Security when we administer users in Linux environments is essential and we must always look for the best options available for this purpose either internally or externally. One of the safest methods to increase security on Linux systems is to administer in a much more complete the way users authenticate in the system , this allows only those users who have the correct credentials are those who will have access to the system..
In this case, we have a functionality called Linux-PAM (Pluggable Authentication Modules for Linux) which has been developed as a set of libraries with which it will be possible for the system administrator to select the way in which the applications authenticate the users of the local network.
When compiling a PAM-compatible application, we are able to switch between the authentication mechanisms used.
To understand this concept a little better we can analyze the way users are authenticated today, firstly the user's identity is verified when the password assigned to the user is entered , these passwords are stored in the file / etc / passwd, then, the privilege is defined in the form of a personal user identifier called UID and membership in the available groups, services and applications are available based on the personal and group identity of each user..
The PAM library is configured locally in the system file /etc/pam.conf or in a series of files located in /etc/pam.d/ in order to authenticate a user request through the modules of Authentication available only locally.
The modules are available in the / lib / security or / lib64 / security directory. The syntax of the configuration file /etc/pam.conf is made up of a list of rules, and each rule is located on a single line, but can be extended with an end of line `\ <LF> '. The comments are preceded by the `# 'marks and extend to the next end of the selected line..
The format of each rule is a collection of tokens separated by spaces, the first three are not case sensitive like this:
service type control module-path module-arguments
The parameters used are:
Service
It is the real name of the application.
Type
It is the type of module / context / interface.
Control
It refers to the behavior of the PAM API in case the module cannot execute the authentication task
Module path
It is the absolute file name or relative path of the PAM.
module-arguments
Indicates a list separated by token spaces in order to control the behavior of the module.
The syntax of each file in /etc/pam.d/ is identical and consists of lines with the following structure:
type control-flag module module-arguments
For example, a rule definition (without module arguments) available in the file /etc/pam.d/sshd, which does not allow non-root logins when available / etc / nologin is:
account required pam_nologin.so
1. How to manage PAM groups and controls on Linux
PAM authentication tasks are cataloged into four independent administration groups, each of these groups handling different aspects of a user's request for a restricted service.
A module is associated with one of these types of administration groups as follows:
account
This value offers the services for the verification of the account with aspects such as expiration of the user's password or if the user is allowed access to the requested service.
authentication
With this value, a user is authenticated and user credentials can be configured.
password
They allow updating user passwords and are integrated with PAM authentication modules
session
This is responsible for managing the actions executed at the beginning and end of a session.
PAM object files are hosted in the following directory / lib / security / or / lib64 / security depending on the architecture used.
The control indicators supported in PAM are:
requisite
With this indicator the fault instantly returns control to the application, indicating the nature of the failure of the first module.
required
It is indicated that all modules are necessary for libpam to be executed correctly and return the success to the application
sufficient
This module leads to an immediate and correct return of the application, in this case the failure of this module is omitted.
optional
The success or failure of this module is generally not recorded in this indicator
There are other values ​​such as:
include
There, all lines of the type are included based on the specific configuration file as an argument for this control.
substack
Includes all lines of the given type of the specified configuration file as an argument for this specific control.
2. How to verify that a program is compatible with PAM on Linux
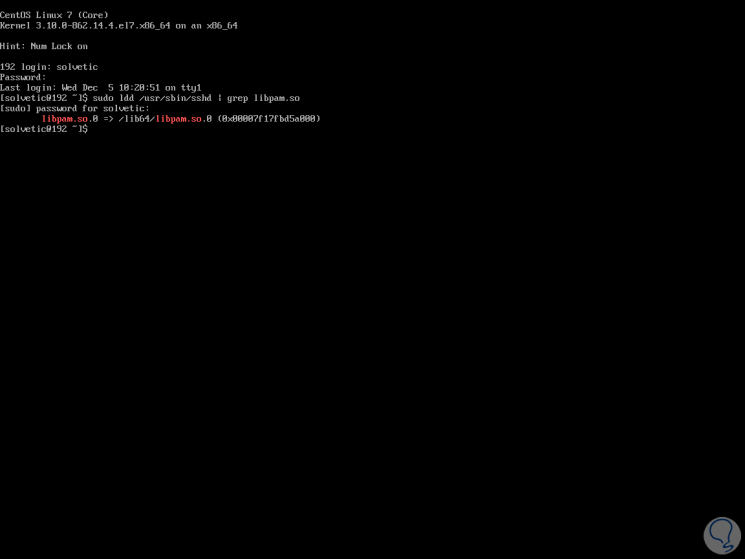
To implement PAM in an application, it must have been written and compiled specifically to use PAM, to check if that application is compatible or not, for example, SSH, we will execute the following:
sudo ldd / usr / sbin / sshd | grep libpam.so
3. How to restrict root access through SSH with PAM on Linux
PAM can be used to disable root user access to a system through SSH and login programs and this helps increase system security options.
