Many times we have mentioned the importance and the vitality of maintaining the security of the files and documents in our operating system since many of them are private or confidential and if they fall into the wrong hands it can become a headache or a security risk depending on the type of information hosted there. Today we find both paid and free applications that are willing to offer us various levels of security , but today in TechnoWikis we will focus on a special utility that many of us already know and that we will explore its alternatives such as VeraCrypt..
What is VeraCrypt?
VeraCrypt has been developed as a completely free security software through which it will be possible to carry out the task of disk or file encryption and is an open source utility which is available for Windows, macOS and Linux operating systems and is a tool based on TrueCrypt 7.1a. With VeraCrypt it will be possible to protect all our files by encrypting them by using a password, this is responsible for creating a protected area, which is called volume, either locally or on a storage device, now, all this volume is hosted in a single file called a container, which will be possible to open (mount) and close (unmount).
Another advantage of VeraCrypt is the possibility of creating and managing encrypted volumes which occupy the entire space of a physical medium. VeraCrypt adds more security to the algorithms that are used for encryption of systems and partitions, which allows protected elements to be secure against new brute force attacks. When using VeraCrypt we have a utility that solves vulnerabilities and security problems found in TrueCrypt.
To understand this VeraCrypt operation a bit more against the old TrueCrypt, it is ideal to know that while TrueCrypt uses PBKDF2-RIPEMD160 with 1000 iterations, VeraCrypt will use 327661 iterations, in the case of standard containers and other partitions, TrueCrypt use up to 2000 iterations, while VeraCrypt will use 655331 for RIPEMD160 and 500,000 iterations for SHA-2 and Whirlpool..
So we can see the improved security levels of VeraCrypt.
VeraCrypt features
When using and implementing VeraCrypt we will have the following features:
- Ability to create a virtual encrypted disk within a file and it will be mounted as a real disk.
- VeraCrypt can encrypt a complete partition or storage device such as USB flash drive or hard drive.
- The encryption to use is automatic, real-time and transparent.
- Possibility to encrypt a partition or drive where Windows is installed.
- Encryption can be accelerated by hardware in modern processors that support this technology.
- Parallelization and channeling make it possible for data to be read and written as quickly identically as if the unit was not encrypted.
- In case a user forces us to show the password we can use the hidden volume (steganography) and hidden operating system function.
VeraCrypt functions
VeraCrypt makes use of encryption on the fly which is nothing more than the data is automatically encrypted before saving and can be decrypted immediately after they are loaded without user intervention, thus, it will not be possible to read (decrypt) the stored data on an encrypted volume without using the correct password or file keys or the correct encryption keys which translates into high levels of security.
When using VeraCrypt it will be possible to carry out specific tasks such as:
- Simple encryption: It is the simplest form of VeraCrypt which uses encrypted volumes, which are folders created with secure passwords, so it will only be possible to access them by mounting them as a virtual encrypted disk which is mounted as a real disk as we have mentioned.
- Encrypted volumes within volumes: It is a more advanced option since it involves storing the information in a VeraCrypt volume which is later encrypted and housed within another encrypted VeraCrypt volume, thus, the volume that hosts sensitive information is hidden in sight and so really more levels of privacy are added.
- Encrypt a complete partition or storage device: It is the option of integral security since it will be possible to encrypt the entire current hard disk or some external hard disk or USB device.
We propose the video where you can see how to easily encrypt a USB memory using Veracrypt to protect your information..
To keep up, remember to subscribe to our YouTube channel! SUBSCRIBE
1. Install VeraCrypt on Windows 10
Step 1
For this case we will use Windows 10 and this utility is available in executable or portable version in the following link.
