One of the most used connection methods for its security and compatibility levels is the SSH connection . This guarantees us a secure connection for data transfer. In order to improve connectivity and performance levels through SSH, we have a resource called OpenSSH through which the entire connectivity process will be managed in a much clearer and more concrete way. Through this tutorial we will see how to install OpenSSH on Linux to have better options when it comes to protecting the transfer of information ..
What is OpenSSH?
OpenSSH has been developed to act as a connectivity tool through remote login using the SSH protocol. When OpenSSH is implemented, all traffic is encrypted in order to eliminate potential hazards such as connection hijacking, unauthorized access and other attacks. In addition to this, OpenSSH offers a set of secure tunnel capabilities, multiple authentication methods and various configuration options so that we have the opportunity to make better use of it.
OpenSSH tools
The OpenSSH suite consists of the following tools:
- Remote operations which are done using ssh, scp and sftp.
- Key management through ssh-add, ssh-keysign, ssh-keyscan and ssh-keygen.
- The service side is composed of sshd, sftp-server and ssh-agent.
OpenSSH features
Within the different OpenSSH features we find:
- Open source project with free license.
- OpenSSH is available under a BSD license.
- Various crypto options such as AES, ChaCha20, RSA, ECDSA, Ed25519 and more.
- Forwarding X11 which allows the encryption of X Windows remote traffic, thus preventing attackers from accessing remote xterms or inserting malicious commands.
- Port forwarding which allows the forwarding of TCP / IP connections to a remote machine through an encrypted channel.
- Better levels of authentication which protect against various security failures.
- SFTP client and server support.
OpenSSH news
The recently released version of OpenSSH is 7.9 which comes with a series of new features and new features such as:
- It is now allowed to specify most of the port numbers through getservbyname service names.
- The IdentityAgent configuration directive may accept environment variable names.
- Supports signaling sessions through the SSH protocol.
- It is compatible with "ssh -Q sig" to list the supported signature options.
- Supports key revocation lists (KRL) to revoke the keys specified by the SHA256 hash.
Next, we will see how to install OpenSSH on Linux.
Previous requirements
For OpenSSH to work in the correct way we must have the following:
- Zlib 1.1.4 or 1.2.1.2 or higher
- LibreSSL or OpenSSL> = 1.0.1 <1.1.0
1. Install OpenSSH client on Linux
Step 1
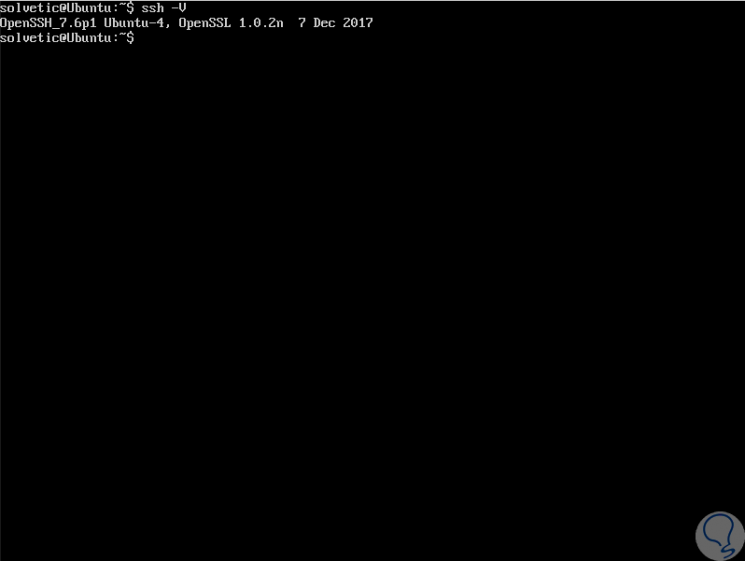
Before starting we will check the version of SSH installed with the following command:
ssh -V
Step 2
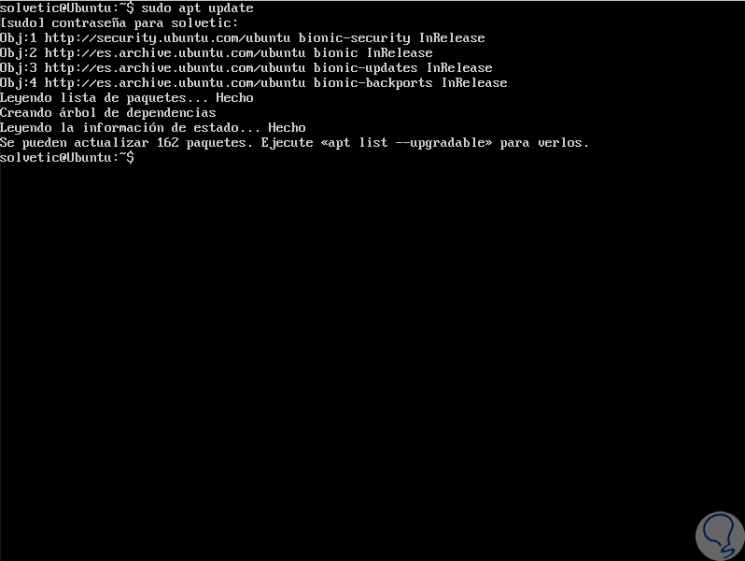
Now we are going to install the dependencies which are the development tools or essential elements of compilation, as well as other necessary packages, for this we execute one of the following commands:
CentOS / RHEL 7/6
sudo yum group install 'Development Tools' sudo yum install zlib-devel openssl-devel
Fedora
sudo dnf group install 'Development Tools' sudo dnf install zlib-devel openssl-devel
Step 3
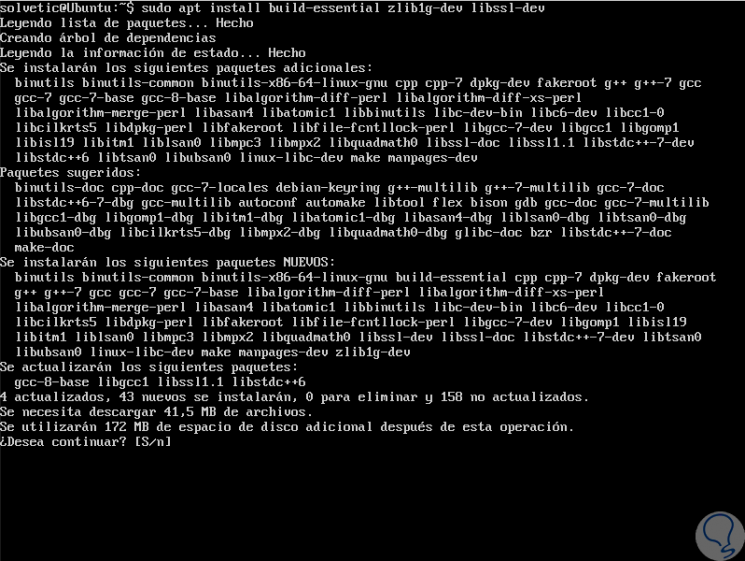
There we enter the letter S to confirm the download and installation of OpenSSH.
sudo apt install build-essential zlib1g-dev libssl-dev
2. Install OpenSSH server on Linux
Step 1
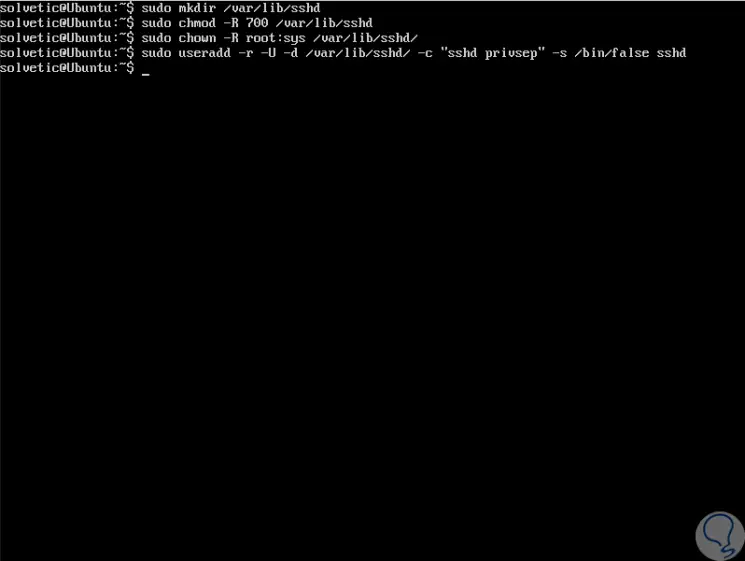
Now we are going to create an environment to install the OpenSSH version 7.9 server, for this it will be necessary to create a new user and system group called "sshd", then secure it with chroot, we execute the following lines:
sudo mkdir / var / lib / sshd sudo chmod -R 700 / var / lib / sshd / sudo chown -R root: sys / var / lib / sshd / sudo useradd -r -U -d / var / lib / sshd / -c "sshd privsep" -s / bin / false sshd
Step 2
The parameters used are:
Create User
Useradd is instructed to create a system user
-r
Create group
The creation of a group with the same name and group ID is indicated.
