What services are active, are all necessary?
To see the services that we have assets you can use the netstat command . For example from an SSH connection : root @ server1: ~ # netstat -a
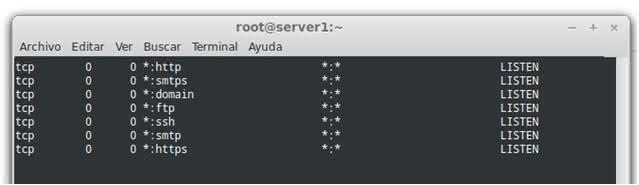
It shows us all the active services and listening to receive users or connections, here we see some like
Apache (http) to serve web pages,
smtp service of sending emails,
ftp to upload files.
You can stop a service if it is unnecessary or if it takes up a lot of memory or cpu, for this we can see the consumption with the command:
root @ server1: ~ # ps aux --sort cputime
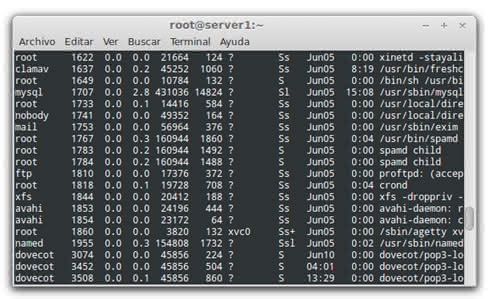
Here we can see Mysql , the Clamav antivirus, and Dovecot is an open source IMAP and POP3 server. Here we can see the process executed by us previously, it is important not to confuse the START column that takes dates and times, it indicates in what date or time the operation began.
Then to stop an example service Mysql:
/etc/init.d/mysql restart /etc/init.d/mysql stop /etc/init.d/mysql start
Example of command use in Linux server security, we are going to use some commands to detect and prevent a denial of services attack that are the most frequent. A denial-of-service attack (DoS attack) or distributed denial of service (DDoS attack) attack is an attempt to make a server resource unavailable to its user.
1) Detect the attack
The main symptom is the server becomes very slow, or "services fall", they stop working because an excess of connections is generated, the server can not respond. We will use the command "netstat".
It shows us the active connections on port 80.
root @ server1: ~ # netstat -an | grep: 80 | sort
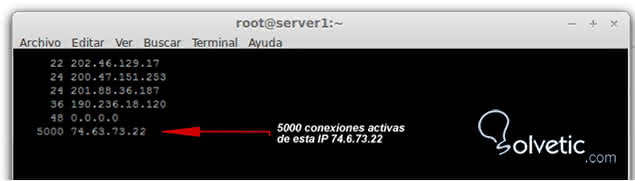
Here we can see that one of the active ip queries our server takes 5000 connections, while it could be said that normal would be about 20 or 30 connections per ip. We could suspect then of a DDOS attack, since the consumption of resources
2) The first thing will be to block the ip of the attacker with Iptables
Iptables is the name of the user space tool through which the administrator can define filtering policies for the traffic circulating on the network. root @ server1: ~ # iptables -I INPUT -s 74,6,73,22 -j DROP
With that it is blocked.
3) Install mod_evasive for Apache
Mod Evasive is a module for Apache that is responsible for providing an additional level of security to our web server very powerful and customizable. In the example we will do it for Centos, but it can be adapted to any Linux with Apache.
We install dependencies from ssh
root @ server1: ~ # cd / usr / src root @ server1: ~ # wget http://www.zdziarski.com/projects/mod_evasive/mod_evasive_1.10.1.tar.gz root @ server1: ~ # tar zxvf mod_evasive_1.10.1.tar.gz root @ server1: ~ # cd mod_evasive root @ server1: ~ # apxs -cia mod_evasive20.c # for Apache 1.3 the command would be apxs -cia mod_evasive.c root @ server1: ~ # vi /etc/httpd/conf/httpd.conf # edit the configuration root @ server1: ~ # service httpd restart # restart the Apache
/etc/httpd/conf/
httpd.conf habrÃa que agregar las siguientes lÃneas. In the / etc / httpd / conf /
httpd.conf the following lines should be added. <IfModule mod_evasive20.c> DOSHashTableSize 3097 DOSPageCount 2 DOSSiteCount 50 DOSPageInterval 1 DOSSiteInterval 1 DOSBlockingPeriod 300 </ IfModule>
The important parameters - DOSPageCount: number of connections that a user can make per sec before their ip is blocked.
- DOSSiteCount: how many requests a user can make before being blocked.
- DOSBlockingPeriod: how long in seconds the blocking of that IP will last.
It would also be advisable to install a firewall such as CSF for Linux that is Open Source.