VeraCrypt
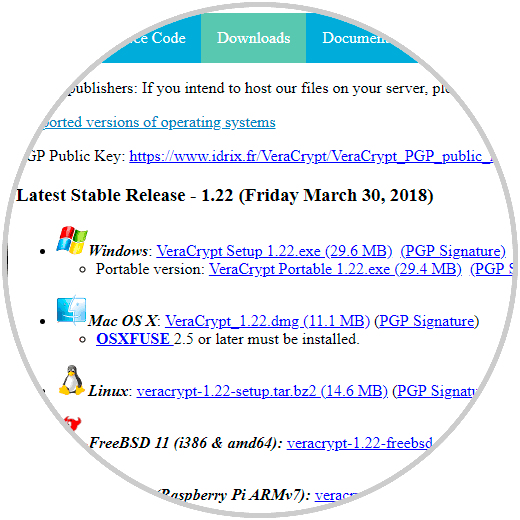
Step 2
There we select the desired option and note that the macOS case requires an additional package called OSXFUSE. We download the executable and when executing it, the following wizard will be displayed where we will accept the license terms:
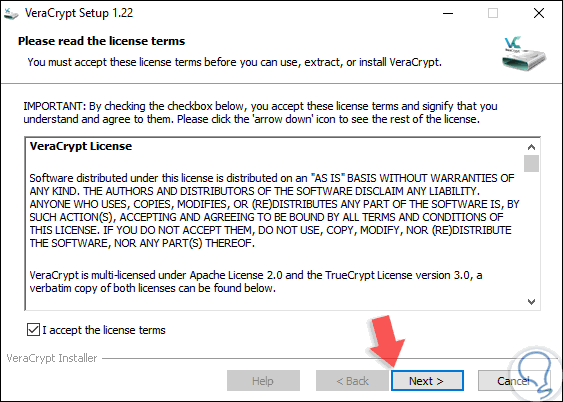
Step 3
Click on the Next button and we must define the installation mode of VeraCrypt:
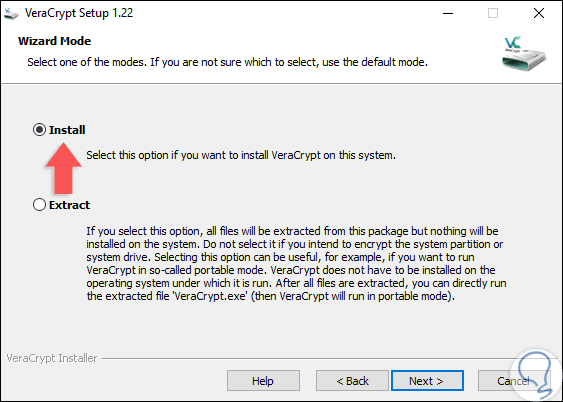
Step 4
In the next window we define the installation path and usage settings for the utility by activating the respective boxes:
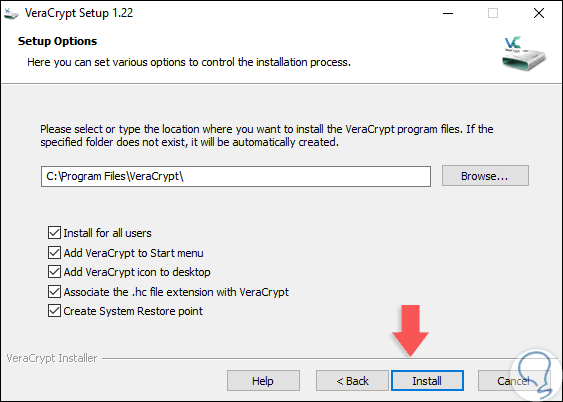
Step 5
Click on the "Install" button to carry out the installation process in Windows 10.
2. Set language in VeraCrypt in Windows 10
Step 1
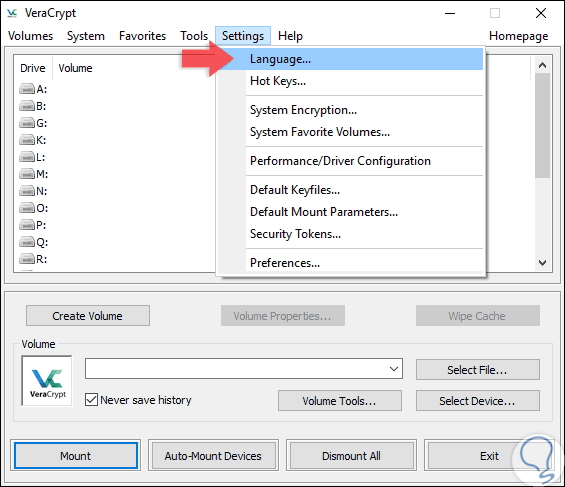
By default VeraCrypt will be installed in English, but it has more than 20 languages ​​available, to edit this, we go to the “Settings / Language†menu:
Step 2
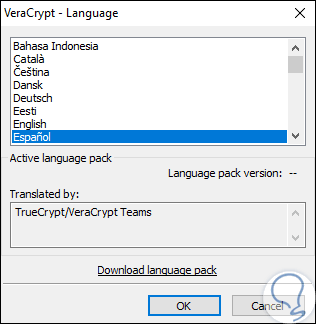
In the window that appears, select the desired language and click on OK. The change will be automatic.