-OR
Indicate Directory
The user directory is specified
-d
add comment
It is used to add a comment.
-c
Indicate shell
The user's shell is specified.
-s
Step 3
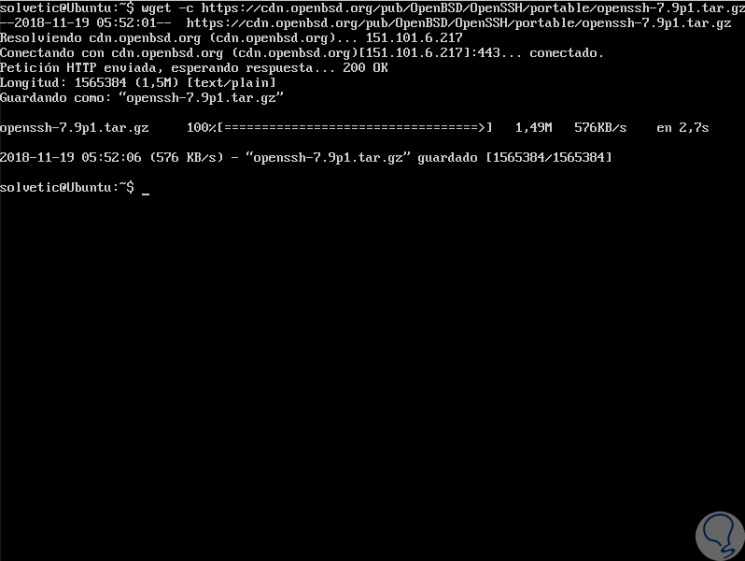
Once this is done, we will download the latest version of OpenSSH by running the following line:
wget -c https://cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-7.9p1.tar.gz
Step 4
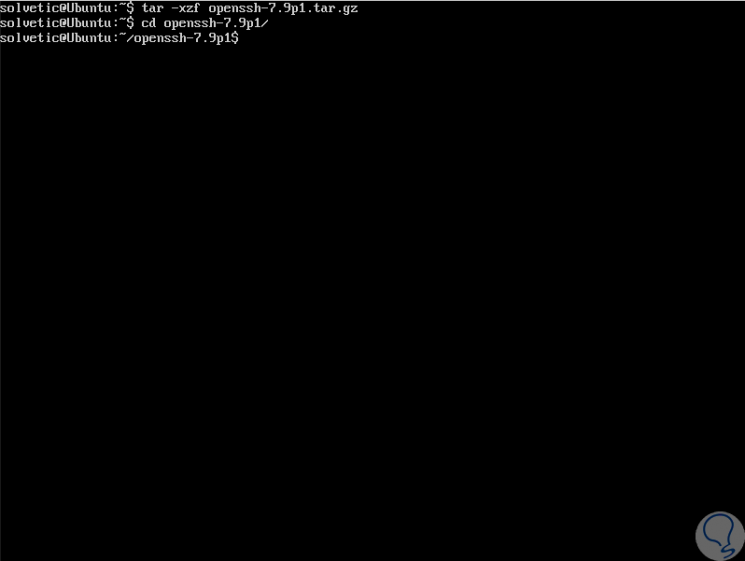
We proceed to decompress the downloaded file and access the new directory:
tar -xzf openssh-7.9p1.tar.gz cd openssh-7.9p1 /
Step 5
The next step is to build and install the OpenSSH server through the options "--with-md5-passwords, --with-privsep-path and --sysconfdir", which will install all the files in the / usr / local directory / which is the default PREFIX installation. To see all the available options we will execute “./configure -h†and from there it will be possible to customize the installation as necessary:
./configure -h
Step 6
If we want to enable PAM and SELinux support, we will add the
–with-pam and
–with-selinux options like this:
./configure --with-md5-passwords --with-pam --with-selinux --with-privsep-path = / var / lib / sshd / --sysconfdir = / etc / ssh make sudo make install
Step 7
Finally, we can verify that we have the latest version of OpenSSH by running:
ssh -V
Step 8
The OpenSSH configuration files are in the following paths:
User settings
User-specific ssh client configurations (alias ssh) and keys are stored in this directory.
~ / .ssh / *
System wide configuration
Refers to the ssh client configurations of the entire system.
/ etc / ssh / ssh_config
Sshd service configuration
The sshd service configurations are hosted there.
/ etc / ssh / sshd_confi
We can see how OpenSSH is a practical alternative to manage and have better options when using SSH..