It is important to explain in the company the different roles that make up Information Security and responsibilities applied to each of them, their differences, etc..
Apart from the fact that we explain the different profiles in charge, it is important to emphasize that it will depend a lot on the size of the company. There are cases such as small companies (startups) that the CEO himself or a member of the C-Suite must be responsible for company security. As it grows, these positions may be delegated.
We know the importance that exists today in the digital area regarding the execution of the business of the companies to have a good and well applied computer security of the same, so being clear about all these profiles, standards and responsibilities is a vital point. in order to understand information security at the company level and who should manage it correctly..
As we said before, it does not matter if you are a small, medium or large company, in the end it is logical and it is necessary to take into account these information security points in order to grow robustly without significant risks that affect the production and business of the company. company, and may even sink it. (in case of abandonment and not taking into account anything more than the basics regarding information security).
Let us initially explain the different roles that are linked in a more or less important part to the management and execution of the Information Security of companies.
1 Roles and responsibilities in Information Security
The Roles and responsibilities in the area of Information Security are very important to understand where any company can have well located to deal with these points to take into account such as information security, computer security, physical security of the company and security of the data. Key points today that must be dealt with by professionals in this area, well prepared for these tasks.
CEO (Chief Executive Officer)
You are the CEO of a company. Manager and general leader of the company. It is usually seen a lot used at the startup level but generally affects all companies.
It is an important position to push the importance of Cybersecurity and give it value to be implemented within the company. We can say that it is a vital point for the promotion of Information Security in the company and everything that entails. Although the CEO does not have the main objective of focusing on the company's computer security, he must understand and appreciate the importance of its good implementation and be able to guarantee that the company has the adequate resources and organizational structure to effectively manage security of the information. He can help along with the board of directors, as outlined below, so that the information security of the company is linked with the commercial objectives, business and the priorities that the company has.
CEO is the person in charge of making important or necessary hiring decisions for team personnel (depending on the size of the company, you can delegate part of these terms, but what is certain is that important positions always go through this person).
If it is important for your company, it must be a CEO who gives you a push and free rein to the execution of Cybersecurity controls. In addition to allowing risk delimitation so that Cyber threats do not affect the same scale of damage depending on where they occur within the Company. In other words, it manages and it is interesting and important to be correctly aware from above of the risks that can occur at the IT Security level in the company. If we add that he may have advanced knowledge in this area of IT Security, it would be a two-in-one, because he will know how to value and apply from above the organization an important point of support for the area of the team that has to implement security measures..
As an important point that you can push hard from your position as CEO, it is to apply and support the Cybersecurity culture applied to your company, it is usually called "IT Security Organizational Culture" where its importance is promoted to all employees and it will favor a suitable communication, execution and follow-up to achieve the success of avoiding a good number of risks in the use of company information.
CISO (Chief Information Security Officer)
In a quick plan, he is responsible for the IT Security (information security) of the company. Within his security tasks and responsibilities, he has the following:
- Responsible for information security throughout the company.
- He is the person in charge of establishing information security policies and strategies to safeguard the company's information and data. Including the responsibility of the Internal Cybersecurity Auditor.
- Oversees the implementation of security controls and measures, and ensures that the company complies with applicable laws and regulations to avoid potential fines and reputational violations.
- He is the person in charge of uniting and connecting the Information Security of the company with the positions such as CSO (if any) and if there is no CSO, he would be in charge of transmitting it to the C-Suite of senior management (CEO, CMO, CFO etc.).
The connection between both parties, of C-Suite with the professional or professionals in charge of this point (as is the case of CISO or CSO), are vital for the good and agile implementation to be aligned with the two important points in this scenario that are :
- Information Security of the company well applied and continued.
- Apply these IT Security rules taking into account the business strategy and business points of the company itself.
Summarizing: CISO can also be in charge of transmitting and being a bridge between IT professionals and senior management (especially if there is no CSO). Not forgetting business continuity. Being able to speak clearly and understandably about the importance of Security issues without technicalities with Management, in addition to also being a point of support for IT professionals who execute security on their team, understanding and helping its correct implementation. Correctly choosing the techniques and correct execution of those changes that will be applied in the company's information security approach.
CSO (Chief Security Officer)
He is responsible for the security at the general level of the company, this covers the physical security of the company with the security of the information (IT security) of the same. He takes a broad approach to company security.
If this position exists in the company, it is one of the points of union in this regard with C-Suite and in many cases, being a more specialized CISO, it can also enter into this responsibility. In some companies it is important to note that the profile of CSO (Chief Security Officer) can be the same as CISO (Chief Information Security Officer).
The CSO is in charge of controlling, checking and coordinating active security implementations that exist throughout the organization. He is also in charge of carrying out and establishing security policies and is in charge of coordinating with those responsible for different areas of the company to guarantee that security is taken into account and used by all employees of the different departments, always taking into account the Key points where you have to focus more risk control.