3. Create a new volume in VeraCrypt in Windows 10
Step 1
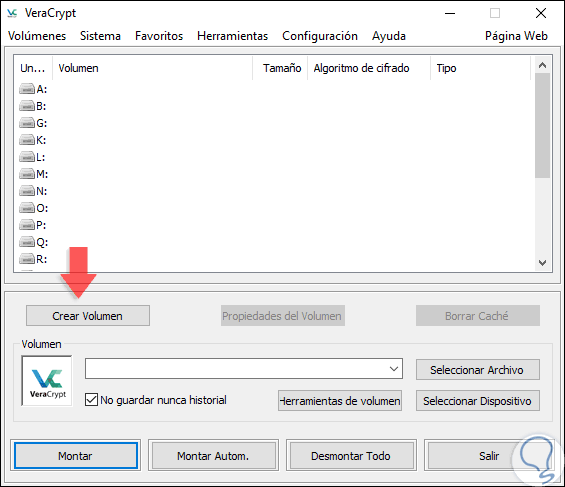
At the moment of executing the tool we will see the following environment where we click on the “Create Volume†button:
Step 2
The following wizard will be displayed:
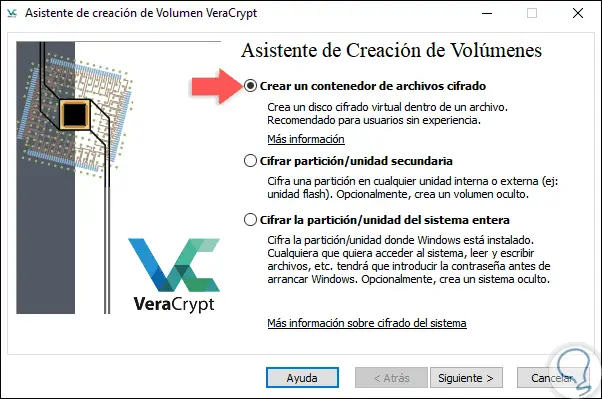
Step 3
There we select the “Create an encrypted file container†box and click Next where we will see this:
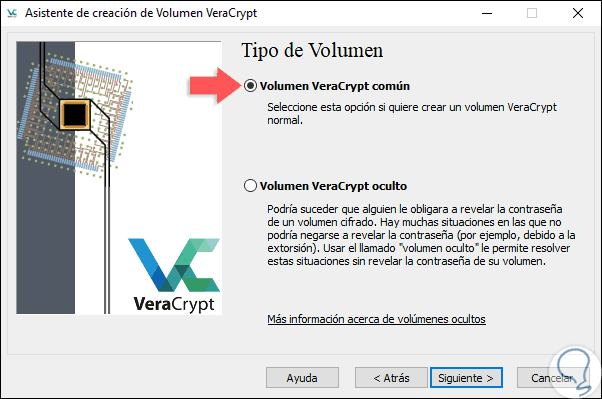
Step 4
There it will be necessary to define the type of volume and the options to be used are:
Common VeraCrypt Volume
It is the default option which, once the volume is encrypted, will be visible to all system users.
Hidden VeraCrypt Volume
With this alternative we have more levels of security and privacy since, by activating this, for most applications the information stored there will only be similar to random data.