If we wish to do this, we will use the module /lib/security/pam_listfile.so which gives us the option to limit the privileges of specific accounts.
Step 1
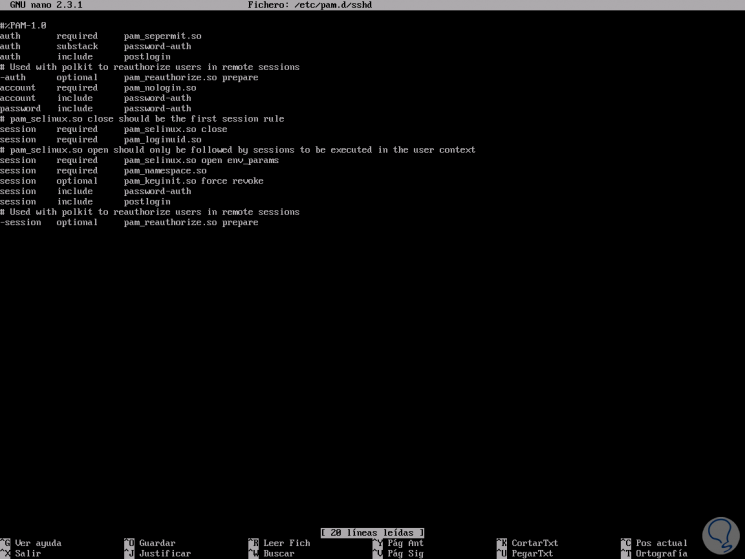
To perform this action, we will access the file /etc/pam.d/ as follows:
sudo nano /etc/pam.d/sshd
OR
sudo nano /etc/pam.d/login
Step 2
There we will see the following:
Step 3
For this case we will add the following lines at the end:
auth required pam_listfile.so \ onerr = succeed item = user sense = deny file = / etc / ssh / deniedusers
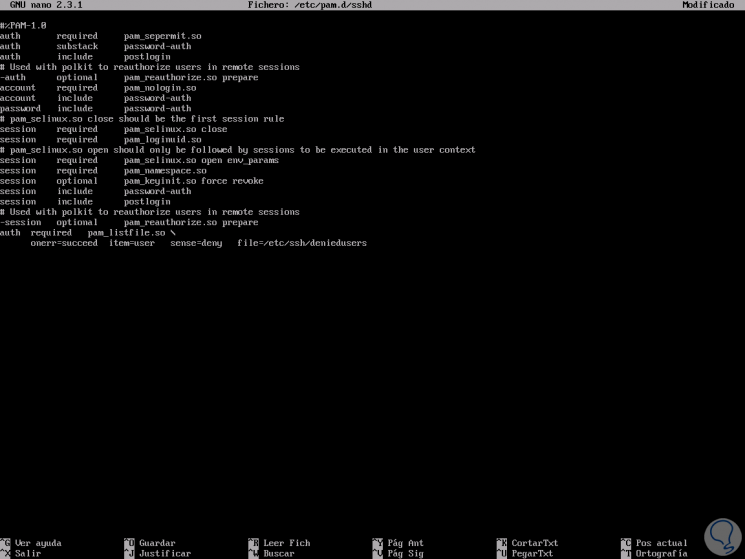
In this case the following parameters have been added:
auth
It is the type of module to use
required
It is a control indicator with which, if the module is used, it must be approved or the general result will have an error regardless of the status of other modules.
pam_listfile.so
It is a module with which it is allowed to deny or allow services based on an arbitrary file.
onerr = succeed
It is the argument of the module.
item = user
It is the argument of the module in which it is indicated what is listed in the file and that must be verified.
sense = deny
It refers to the argument of the module in which the action to be performed is specified if it is in the file, if not, the opposite action is requested.
file = / etc / ssh / deniedusers
It is the argument of the module in which a file containing one element per line is specified.
We save the changes using the Ctrl + O keys and exit the editor using Ctrl + X.
