Microsoft has integrated Windows PowerShell as the default management console in its home (Windows 10) and corporate (Windows Server) operating systems in order to perform hundreds of tasks in a simple, secure and fully functional way..
However, within the tasks that we can execute with Windows PowerShell is the execution of scripts which has the task of automating routine tasks or executing one in particular facilitating administrative actions , and although this is something really useful it can carry certain risks since A script with malicious content can affect various system components such as its records or services, creating a negative impact on all its performance and operability.
For this reason, Microsoft offers several options that as users we can select for the execution of the scripts, from enabling them all regardless of their source (nothing recommended) to restricting them all at all..
To keep up, remember to subscribe to our YouTube channel! SUBSCRIBE
1. View the Windows PowerShell execution policies
Microsoft provides us with a series of Windows PowerShell execution policies in everything related to the scripts which they are.
Restricted
It is the default rule and with it the execution of individual commands is allowed, but no scripts will be executed, in addition to this, the execution of all script files, including configuration and format files (.ps1xml), Module script files (.psm1) and Windows PowerShell profiles (.ps1).
Allsigned (Signatures only)
With this type of policy, scripts can be executed, for this it is required that all scripts and configuration files be signed by a trusted editor, including scripts that are written to the local computer, additional confirmation is requested before executing scripts Publishers who have not been classified who are trusted or not.
Remotesigned
This directive allows the execution of scripts, for this requires a digital signature of a trusted editor in scripts and configuration files that are downloaded from the Internet (including email and instant messaging programs), does not require digital signatures in scripts that have been written to the local computer, that is, that have not been downloaded from the Internet and can run scripts that are downloaded from the Internet and are not signed, if they are unlocked, for example by using the Unblock-File cmdlet.
Unrestricted (No restriction)
This directive gives us the possibility of executing unsigned scripts which is a high security risk, and warns the user before executing configuration files and scripts downloaded from the Internet in order to add security.
Bypass
With this directive, nothing is blocked and neither warnings nor security messages will be displayed, this execution directive has been designed for configurations in which a Windows PowerShell script is integrated into a larger application or in configurations in which Windows PowerShell It is the basis of a program that has its own security model.
Undefined (Undefined)
This option indicates that there is no execution policy set in the current scope, so if the execution policy in all fields is Undefined, the automatic execution policy will be Restricted, which is the default execution policy in Windows 10.
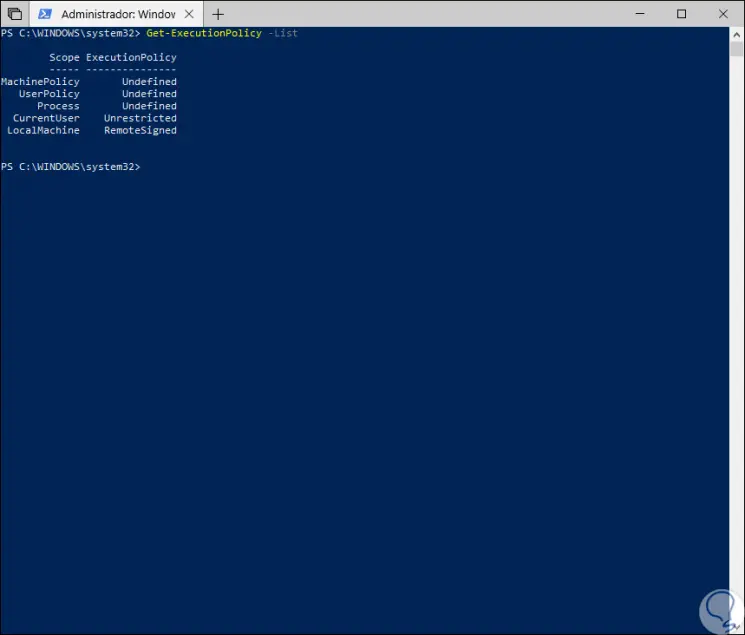
To see all the Windows PowerShell directives we can execute the following. Now let's see how to set a new directive to correctly run a script in Windows PowerShell.