Step 5
In this case we leave the default option and click Next where we will see the following option:
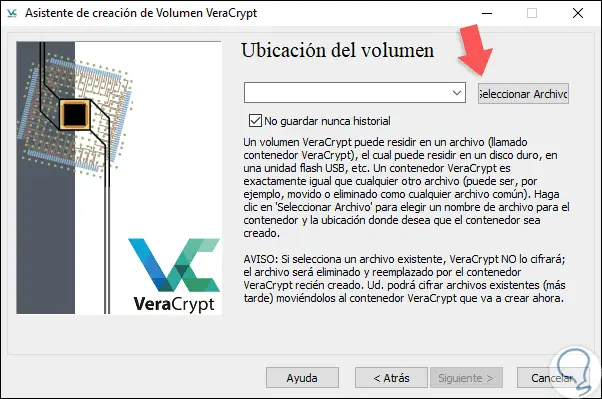
Step 6
In view of the fact that the encrypted file has not yet been created, we must click on the “Select File†button and go to the area of ​​our equipment where you want to create the encrypted volume, this volume can be moved to another location at any time:
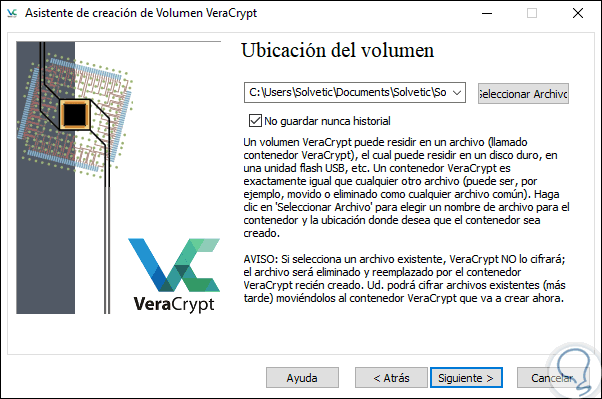
Step 7
Click Next and the time has come to add security to our work since we will be in the encryption section:
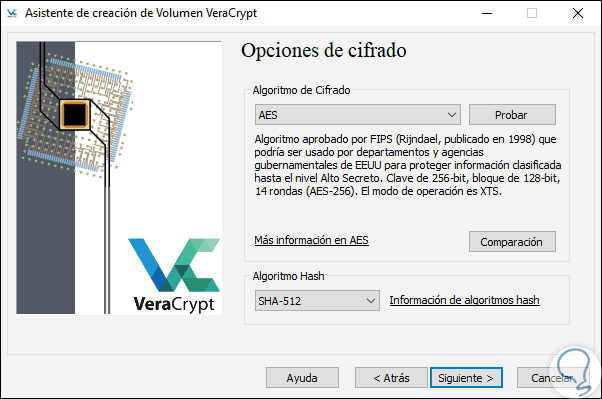
Step 8
The encryption algorithm options are:
AES Advanced Encryption Standard
It is a cryptographic method which makes use of a key of varying length and is called according to the key length used such as AES-128, AES-192 or AES-256. Advanced Encryption Standard is based on the Rijndael algorithm which is combined with symmetric block encryption for the entire encryption method. The block and key lengths are defined respectively with AES.
Serpent
This method is based on a block size of 128 bits and is capable of supporting key sizes of 128, 192 and 256 bits in length, this encryption works in 32 rounds of substitution / permutation which work on four blocks of 32 bits
Twofish
This algorithm is designed as a symmetric encryption method of a block size of 128 bits and key sizes of up to 256 bits. Twofish consists of 16 rounds and the encryption / decryption unit consists of several operating modules.
Camellia
This algorithm is a symmetric key block encryption which has a block size of 128 bits and key sizes between 128, 192 and 256 bits, its development originated in Japan through Mitsubishi Electric and NTT, this algorithm uses a Feistel encryption of 18 rounds or 24 rounds.
Kuznyechik
As the name implies, this Russian algorithm is a symmetric block encryption which has a block size of 128 bits and a key length of 256 bits. It is defined in the National Standard of the Russian Federation GOST R 34.12-2015.