The CSO is responsible for ensuring that the company addresses and complies with the laws and regulations related to Information Security and Physical Security issues that are mandatory for the company to comply with.
What are the differences between CSO and CISO?
One of the questions that many of you can ask yourself is the one exposed that we are going to solve in detail below.
For making clear the points that may exist between both professions. We are going to detail the differential points in case there are both positions in an organization.
The CSO (Chief Security Officer) and the CISO (Chief Information Security Officer) are two distinct leadership roles within an organization. It is true that your responsibilities may be related and sometimes overlap. It is also true that in some companies there is only one of these two profiles (because it is not necessary to expand it so much, it will depend on the size of the organization and the importance they give to this point of company Security and Information Security).
The major differences between both profiles are presented below:
- The CSO is responsible for the overall security of the company (physical and information). CISO is in charge and is responsible for the security of the company's information (not the physical part).
- The CSO responsibility profile includes oversight and coordination of implementations that apply to the enterprise-wide approach to security through Enterprise Security policies, procedures, and risk management. In addition to compliance with applicable laws and regulations related to security as we will explain a little later.
- The CISO responsibility profile is focused on information security specifically. For this, carrying out tasks such as the identification, evaluation of information security risks, application of policies, procedures and internal audits related to information security.
- CSO reports directly to the C-Suite group (CEO, COO, CMO etc.). The importance and position of CSO will be equal to the dependence and importance that the company gives to the point of physical and digital security of a company's information.
- CISO usually reports to the CIO (Chief Information Officer), also to the CSO (it depends on the size and organizational form of each company).
Summarizing: If the size is large and the company's information security management is a very important point, the CISO profile is necessary at the same time as the CSO. If it is a medium-sized company in many cases, a CSO can have CISO responsibilities and vice versa in the general security of the company (physical and computer). And there have even been cases of companies having CISOs focused on information security and the CSO target being one of the company's Management roles in the C-Suite area.
It is important to comment that CSO or CISO (especially CSO) can also help prepare the company to meet the international security standards that each organization needs or requires, depending on their industry together with regulations depending on the laws applicable to the area. where your headquarters are installed and where your business applies.
CIO (Chief Information Officer)
CIO is responsible for the planning, implementation and strategic management of information technology in the company. This profile is not focused exclusively on the Security of the company, but has responsibility for managing the IT infrastructure and the company's systems are safe and protected against threats and vulnerabilities.
It is logical and normal for the CIO to coordinate with both the CISO and CSO so that together they can ensure that the policies, standards and procedures decided to implement regarding the company's computer security end up being successful as these profiles are coordinated among all of them.
Penetration Testers
The Penetration Tester Role, which is also called "pentester" or "ethical hacker", is an information security professional (who can be internal or external to the company) whose task is to evaluate, measure, audit and improve the security of an organization's computer systems and networks.
The real goal is to detect vulnerabilities in company systems, networks, applications and devices before attackers (hackers) do so and can break into business systems.
Once the vulnerabilities in the company have been identified by the Pentester, it is time to correct these detected vulnerabilities. It is recommended that part of your security team become a Pentester and also, in some cases, have a specialized profile in this form of business security verification.
There may be more Security profiles that depend on those described above, we only leave a few more cases of this type:
- Security Administrator: Responsible for implementing and maintaining the security policies and procedures established by the CISO. Configuration and administration of security hardware such as firewalls, detection systems, intrusion prevention, antivirus and server security.
- Information security specialist: Information security specialists focus on specific areas of computer security, such as risk assessment, cryptography, authentication and authorization, or application security.
- Network Security Engineer: This role is responsible for securing the company's network, including network devices, servers, and communication systems. Network security engineers are responsible for monitoring and protecting the network against threats and vulnerabilities.
- Security auditor: The one in charge of security auditor is responsible for reviewing and evaluating the effectiveness of security policies and controls implemented in companies. They are in charge of carrying out internal and external audits to verify that everything is being fulfilled effectively.
- Application security analyst: It is a role in charge of ensuring that the applications developed in the company are secure. These application security analysts review source code, identify potential vulnerabilities, and work with developers to fix security issues.
- Incident response specialist: When a security incident occurs, such as a data breach or cyber attack, incident response specialists are responsible for investigating and managing the situation. It can be internal or external for these cases.
- Information security trainer: This is a role in charge of communicating and training your company's employees on the necessary computer security to avoid security holes in companies, such as teaching the creation of secure passwords, email detection phishing etc. In these cases, it is true that companies usually put these documents online so that employees can read this type of training.
