Security is one of the key pillars in all operating systems since the information that is worked on, whether it is the user's or not, can be compromised at any time due to the thousands of attack options that exist both internally and externally. external and network, in the case of Ubuntu we have a series of tools that have been developed to help mitigate and prevent these threats and one of them is Metasploit..
Metasploit allows the user to carry out tasks such as vulnerability verification, manage security assessments and improve the security levels of both the system and the company itself. In some cases, Metasploit is written in the Ruby language in order to modernize and streamline its various tasks, this project has more than 900 different exploits with which it is possible to carry out these test actions on Linux. If you also want to know what a command is throwing, you can even save command results in Ubuntu text and thus know what it has given.
Metasploit Tasks
In this case, Ubuntu, with Metasploit it will be possible to carry out tasks such as:
- Perform scans as well as gather information from a computer using utilities like Nmap.
- Software designed to access administrator privileges is available on operating systems such as Microsoft Windows and Linux.
- Possibility to identify and explore security vulnerabilities that are published in the CVE system.
- It will be possible to install backdoors through the payloads module, let's remember that a backdoor is a malicious code to steal confidential information from the user.
- Trace removal function using methods to erase the attacker's fingerprint.
Metasploit Components
The main components integrated in Metasploit are:
- msfconsole – This is the command line interface.
- Modules: they are support modules such as exploits, scanners and more for comprehensive work.
- Tools – As the name suggests they are standalone utilities for vulnerability scanning, vulnerability impact assessment or penetration testing and more.
TechnoWikis will teach you how to install Metasploit on Ubuntu..
How to install Metasploit on Ubuntu
Step 1
We open the terminal and there we install the Curl utility to download from the web:
sudo apt install curl
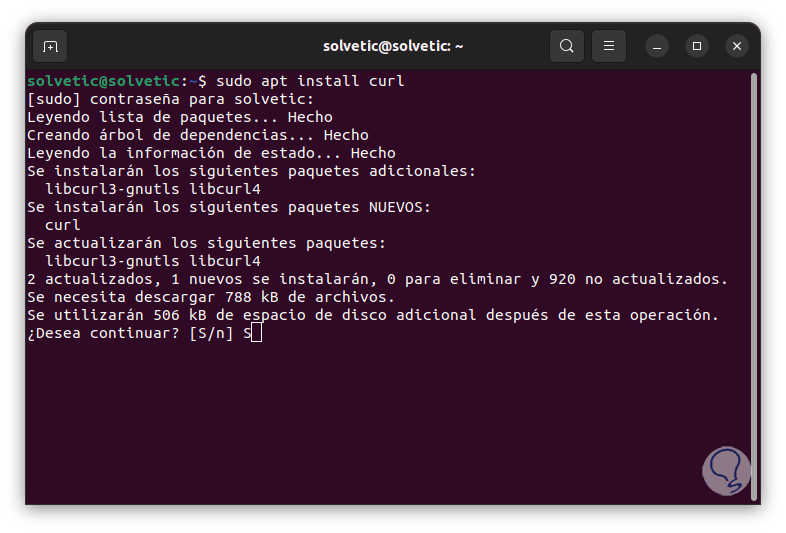
Step 2
We enter the letter S to confirm the download and installation:
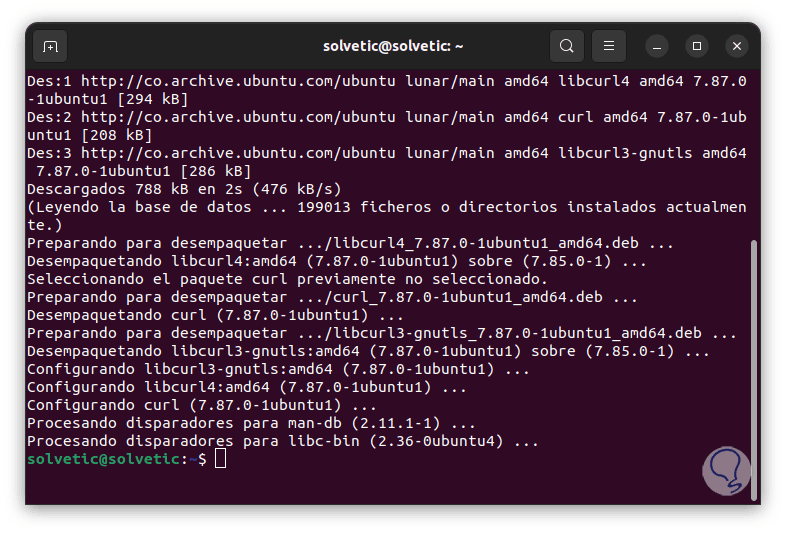
Step 3