Step 9
In addition to these, VeraCrypt gives us the opportunity to combine some of them as:
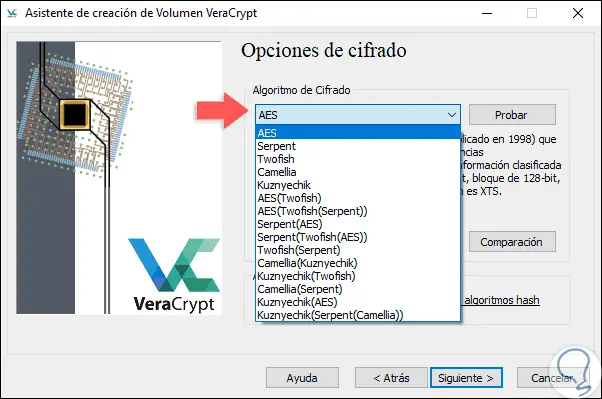
Step 10
Once the algorithm method is defined it will be necessary to configure the hash algorithm where we have the following options:
Step 11
For this example we will use AES with SHA-512. Click on Next and now we must define the size of the volume to be encrypted and it is vital to define the size to use since this cannot be edited and then we would have to repeat the whole process, this size can be defined in KB, MB, GB or TB, note that VeraCrypt indicates the space available for this purpose:
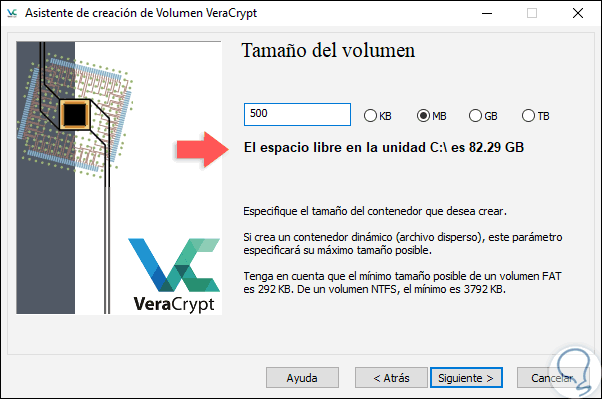
Step 12
We define the size of the volume and click Next and now we must define a secure password for encryption:
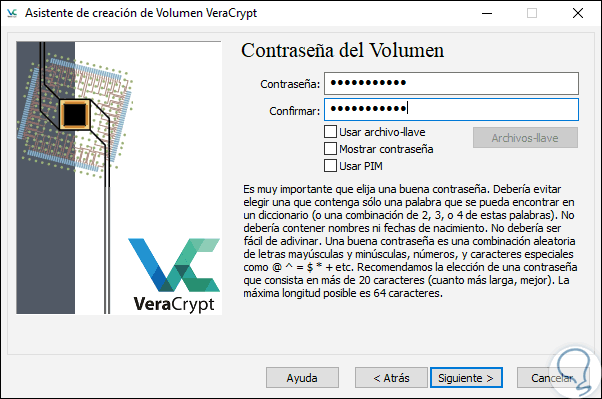
Step 13
Note that we can use resources such as PIM or key files, for security, VeraCrypt recommends passwords of more than 20 characters or else the following will be displayed:
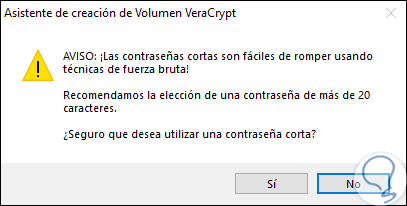
Step 14
Click on the Yes button to confirm. Once the password is defined, click on Next and there it will be necessary to define the file system to be used, the options to be used are:
Important
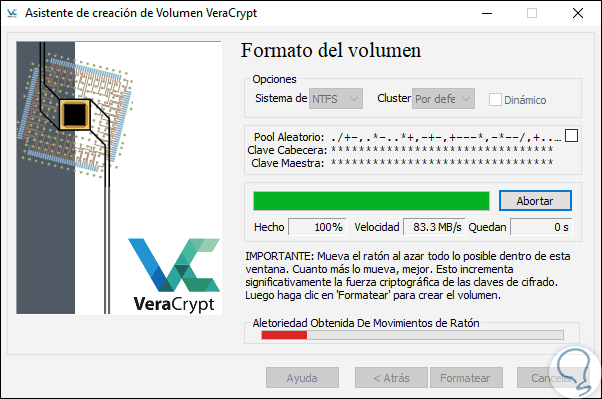
Move the mouse inside that window from side to side so that the cryptographic force grows. You will see that the bar moves and grows, it is advisable to wait to see it in green to give Format.
