Security must be one of the most important pillars in any organization and for any user regardless of their position, role or skill to use. Why is a vital and simple pillar: Every day we are facing millions of attacks of all kinds on the network and externally or internally that can affect our information and make it fall into the wrong hands..
Thought at this level of security, TechnoWikis through this tutorial wants to explain in depth how to encrypt our file systems in Linux in a practical and functional way thanks to a utility called Cryptmount.
What is Cryptmount?
Cryptmount is a utility developed for GNU / Linux operating systems through which a user without root privileges is allowed the ability to mount an encrypted file system without requiring the use of superuser privileges, something that by default is contemplated in All Linux distributions.
Cryptmount can be implemented in Linux distros that use kernel 2.6 or later. In addition, Cryptmount offers simple administration to the system administrator to create and manage encrypted file systems according to the dm-crypt device-mapper objective of the kernel used..
We currently have two main approaches to the use of encrypted file systems within the kernel of any Linux distribution which are:
- The cryptoloop device driver
- The device-mapper system, using the dm-crypt objective.
The new devmapper system allows a cleaner organization of encryption and access to various devices which translates into superior performance.
Within the different features of this utility we have
Cryptmount features
- Access to enhanced kernel functionality
- Transparent support for file systems stored on plain disk partitions or loopback files
- It has separate encryption of access keys to the file system, which gives us the possibility to change access passwords without re-encrypting the entire file system by improving times
