Windows 10 integrates a security functionality that allows you to protect the information stored on the hard disk which can be sensitive or confidential. As we know, we are continually exposed to various types of attacks of all kinds not only on the network but through internal means. To give us an additional security option Windows 10 integrates BitLocker which makes use of an encryption that has been developed as a data protection feature of the operating system. Bitlocker encryption is a function that allows us to have data protection against the exposure of external hazards in information theft. Thanks to TPM we will help, even if someone tries to modify or manipulate our computer or try to decipher our keys, the key that is saved in TPM is needed..
BitLocker is responsible for raising the level of protection if it is used with version 1.2 or later of the Secure Platform Module (TPM). In this case, the TPM is a hardware component which is installed on most new computers and works simultaneously with BitLocker to help protect both system and user data. In this way we can guarantee that the equipment has not been altered when the system was offline.
Now, a vulnerability was recently discovered in the hardware encryption process implemented on various solid state or SSD hard drives. In which, when hardware encryption is available, it is not verified whether the encryption is susceptible to failures and software-based encryption is disabled , which results in vulnerable data. The failure is mainly that SSD hard drives allow access to encryption keys. This causes the central security base to be violated and thus exposes the data and information on the disk, which is not feasible at all..
The Microsoft development group recommends disabling hardware encryption and switching to BitLocker software encryption in order to increase security levels. That is why TechnoWikis will explain how to achieve this.
To keep up, remember to subscribe to our YouTube channel! SUBSCRIBE
1. Check the status of BitLocker in Windows 10
Step 1
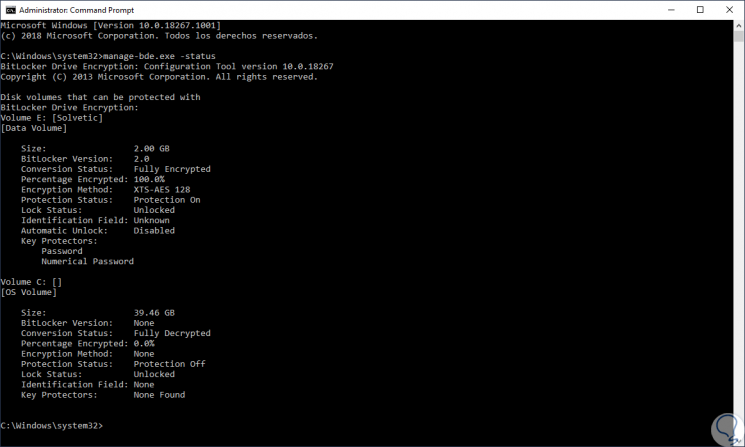
The first step to take will be to validate the current status of BitLocker encryption and for this we must access the command prompt as administrators and there execute the following:
manage-bde.exe -status
Step 2
When executing this command we will see the following result where we find specific details of BitLocker as. To check if encryption is active, we must look at the line "Encryption method" or "Encryption Method" which can be with hardware encryption or AES encryption.
- Encrypted percentage of the media or device
- Automatic unlock and more
2. Disable BitLocker from PowerShell in Windows 10
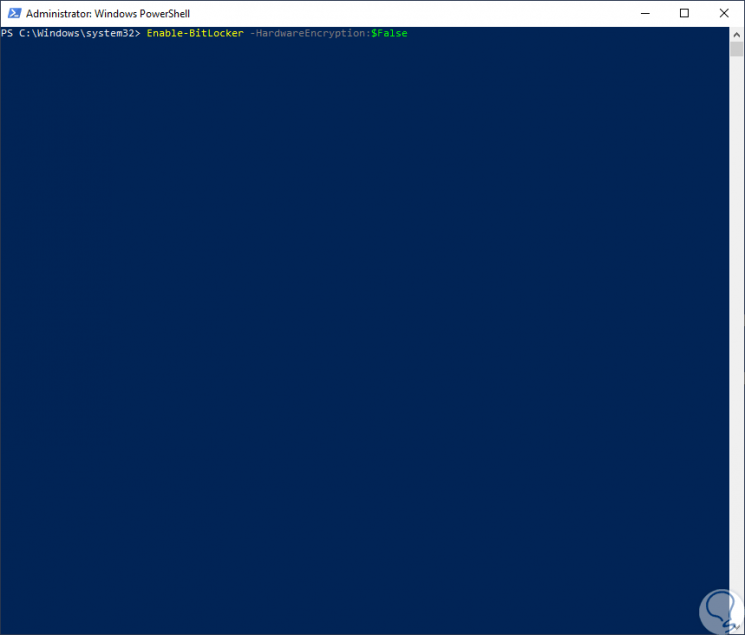
To perform this process, we access Windows PowerShell as administrators and execute the following. There we press Enter to confirm the action.