Get-ExecutionPolicy -List
2. Execute script with ExecutionPolicy Windows PowerShell command
Step 1
To make use of this option we have two options to run in Windows PowerShell as administrators that are:
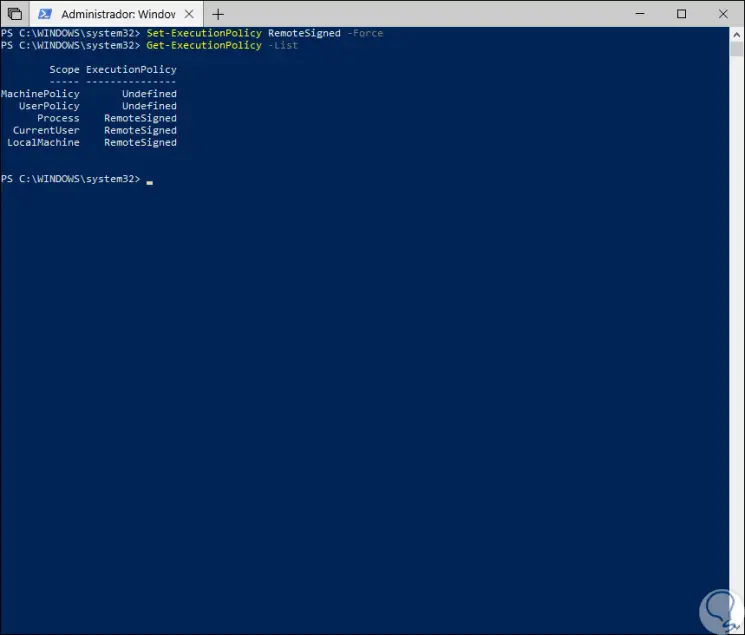
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned Set-ExecutionPolicy RemoteSigned -Force
Step 2
Once any of these lines has been executed, we can validate the result using the following cmdlet
: Get-ExecutionPolicy -List
3. Run script in Windows PowerShell with Registry Editor
Step 1
For this method it is recommended to create a backup copy of the files or create a restore point in case of some kind of failure, then we will use the following keys and execute the following:
+ R
Regedit
Step 2
In the window that will be displayed we go to the next route.
HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ PowerShell \ 1 \ ShellIds \ Microsoft.PowerShell
Step 3
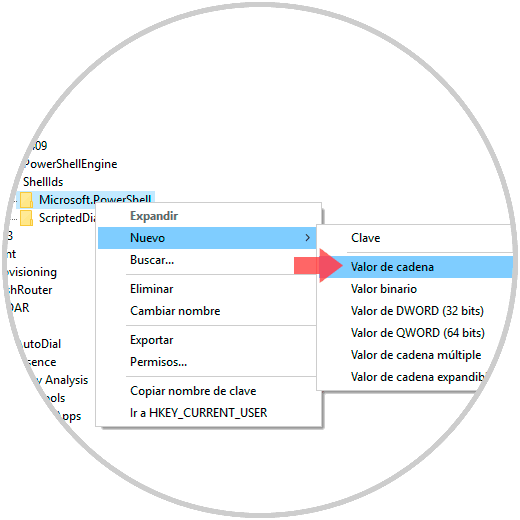
There we will right click on “Microsoft.PowerShell†and select the option “New / String Valueâ€:
Step 4
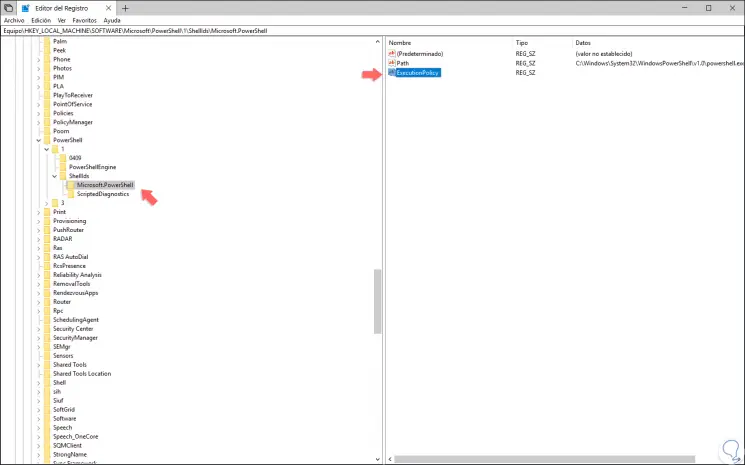
This new value will be called "ExecutionPolicy":