Now we will execute the following line to install the Metasploit installation script:
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && chmod 755 msfinstall && ./msfinstall
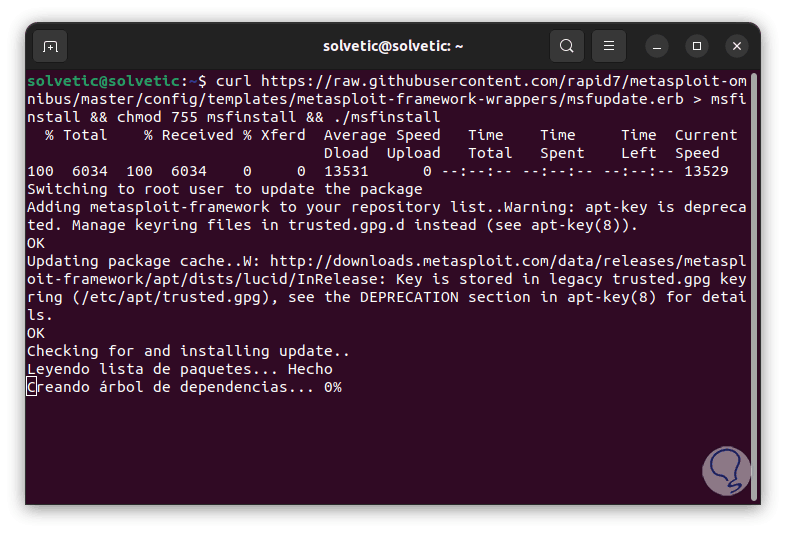
Step 4
The utility installation process will automatically begin:
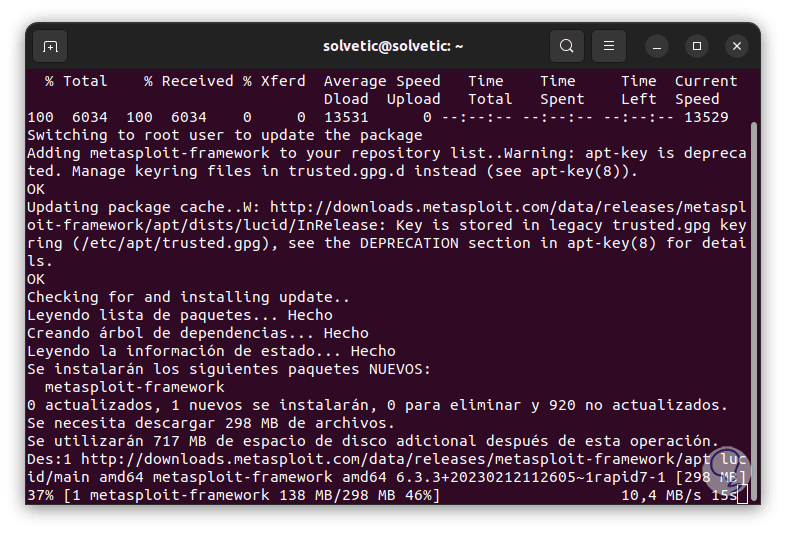
step 5
After this the installation process will start unpacking each package:
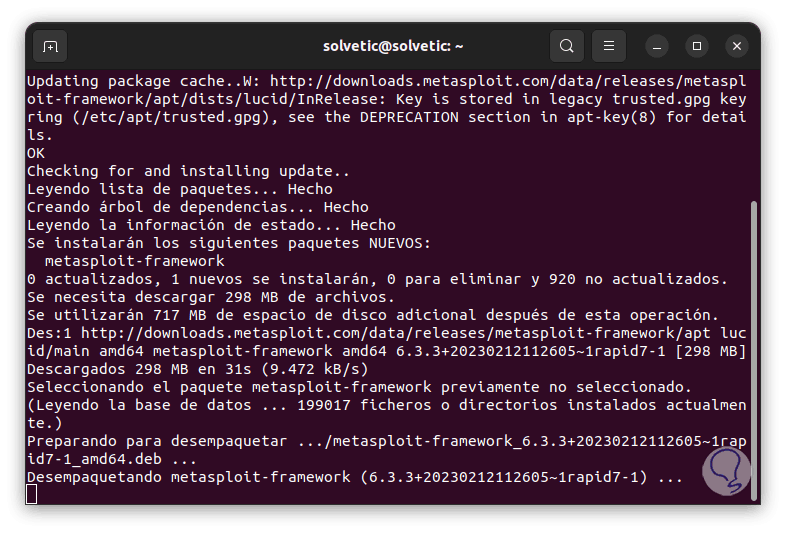
step 6
We hope that this process will come to an end:
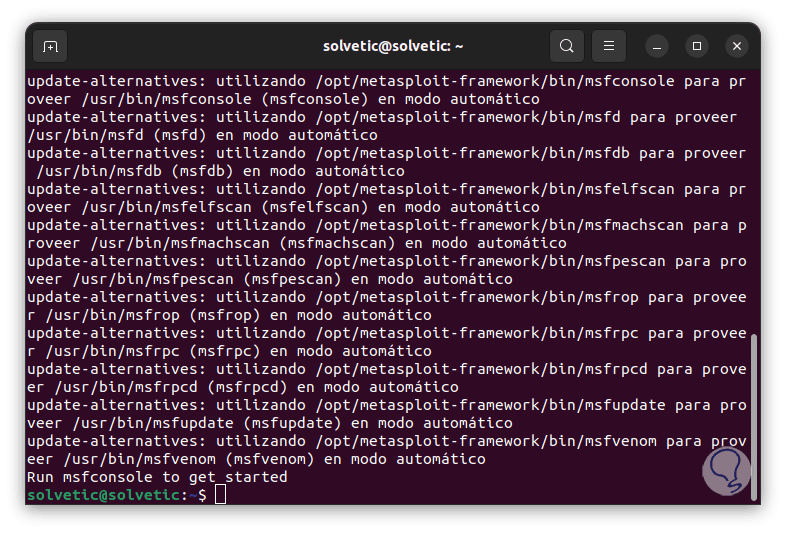
step 7
In the final part we can see that msfconsole is ready to be used. Now in the terminal we execute "msfconsole", we will see the following:
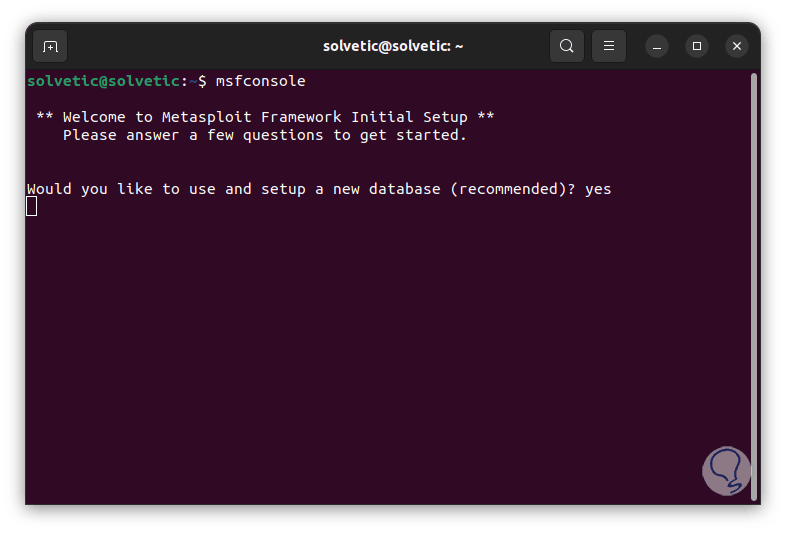
step 8
There we enter the word "yes" to create a new database, now we can start the web service:
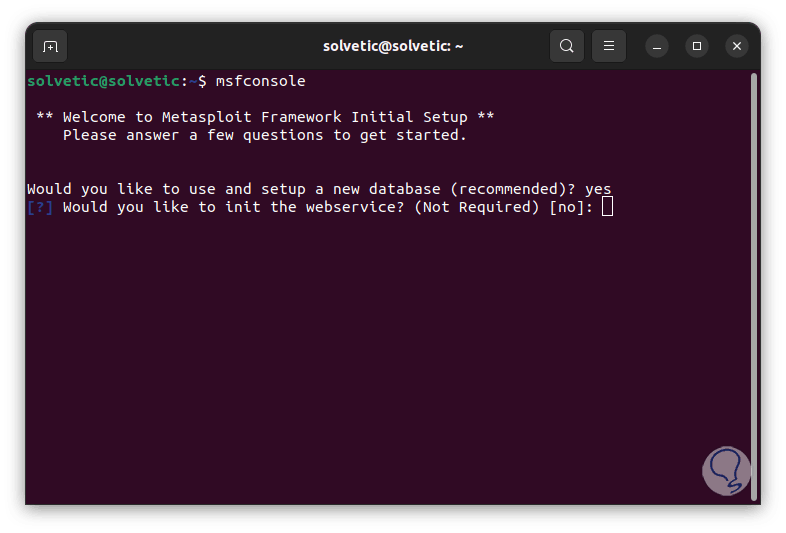
step 9
The installation process will continue:
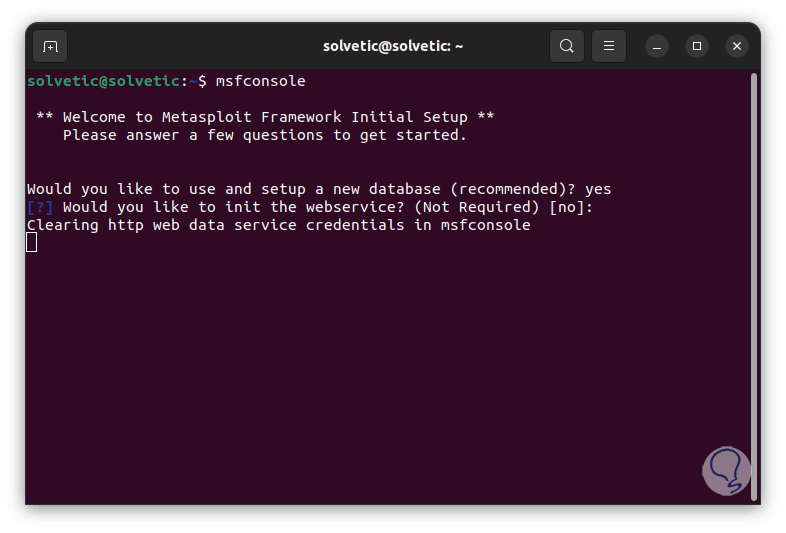
step 10
We wait for each Metasploit component to be installed on Ubuntu:
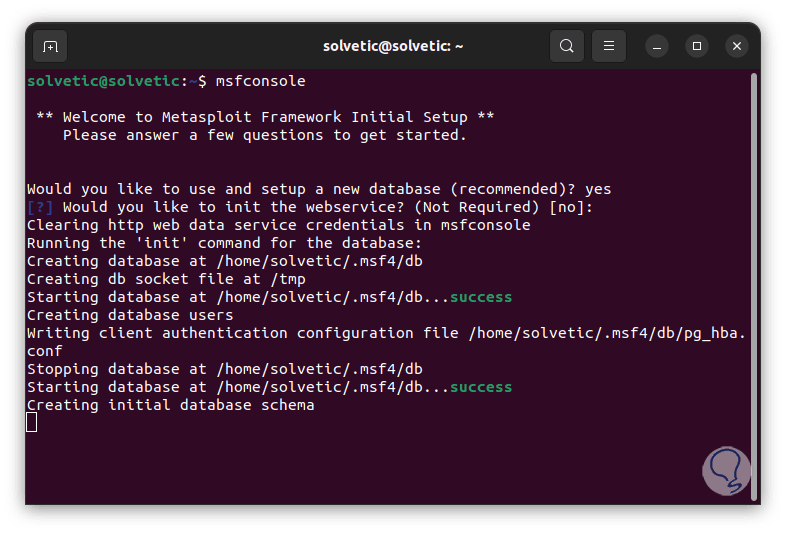
step 11
We can see that the initial configuration has been finished:
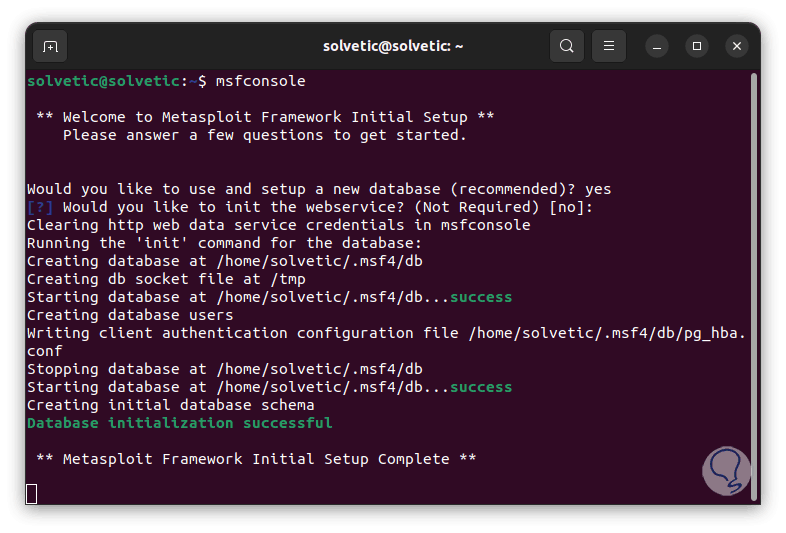
step 12
Now it will lead to the start of the Metasploit console:
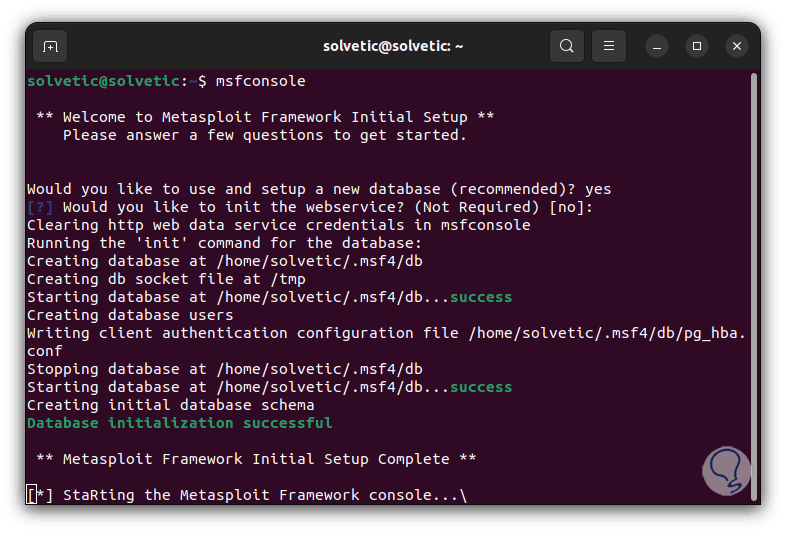
step 13
We hope that this process will come to an end:
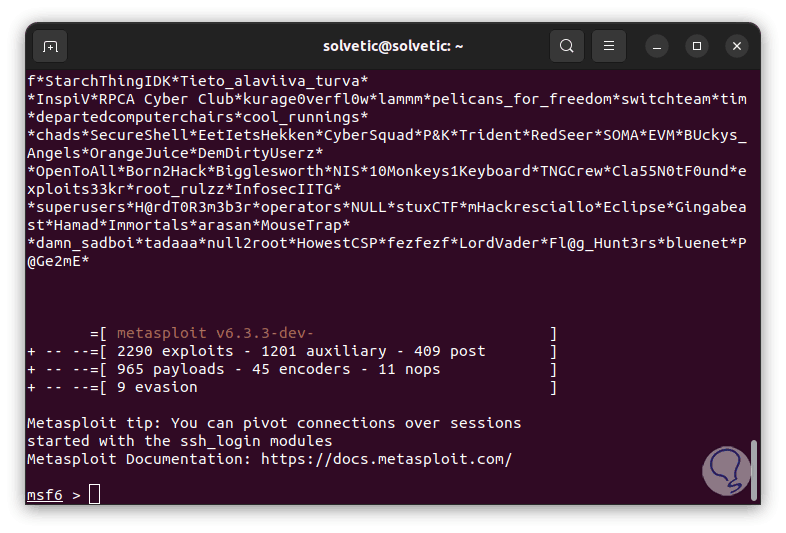
step 14
An evaluation of vulnerabilities will be done automatically in the system:
step 15
In this process we can see some columns:
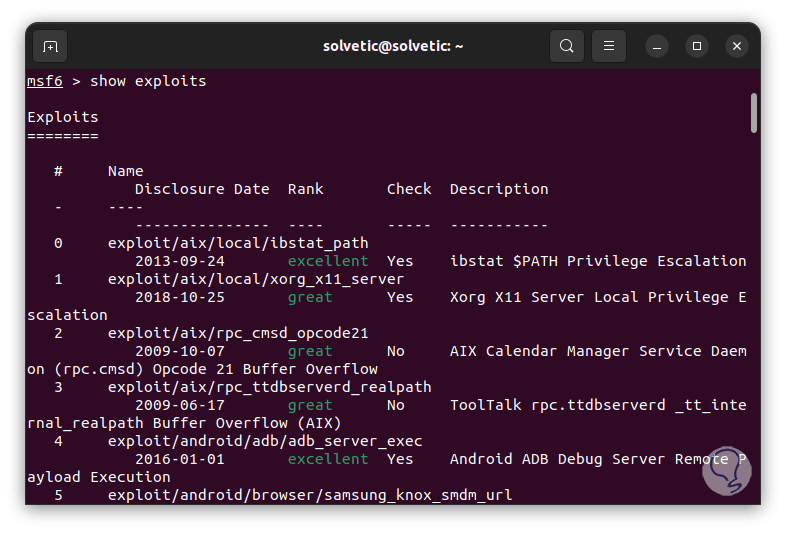
step 16
There we find specific details such as:
- Description of the exploit
step 17
Remember that an exploit is a piece of code from which a vulnerability can act on a system.
Metasploit Parameters
There are a series of parameters to use with Metasploit from the console, these are:
- get: access the value of a context-specific variable
- cd: allows you to change the current working directory
- connect: allows establishing communication with a host
- history: displays the history of commands used
- route – routes traffic through a session
- set: takes care of setting a context-specific variable to a value
- clearm: clears the stack of modules
- loadpath: look for and load modules from a path specified by the user
Metasploit is a valuable tool to know the vulnerabilities present in the system and thus be able to take extra and necessary security measures.