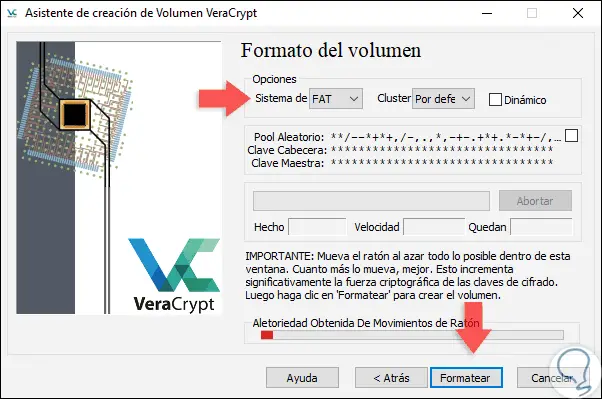
Step 15
Once this is defined, click on the “Format†button and in this case we have selected NTFS:
Step 16
Once this process is finished we will see the following:
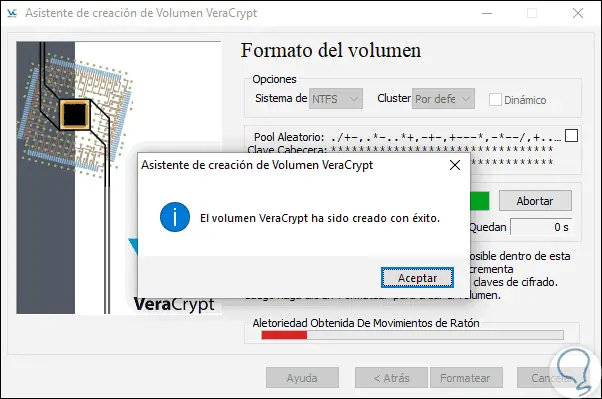
Step 17
Click OK to exit the wizard and we will see the following. If we want to create another volume click on Next or otherwise on Exit.
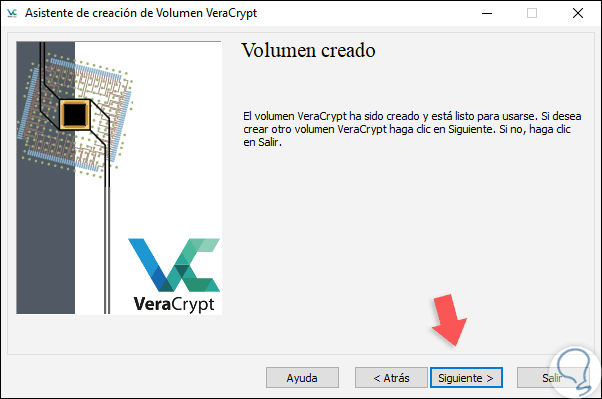
4. Access the volume created in VeraCrypt in Windows 10
Step 1
Now we will access the volume that has been created and for this we select the desired letter and click on the “Mount†button located at the bottom:
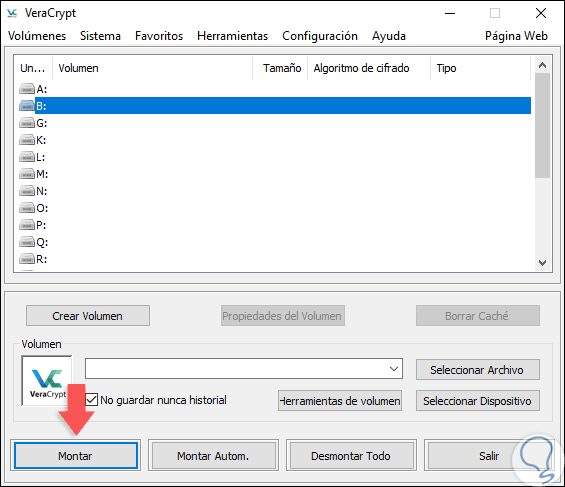
Step 2
