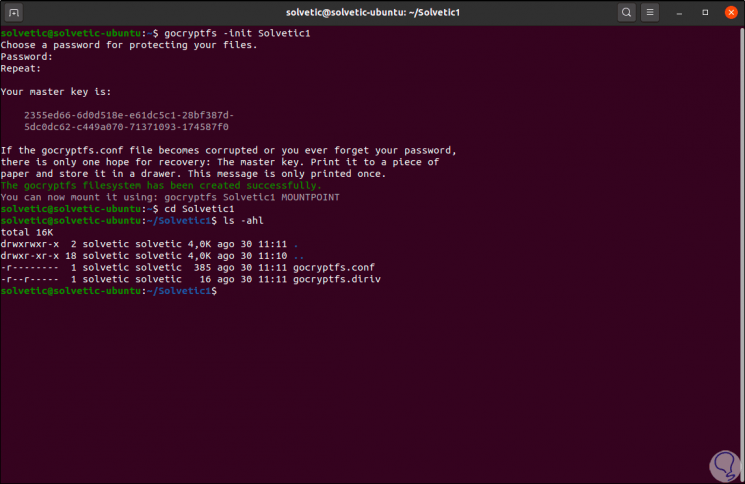
Step 7
There we find two files that are:
- "Gocryptfs.diriv" which is a short binary file
- "Gocryptfs.conf" is a file where the configurations and information to be backed up are stored
Note
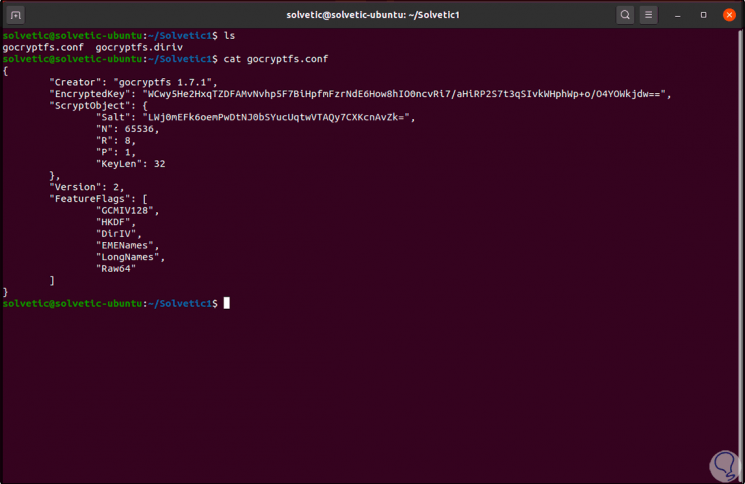
In case of uploading the encrypted data to the cloud or carrying out a backup on a USB, TechnoWikis advises you not to integrate this file there, this because a user can obtain the password from the entries of "encrypted key" and " salt "with the command:
cat gocryptfs.conf
3. Mount Gocryptfs encrypted directory on Linux
Step 1
The encrypted directory will be mounted on a mount point, this is an empty directory, we create the new directory:
mkdir TechnoWikis2
Step 2
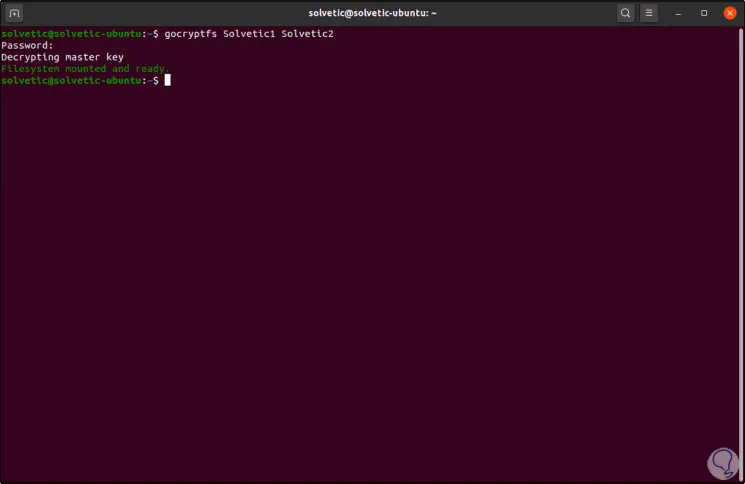
It is time to mount the encrypted directory in the mount point, what it does is mount the Gocryptfs file system within the encrypted directory that we have created, we execute:
gocryptfs TechnoWikis1 TechnoWikis2
Step 3