- Ability to store multiple encrypted file systems within a single disk partition, using a designated subset of blocks for each
- For file systems that are not used frequently, they do not need to be mounted at system startup.
- The disassembly of each file system is locked, so that only the user who mounted it or the superuser can do it.
- All encrypted file systems are compatible with cryptsetup
- Encrypted passwords can be chosen to be compatible with openssl, or managed through libgcrypt, or (for versions 2.0 series) with built-in SHA1 / Blowfish codes
- Support for encrypted swap partitions (superuser only)
- Support for configuring encrypted or crypto-swap file systems at system boot
How to install Cryptmount on Linux
Step 1
For Debian or Ubuntu systems we will execute the following command for the installation of Cryptmount:
sudo apt install cryptmount
In the case of Fedora, RedHat or CentOS, we will first execute the following to install certain required packages:
yum install device-mapper-deve
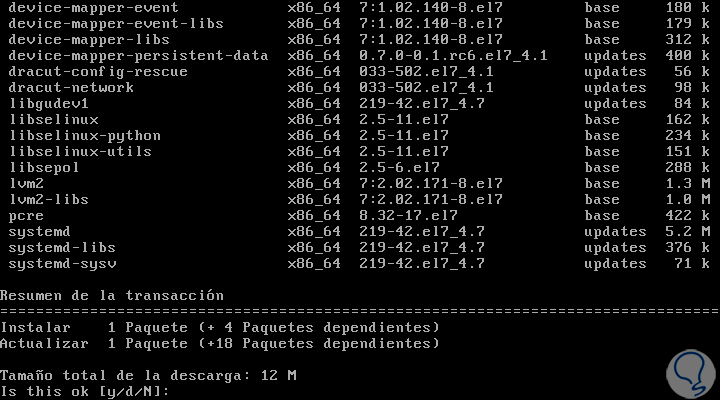
There we enter the letter and to confirm the download and installation of these packages.
Step 2
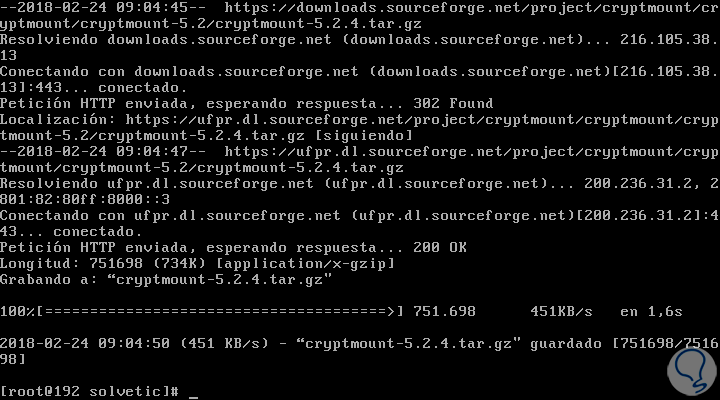
Once this package is installed, we will use the wget command to download the utility:
wget https://downloads.sourceforge.net/project/cryptmount/cryptmount/cryptmount-5.2/cryptmount-5.2.4.tar.gz
Step 3
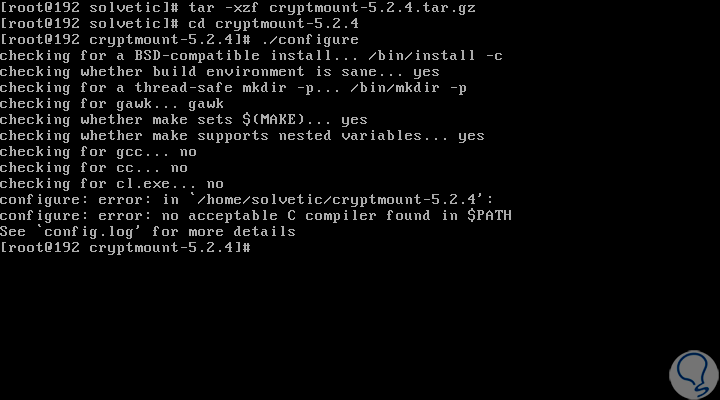
We proceed to extract this downloaded file:
tar -xzf cryptmount-5.2.4.tar.gz
We access the created directory:
cd cryptmount-5.2.4
There we will execute the following command to start the configuration process:
./configure
Step 4
Finally, we execute the installation with the following commands:
make make install
Once this process is complete, we will configure cryptmount and create an encrypted file system using the cryptmount-setup utility as a superuser or through sudo as follows:
cyptmount-setup sudo cyptmount-setup
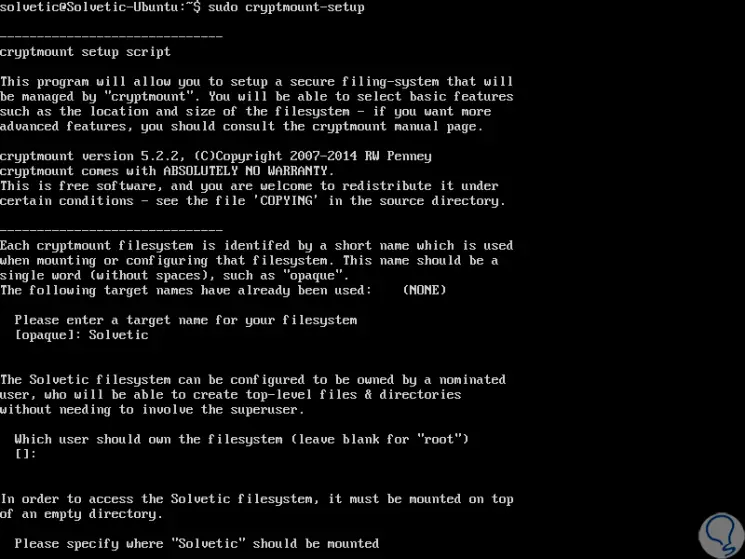
When executing this command we will see a series of questions to configure a secure file system that will be managed by cryptmount. First, the destination name for the file system will be requested, user who must own the encrypted file system, location and size of the file system, file name (absolute name) for its encrypted container, location of the key and password for the destination.
For this case we have used the name TechnoWikis for the destination file system. The following is a sample output of the output of the r-setup command:
Step 5
Later we configure the desired passwords and define paths and file sizes:
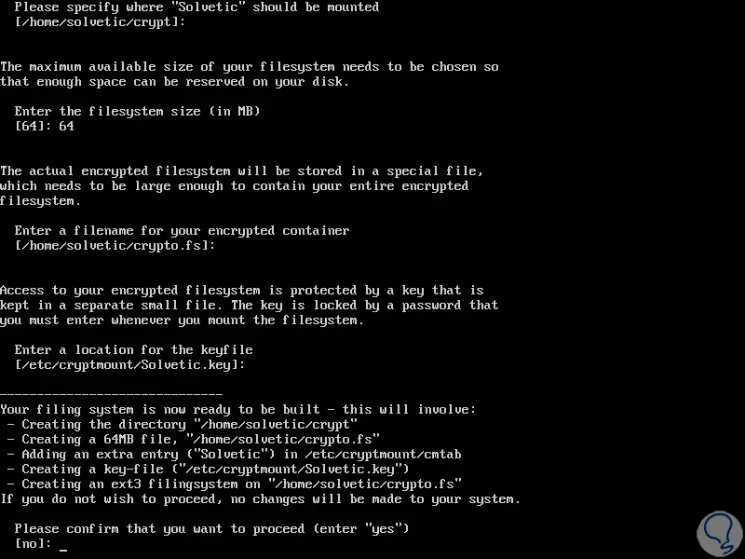
Step 6
Finally we will see the following:
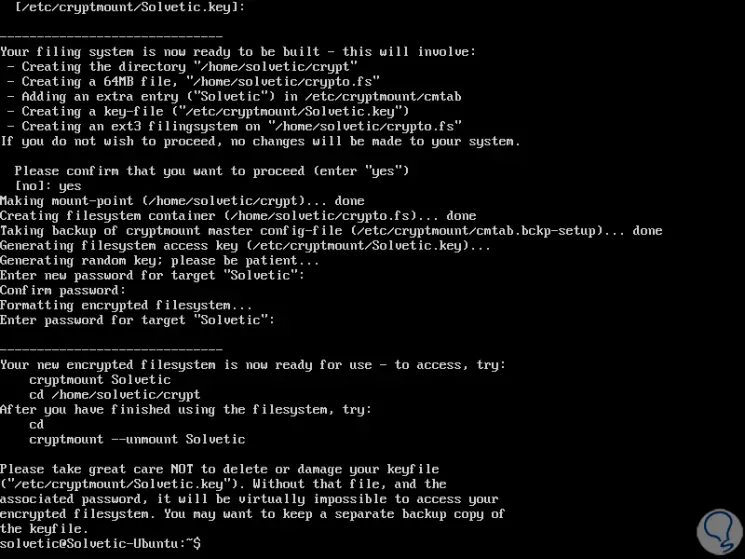
Once we have created the new encrypted file system, it will be possible to access it in the following way indicating the name we use for your purpose and we will see a message where the password for the destination will be requested:
cryptmount TechnoWikis
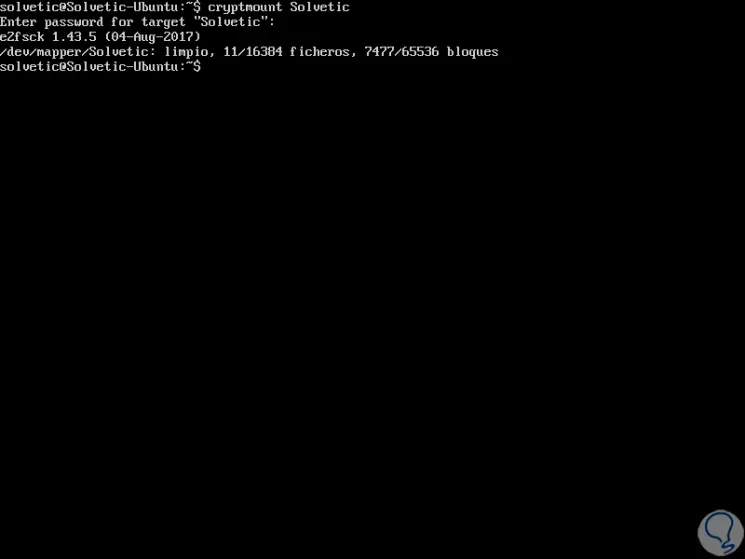
Step 8
To disassemble the created system we will execute the following:
cryptmount -u TechnoWikis
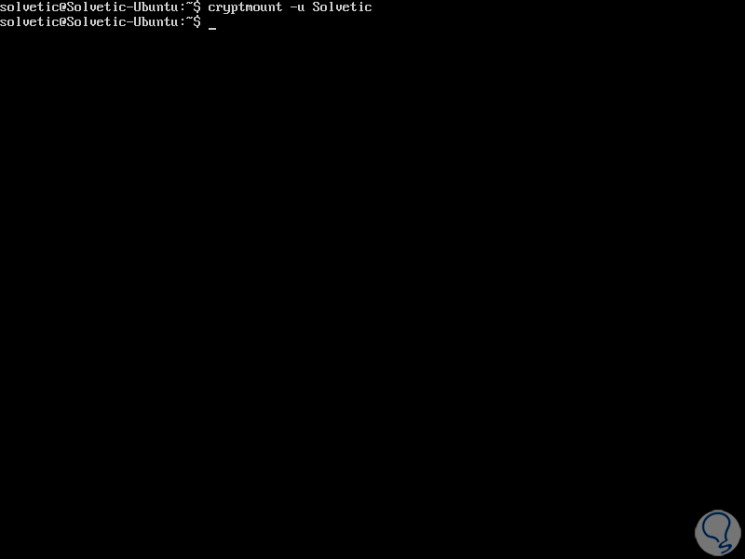
Step 9
In case of having multiple encrypted file systems we can execute the following command to verify which we have:
cryptmount -l
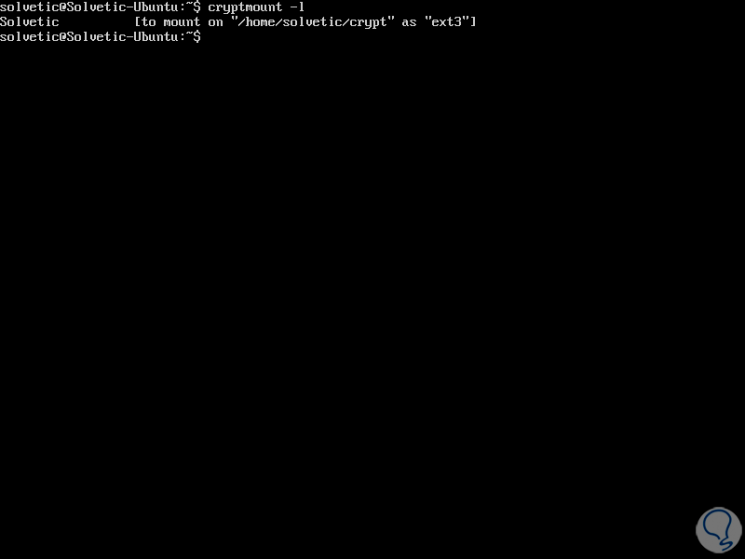
Step 10
If you wish to modify the target password, we will execute the following:
cryptmount -c TechnoWikis
There we will enter the new password.
To get more help on this utility we can execute any of the following commands:
man cryptmount man cmtab
Thus, Cryptmount is another alternative when it comes to adding security layers not only to the Linux file system but to all the information stored there..