Enable-BitLocker -HardwareEncryption: $ False
3. Disable BitLocker from Group Policies in Windows 10
Step 1
This option applies to the Pro, Enterprise and Studio editions of Windows 10 and for this we must use the following key combination and execute the following:
+ R
gpedit.msc
Step 2
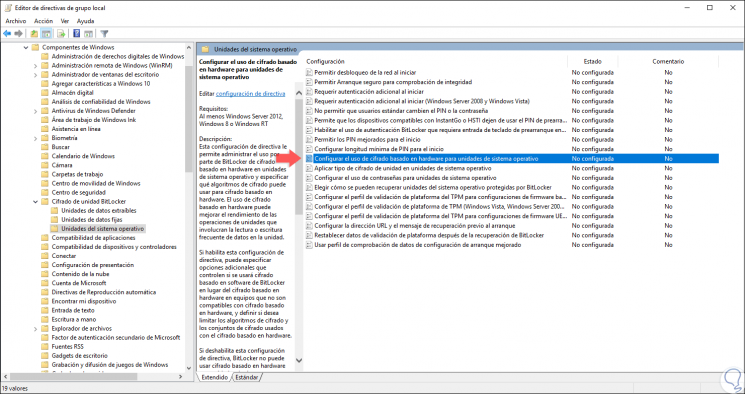
In the displayed window we will go to the following route:
- BitLocker Drive Encryption
Step 3
There we will locate the policy called “Configure the use of hardware-based encryption for operating system unitsâ€:
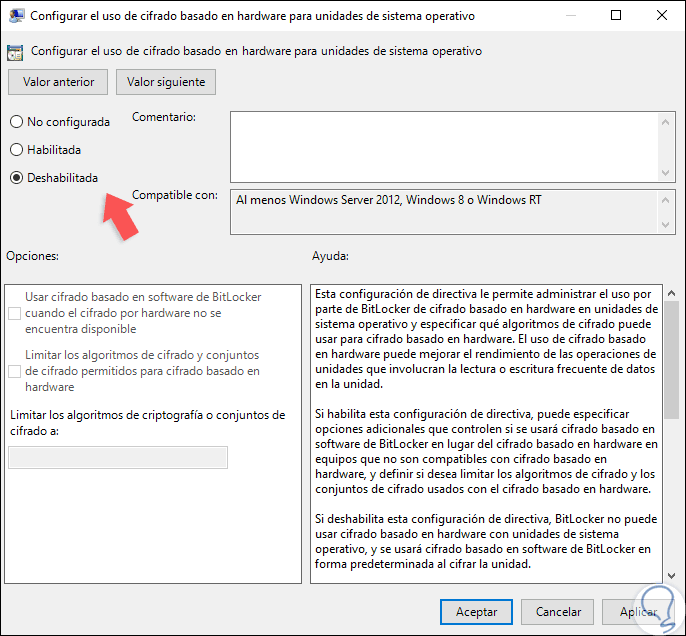
Step 4
We double-click on it and in the displayed window we activate the “Disabled†box. Click on Apply and Accept to save the changes.