A message will be displayed indicating that we must select the file or device to use, for this, in this case, click on the "Select Files" button and go to the path where the volume was created:
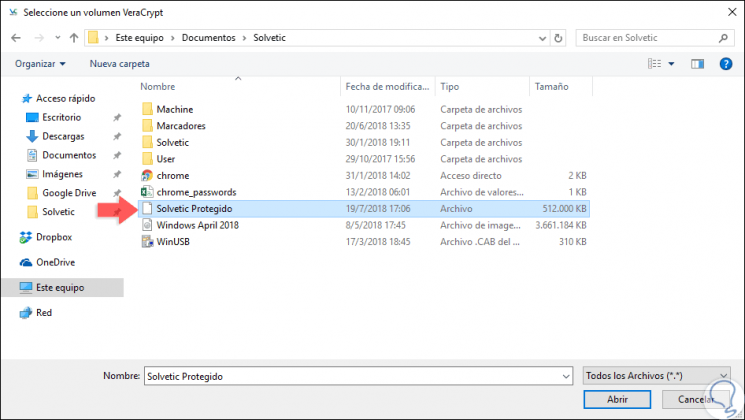
Step 3
Click on Open and we will see the following:
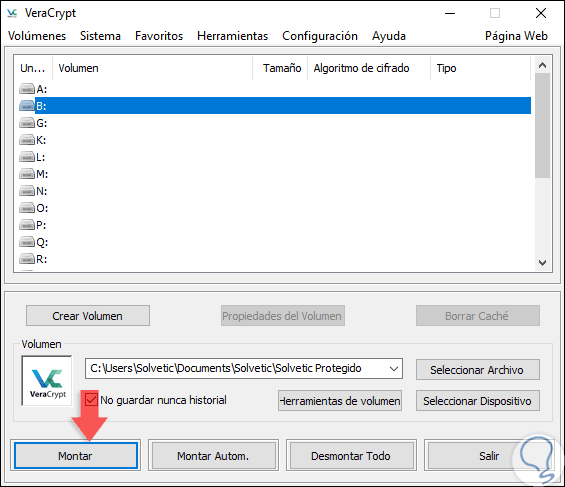
Step 4
Again click on Mount and the following pop-up window will be displayed where we will enter the password we have assigned:
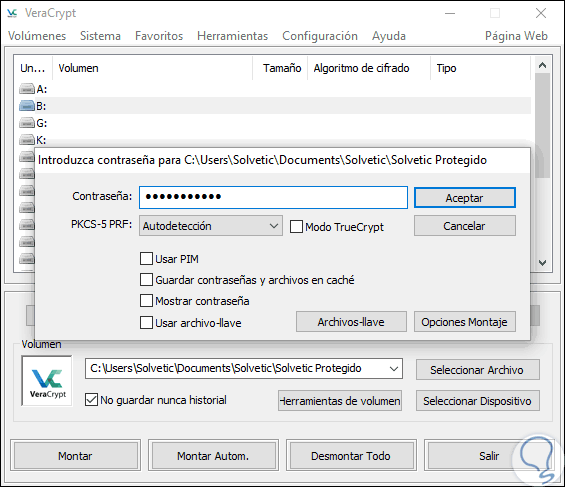
Step 5
Click on Accept and we will see our volume mounted with its respective encryption algorithm and assigned size:
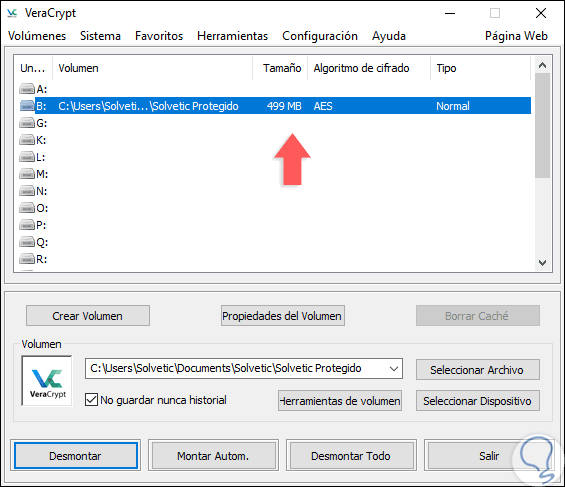
Step 6
Now, in the case of Windows 10, we can go to the file explorer and there we will see the mounted unit with the letter that we have assigned, in this case the B:
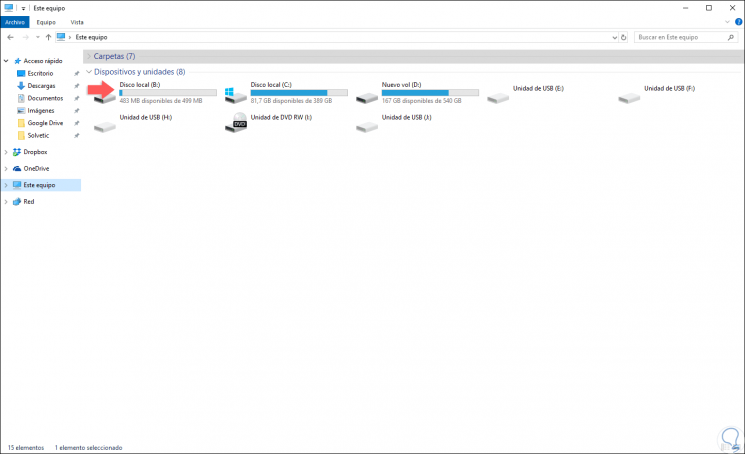
Step 7
We will double click on it and add the necessary files. So we can add all the files that are necessary for protection.
5. Remove the volume created in VeraCrypt in Windows 10
Step 1
At the moment we want to disassemble the volume created from VeraCrypt, just go to the utility and click on the "Dismount" button:
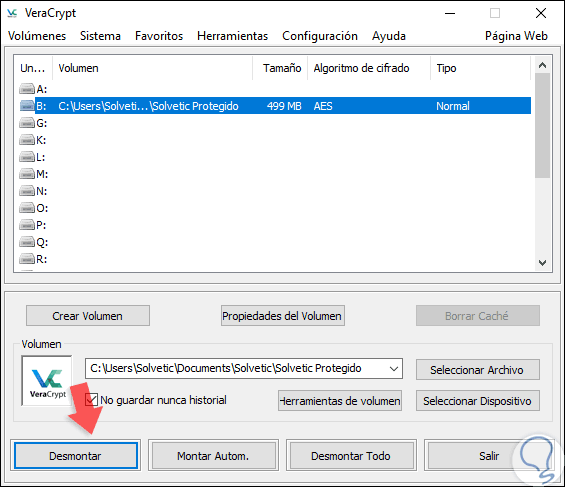
Step 2
Once this is done the volume will be disassembled from the system:
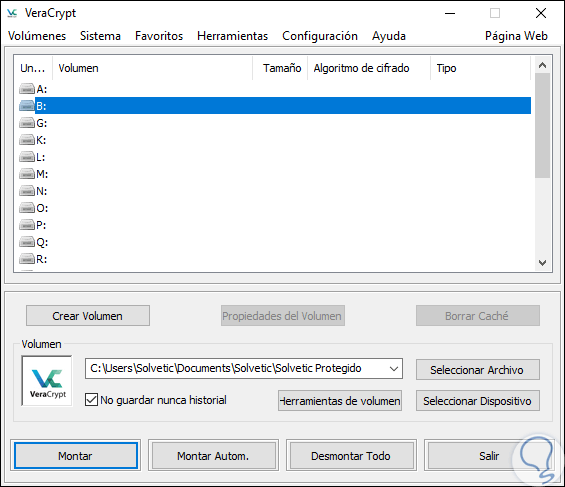
Thus, VeraCrypt becomes one of the most practical and functional utilities to add protection to files or folders that deserve a higher level of protection and privacy.