Introduction
One of the biggest problems that servers, mail and web services are exposed to are attacks through malware . One of the methods to prevent this problem is Linux Malware Detect (LMD) , an application that can be installed on any Linux system and prevent these types of attacks.
Installation
We will suppose that SSH is accessed to the server that we use to perform the installation and can be done from any operating system since the task is connected to the server. 1. We enter our command console by SSH to our server:
ssh [email protected] [email protected]'s password: *******
2. Once we have connected to the server we download the free Linux Malware Detect package on our server: [root @ server1 ~] # wget www.rfxn.com/downloads/maldetect-current.tar.gz
3. Unzip the file: [root @ server1 ~] # tar xfz maldetect-current.tar.gz
With the instruction ls we will be able to review in what directory unzipped it will generally be called as the maldetect version in this case maldetect-1.4.2 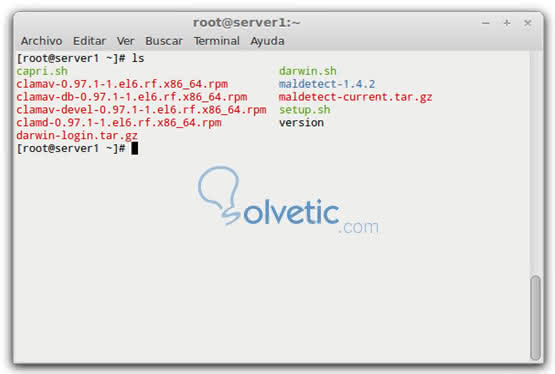
4. We enter the directory and proceed to perform the installation of Maldetect . Here is an installation that will be seen in a few commands:
[root @ server1 ~] # cd maldetect-1.4.2 [root @ server1 maldetect-1.4.2] # ./install.sh Linux Malware Detect v1.4.1 © 2002-2013, R-fx Networks <[email protected]> © 2013, Ryan MacDonald <[email protected]> inotifywait © 2007, Rohan McGovern <[email protected]> This program may be freely redistributed under the terms of the GNU GPL installation completed to / usr / local / maldetect config file: /usr/local/maldetect/conf.maldet exec file: / usr / local / maldetect / maldet exec link: / usr / local / sbin / maldet exec link: / usr / local / sbin / lmd cron.daily: /etc/cron.daily/maldet maldet (10805): {sigup} performing signature update check ... maldet (10805): {sigup} local signature set is version 201205035915 maldet (10805): {sigup} new signature set (2013041816820) available maldet (10805): {sigup} downloaded http://www.rfxn.com/downloads/md5.dat maldet (10805): {sigup} downloaded http://www.rfxn.com/downloads/hex.dat maldet (10805): {sigup} downloaded http://www.rfxn.com/downloads/rfxn.ndb maldet (10805): {sigup} downloaded http://www.rfxn.com/downloads/rfxn.hdb maldet (10805): {sigup} downloaded http://www.rfxn.com/...aldet-clean.tgz maldet (10805): {sigup} signature set update completed maldet (10805): {sigup} 11203 signatures (9335 MD5 / 1868 HEX) Then we do an update of the signature database of maleare [root @ server1 ~] # maldet -update Configuration
In the command window we write below using our preferred nano , vim editor or the one we use often: nano /usr/local/maldetect/conf.maldet
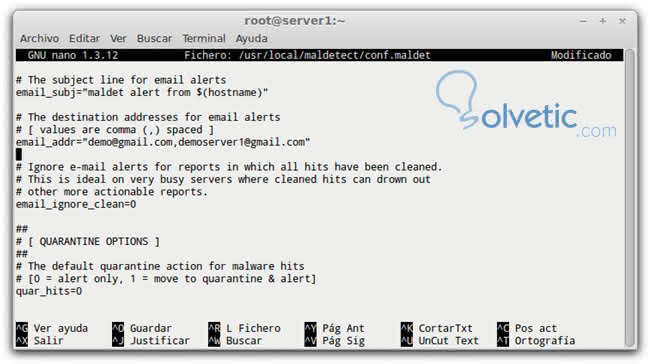
We establish if to find any malware will alert us by email:
And
we define the mail, as seen in the capture: # [0 = disabled, 1 = enabled] email_alert = 1
We also define if we only receive an alert and move the infected file to quarantine so that it can not be executed. # [0 = alert only, 1 = move to quarantine & alert] quar_hits = 0
How to perform the scan
Depending on the structure of the server and the route that the domain or file to scan has.
The -a option indicates All to scan all files in that directory. [root @ server1 maldetect-1.4.2] # maldet -a / home / user / public_html
To see the last report that we have generated, we will execute: [root @ server1 maldetect-1.4.2] # maldet -report
Here is an example of a malware report found in a scan of all the domains of a server, in the list you will see in File Hit List the name of the malware, the file and the code line number where it is located, in In this case, 2 infected files were found. [root @ server1 maldetect-1.4.2] # maldet --scan-all / home malware detect scan report for server.mydomain.com: SCAN ID: 02233-0315.9516 TIME: JUN 6 07:02:44 +0300 PATH: / home * / * / public_html RANGE: 2 days TOTAL FILES: 8406 TOTAL HITS: 1 TOTAL CLEANED: 0 FILE HIT LIST: {HEX} php.cmdshell.unclassed.344: /home/user1/public_html/images/upload/files/asphoto.php.pjpg {HEX} php.nested.base64.513: /home/user2/public_html/formulario.php If a false positive detection results, the quarantine file can be recovered with: [root @ server1 maldetect-1.4.2] # maldet -restore /home/user2/public_html/formulario.php
There are other more advanced configurations for Maldetect , even for it to work using the Clamav antivirus present in many servers.