4. Disable BitLocker from Registry Editor in Windows 10
Step 1
This method is compatible with all editions of Windows 10 and for use we must combine the following keys and execute the "regedit" command
. + R
Regedit
Step 2
In the displayed window we will go to the following route:
HKEY_LOCAL_MACHINE \ SOFTWARE \ Policies \ Microsoft \ FVE
Step 3
In case the FVE key is not available, we will right click on the Microsoft key and select the “New / Password†option and assign the name FVE:
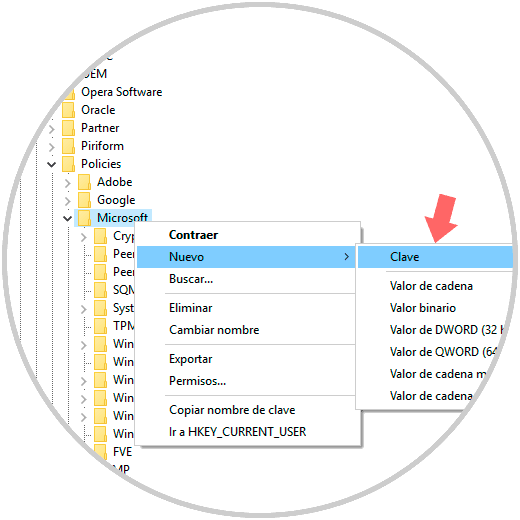
Step 4
Now, in any free place the FVE key will right click and select the option “New / DWORD Value (32 bits)â€:
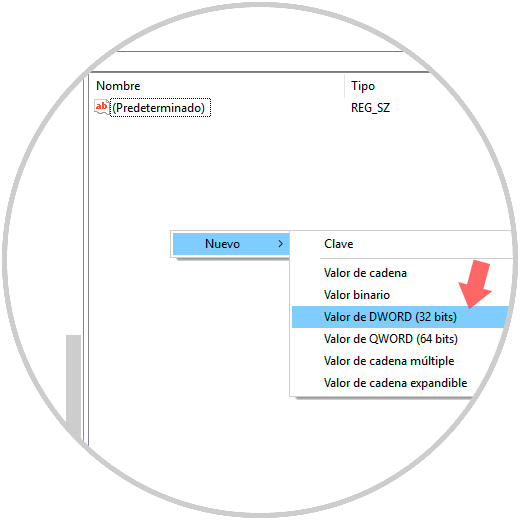
Step 5
This new value will be called “OSAllowedHardwareEncryptionAlgorithmsâ€:
OSAllowedHardwareEncryptionAlgorithms
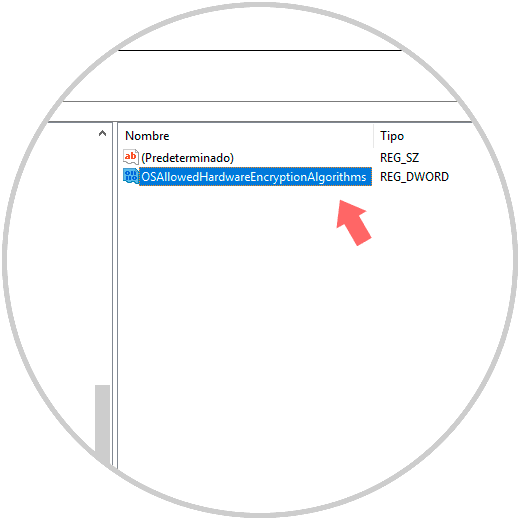
Step 6
We will double-click on it and in the Value data field we set the number 0. Click on OK to save the changes.
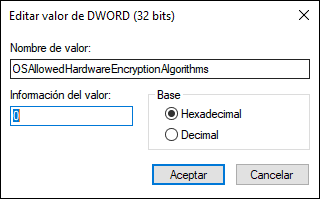
Using any of these methods it will be possible to disable BitLocker encryption and avoid this vulnerability on some SSDs..