If your friends suddenly complain about your Facebook posts or are missing funds from your bank account, chances are your account has been hacked. To prevent this from happening in the first place, you should take precautions: You can secure log-ins using various methods and prevent hackers from gaining access to your private data and more. We show you how it works.
5 Tips for Hacker-Safe Accounts
1. Use individual passwords
You should really assign an individual password for each online account . The reason: If a log-in combination that you use multiple times ends up on a password list in the Darknet, all associated accounts are automatically at risk. With individual passwords, you can keep the damage as low as possible in an emergency.
2. Use the password manager
Since it is of course difficult to remember dozens of different credentials, password managers come in handy . The idea: You save all log-in data in an encrypted database. You secure this with a password that is as complex as possible. In the end, you only have to remember one access to secure all passwords. In addition to commercial solutions such as 1password or LastPass, you can also use free solutions such as KeePassX..
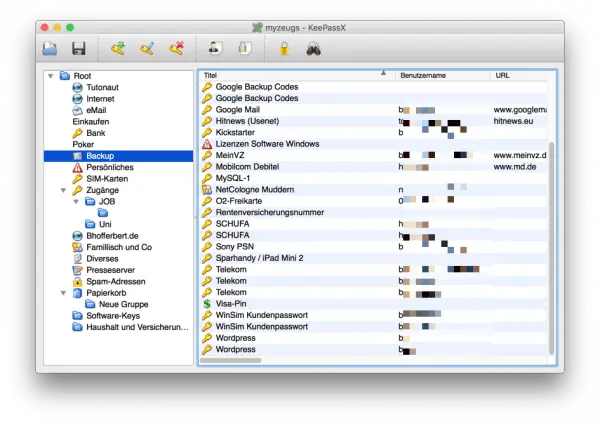 With a password manager like KeePassX you can save as many passwords as you want, but only have to remember one login.
With a password manager like KeePassX you can save as many passwords as you want, but only have to remember one login. 3. Set up two-factor authentication
Many online accesses can be secured with two-factor authentication . Once activated, a password is no longer sufficient to log into an account. Instead, the log-in requires an additional step, for example entering a number code that you receive via SMS on your mobile phone. It takes longer, but it's a big plus for online security. We'll show you how to set up two-factor authentication below .
4. Use strong passwords
Experts have been arguing about what a “secure” password is since the “password” principle has existed in digital form. There is agreement that longer passphrases are still harder to crack than short ones. Instead of using short passwords full of obscure special characters, you should, for example, take a sentence and modify it slightly, for example with a number in the middle. Practical: Password managers like KeePass have already integrated a password generator. This allows you to generate complex, secure passwords that the program saves for you at the same time. In this tipps + tricks article, we explain how to find a password that is as secure as possible..
5. Stay informed
You can do a lot yourself to protect your accounts - but you still have to rely on the service providers with whom you have an account. If hackers steal a password database, all security measures are of no use. It is important that you stay informed in such a case. Affected companies often inform about possible attacks and the necessary measures by e-mail - you should not ignore these e-mails under any circumstances. In addition, you can find out about current threats and attacks on accounts of all kinds on news sites such as Heise Security.
 Make sure to stay up to date so that you can react quickly in the event of a hacker attack.
Make sure to stay up to date so that you can react quickly in the event of a hacker attack. Detect phishing attempts
In addition to data leaks from providers, “ phishing ” is still the most common cause of hacked passwords. The method is as old as it is effective: an attacker tries to direct you to a fake log-in website using a link (e.g. by email or social media). If you log in here, a hacker has got hold of your access data . The good thing: Modern browsers like Chrome and Firefox recognize a lot of fake phishing pages and warn you. Phishing emails also have a hard time with many mail providers. But you shouldn't rely on that alone. The best trick against phishing attempts is this: go to the website directly in your browser instead of clicking links . Hardly any service provider does without an encrypted and signed connection. You can use the browser bar to check in all major browsers whether you are surfing via an encrypted connection . Chrome, Firefox, Edge and the like usually indicate secure connections with green lettering, a lock symbol or something similar. On the other hand, if you see an exclamation mark next to the URL, you should at least be skeptical and reconsider entering your log-in data.
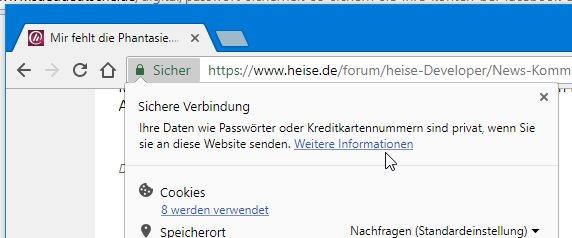 Current browsers reveal at a glance whether the connection to the page is secure and you are really surfing the correct website.