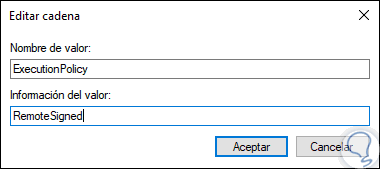
Step 5
We will double click on this value and in the “Value information†field enter “RemoteSignedâ€:
Step 6
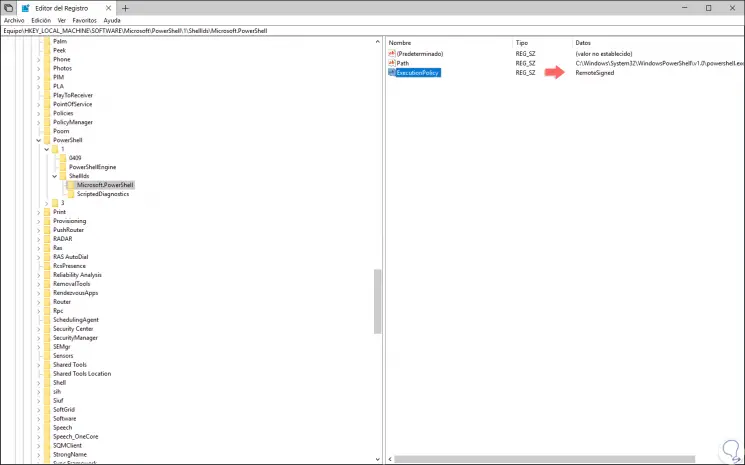
Click on Accept and we will see that this directive is applied:
4. Run script in Windows PowerShell with Group Policies
Step 1
This option is available for the Pro and Enterprise editions of Windows 10 and to access them we will use the following keys and execute the following:
+ R
gpedit.msc
Step 2
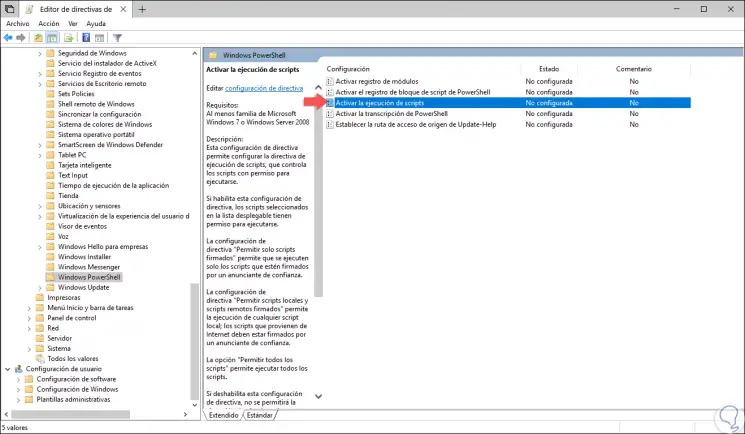
Pressing Enter will display the following window and there we will go to the following route:
Step 2
There we select and open the policy called "Activate script execution":
Step 3
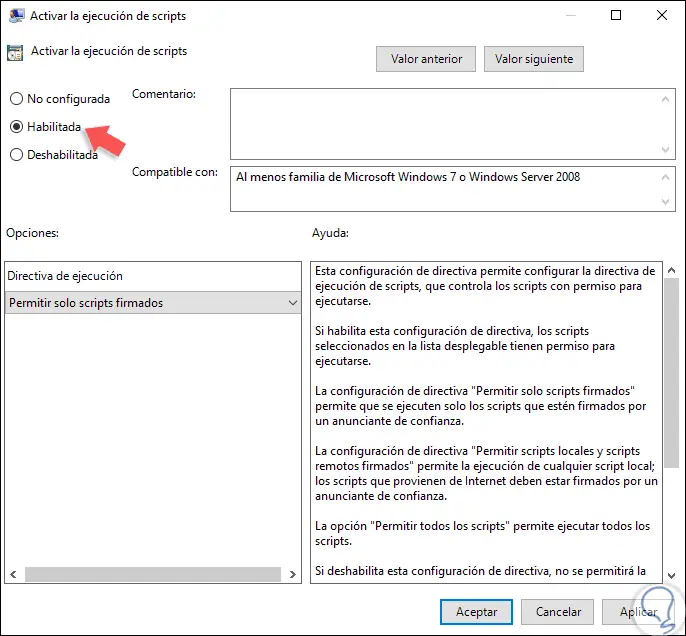
In the displayed window we activate the “Enabled†box and in the “Execution policy†field we can select one of the following options. Once the directive is defined, click on Apply and Accept to save the changes.
- Allow only signed scripts
- Allow local scripts and signed remote scripts
With any of these methods it will be possible to make proper use of scripts in Windows environments..