After this we must create the file / etc / ssh / deniedusers and add the root user in it and then assign the respective permissions:
sudo chmod 600 / etc / ssh / deniedusers
4. How to configure advanced PAM on Linux
A special value is the default value in PAM, whereby all values ​​are not explicitly mentioned, therefore, the N value corresponds to the return code of the function invoked in the module for which the line is defined.
The action has some arguments such as:
ignore
If this action is used with a stack of modules, the return status of the module does not generate an application return code.
bad
Indicates that the return code should be considered as indicative of the failures of the module used.
die
It fulfills the same bad function, but it is capable of finishing the module stack and PAM immediately returns to the application.
okay
This value tells PAM that the system administrator will use this return code directly to the return code of the complete stack of modules.
done
It fulfills the same role of Ok, but it can end the module stack
N
(an unsigned integer): equivalent to ok, but you can jump over the next N modules in the stack.
Reset
When using this parameter, all memory of the module stack status is cleared and restarted with the next module stacked.
Each of the PAM base words, required; requisite; sufficient and optional, have an equivalent expression in terms of the [...] syntax, with which it will be possible to write more complex rules such as:
required
[success = ok new_authtok_reqd = ok ignore = ignore default = bad]
requisite
[success = ok new_authtok_reqd = ok ignore = ignore default = die]
sufficient
[success = done new_authtok_reqd = done default = ignore]
optional
[success = ok new_authtok_reqd = ok default = ignore]
Step 1
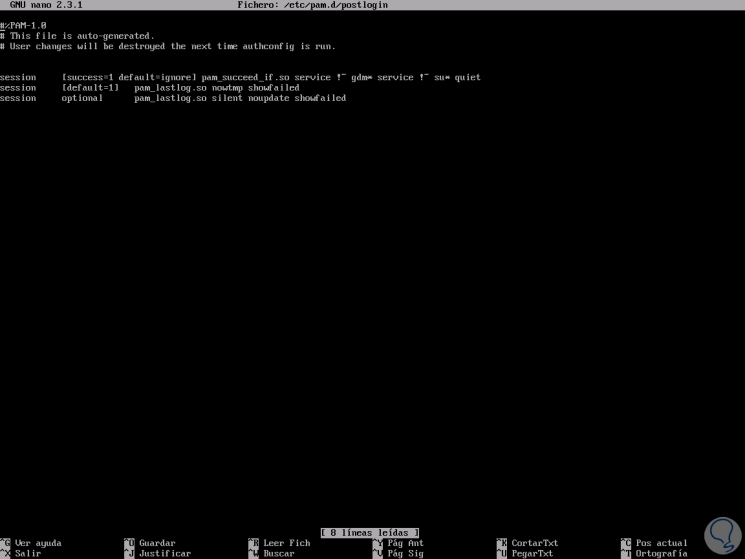
For example, in CentOS 7 we can see the rules of the PAM file by executing:
sudo nano /etc/pam.d/postlogin
Step 2
If we access the file:
sudo nano /etc/pam.d/smartcard-auth
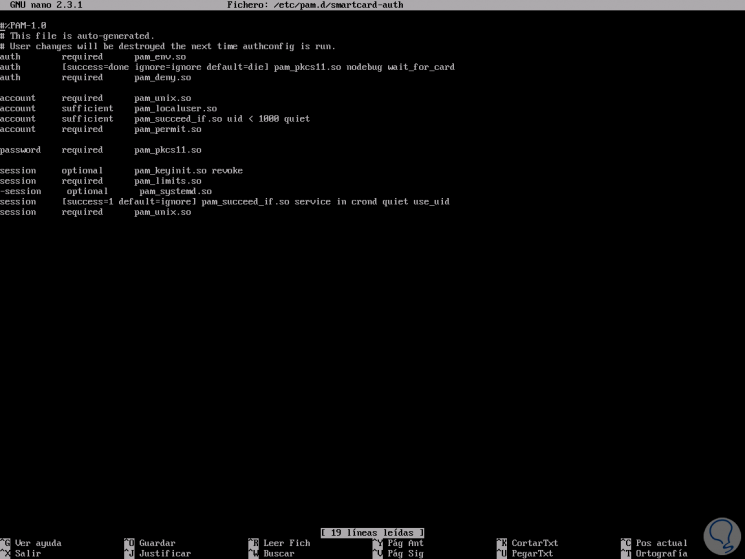
To access more PAM help we can run:
man pam.d
With PAM it will be possible to create or edit rules for better administration of authentication processes in Linux.