Current browsers reveal at a glance whether the connection to the page is secure and you are really surfing the correct website. Secure accounts with two-factor authentication
The two-factor authentication or short 2FA may sound like very boring to, but to protect remains one of the most efficient ways of your online accounts from unauthorized access. In addition to the classic combination of username and password, access secured with 2FA requires a second code that is generated for every log-in attempt . For example, you can have a code sent to you by SMS or email, generate it with a separate smartphone app such as Authy or the Google Authenticator , or even use a hardware key - such as a USB stick. Once set up, the 2FA ensures that a stolen password alone no longer allows access to your accounts.
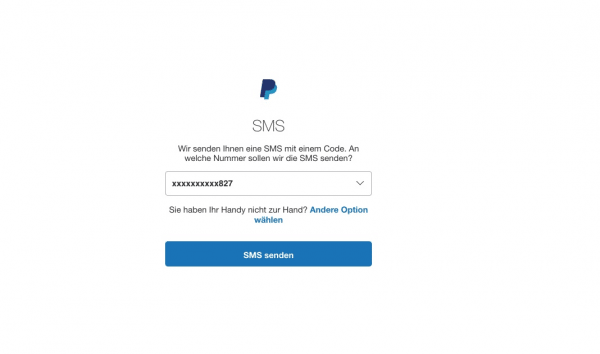 With activated 2FA, PayPal only allows access to the account with a numerical code that you receive via SMS. In this tipps + tricks article, we explain how secure it is to pay with PayPal.
With activated 2FA, PayPal only allows access to the account with a numerical code that you receive via SMS. In this tipps + tricks article, we explain how secure it is to pay with PayPal. The setup of the two-factor authentication is done in a few steps. Among other things, you can secure your accounts with Google, Facebook, Paypal, Dropbox, Microsoft and many other providers.
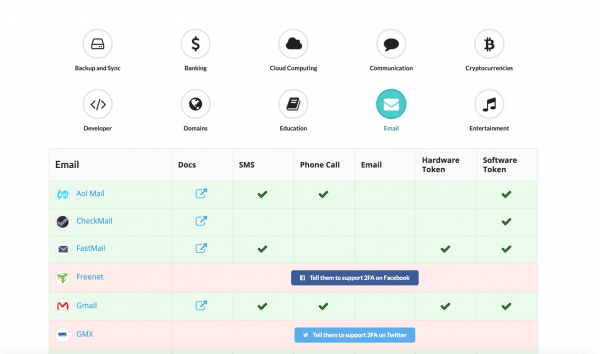 Portals like Two Factor Auth show where you can activate 2FA and where not yet.
Portals like Two Factor Auth show where you can activate 2FA and where not yet. The disadvantage of two-factor authentication: If for some reason you do not have access to your second code, you cannot access your accounts either. For this reason, you should always make sure that you can use a " Plan B " for the use of two-factor authentication . For example, Google offers the option of entering an additional telephone number or email address to restore your log-in. These or similar safety nets are also used by many other services that enable accounts to be secured using 2FA.
Online Account Hacker Attack: What If It's Too Late?
With the right precautions, you are protected against account theft in many cases. But what can you do when an emergency has already occurred? If one of the online accounts has been cracked, you should proceed systematically. If the hackers weren't faster, the first thing you should try to get a new password is. Corresponding links can be found on the respective log-in pages. If it is too late for this, you should contact the company's user support immediately. Many providers such as Facebook or Google offer instructions and procedures in their help areas to restore cracked accounts. Ideally, you can use it to prevent the worst damage.
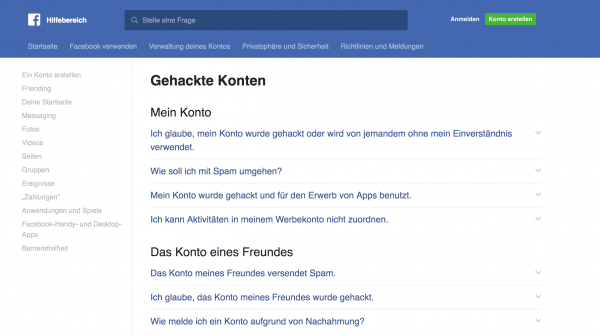 In the help areas, many providers give tips on how to get back hijacked accounts.
In the help areas, many providers give tips on how to get back hijacked accounts. Is it a “social” account like Facebook, Twitter, or your email service? Then you should inform friends and acquaintances about it in order to prevent mistakes and anger. In the event of a hacker attack that could cause you financial problems (e.g. hacked Amazon, e-mail or online banking access), you should immediately ensure that the relevant accounts are temporarily blocked . To do this, contact the support hotline of the relevant provider directly.