When doing this we will enter the password that has been assigned in the beginning and we will see the following:
Step 4
Once the directory is mounted, we can create and edit the objects that are necessary in it, in this case we create a text file with "touch" and with "gedit" we edit it:
touch TechnoWikis.txt gedit TechnoWikis.txt
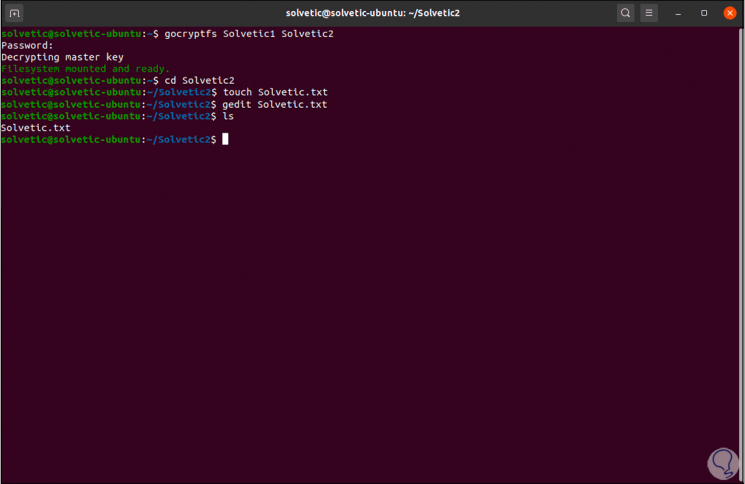
Step 5
By changing to the encrypted directory we can see that a new file has been created where its name is encrypted:
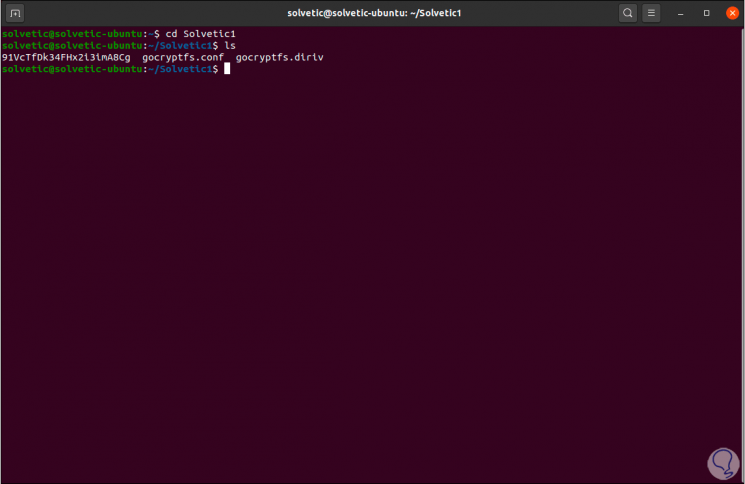
Step 6
There we can use "ls -hl" for more complete details:
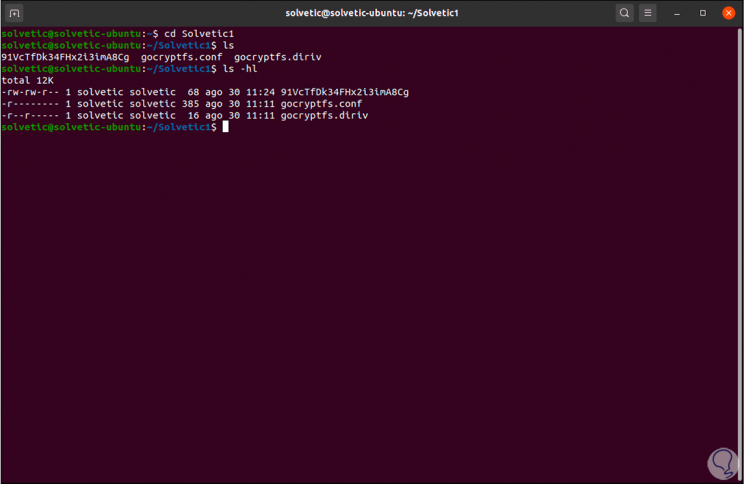
Step 7
We can try to visualize the content of this file with the command "them":
less "file"
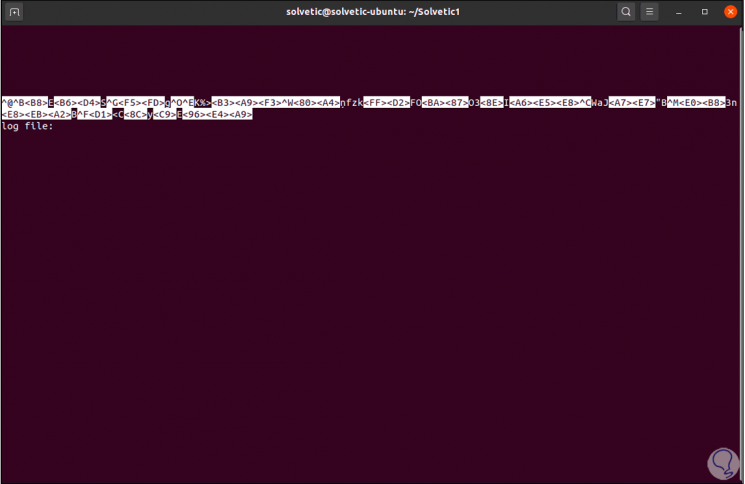
4. Unmount Gocryptfs encrypted directory on Linux
Step 1
When the moment is necessary we can unmount the directory using the fusermount command:
fusermount -u TechnoWikis2
Step 2
Then we can access this directory and with "ls" validate that it is empty:
Gocryptfs is one of the most complete solutions to add security to confidential files in Linux.