2 International Computer Security Standards
Some international information security standards that companies can obtain to demonstrate that they comply with company information security guarantees and are well known are the following:
ISO/IEC 27001
International standard of the best known for the management of information security. It depends on the Information Security Management System (ISMS), which provides a standard to correctly manage the security of the company's information. Basically and summarizing, obtaining this ISO/IEC 27001 certification confirms that an organization has implemented a correct ISMS and currently applies good practices regarding the security of company information. It can give a better image and confidence to the outside, for customers, suppliers and other parties interested in the evolution of the company.
We also leave you access to the official page of ISO 27001 if you want more direct information on the standard.
Important points regarding preserving the security of information by complying with ISO 27001 are the following:
- Confidentiality.
- Integrity.
- Information availability.
- Minimization of information security risks.
One of the objectives of this ISO is undoubtedly to guarantee the cybersecurity of information systems, so profiles such as the CSO or CISO of a company make sense that they want to apply this standard as part of their objectives to improve the security of the information of the company they are managing at that security level.
AENOR is a well-known company that regularly applies this international standard (regarding information security) to companies. Therefore, it is interesting to show you his explanation in this regard to understand the importance of ISO 27001.
To stay up to date, remember to subscribe to our YouTube channel!
SUBSCRIBE ON YOUTUBE
ISO/IEC 27002
This standard known as ISO 27002 provides companies with security controls that, together with the previous ISO 27001 standard, provides companies with another step to comply with more standards, techniques and practices regarding the security of information from companies that we do not enter. in detail. More information enter the official page of this standard.
NIST Cybersecurity Framework (CSF)
This international cybersecurity framework is developed by the US National Institute of Standards and Technology (NIST). It provides best practices to help organizations comply with correct cybersecurity for the company.
CSF 2.0 | Updates 2023 2024 (PDF)
CIS Critical Security Controls
Basically CIS are best practices that the company can use to strengthen its position regarding cybersecurity. These are the so-called critical security controls of the Internet Security Center (CIS), which in the end are a group of prioritized actions to protect your company against cyberattacks by improving its information security.
To stay up to date, remember to subscribe to our YouTube channel!
SUBSCRIBE ON YOUTUBE
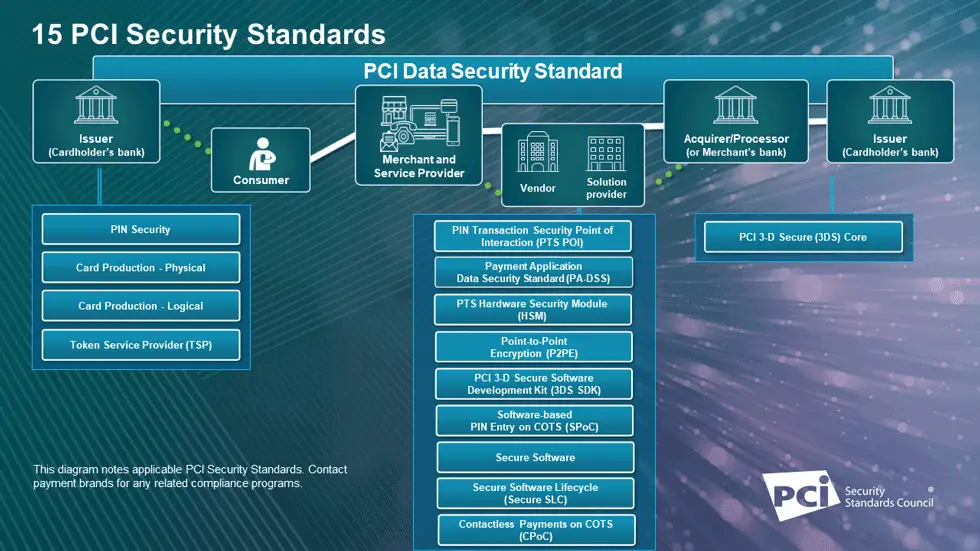
PCI DSS (Payment Card Industry Data Security Standard)
For companies that process, store or transmit payment card data, they must comply with the payment card industry data security standard, called (PCI DSS).
PCI DSS is a unified, global response to combating security breaches in payment card data. They are continuously updated, improving the standards of this industry to improve security in this regard. Depending on your business model and its size, it may or may not be interesting in your case to comply with it.
This image shows the 15 PCI security standards that are applied in the payment process. You can get more information see PCI DSS Official Page.
GDPR (General Data Protection Regulation)
(GDRP) General Data Protection Regulation is a regulation of the European Union regarding the protection and processing of personal data of EU citizens.
Basically all organizations that handle personal data of EU citizens must comply with the GDPR, within this protection there are security measures to protect this type of data of natural persons (from the EU) that companies house in what affects the processing of personal data and the free circulation of this type of data. More information on the GDPR Official Page.
There are more important regulations, depending on the type of company that can comply and may be of interest, but we have shown some of the best known and relevant internationally focused on information and data security.