There are thousands of tasks that we can carry out in macOS and some are more delicate than others, one of these is the possibility of performing a scan of the local network in order to detect intruders, find out which computers are on the local network and carry out perform management tasks..
To accomplish this task, we have the Nmap command.
Nmap (Network Mapper) has been developed as a free and open source utility with which it is possible to detect networks or carry out security audits on network infrastructures, although the initial objective of Nmap was to scan large networks, it is also we can use for scanning in small networks..
nmap
With Nmap it is possible:
- Discover networks and network inventory
- Carry out service update schedules
- Run real-time host or service uptime monitoring
- Run it on Linux, Microsoft Windows, FreeBSD, OpenBSD, Solaris, IRIX, Mac OS X, HP-UX, NetBSD, Sun OS operating systems
- It is possible to map IP filter networks, firewalls, routers using port scanning (TCP and UDP), detect operating systems, version detection, ping sweeps, etc.
nmap hits
By using Nmap it is possible to have access to:
- Packet Filters and Active Firewalls
- Hosts with live status on the local network
- Services with name and version of the application used at that moment
TechnoWikis will explain the process to scan a local network with Nmap in macOS.
To stay up to date, remember to subscribe to our YouTube channel!
SUBSCRIBE ON YOUTUBE
How to scan a local network with Nmap on macOS
Step 1
The first thing will be to open the terminal and install Nmap with the command:
brew install nmap
Step 2
There it will start downloading the necessary plugins:
Step 3
The installation process will continue:
Step 4
At the end we will see the following:
step 5
Run a simple scan to one of the Nmap databases:
nmap scanme.nmap.org
step 6
The scan will start, at the end the following will be displayed:
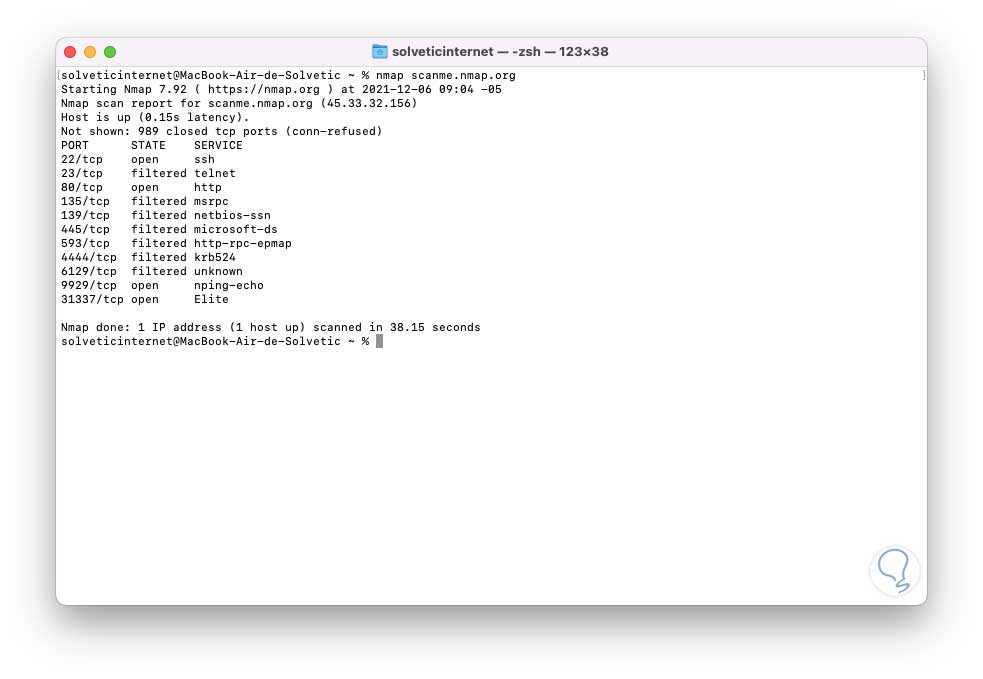
step 7
There we find:
It is possible to scan a range of ports with the syntax:
nmap 192.168.10.0/24
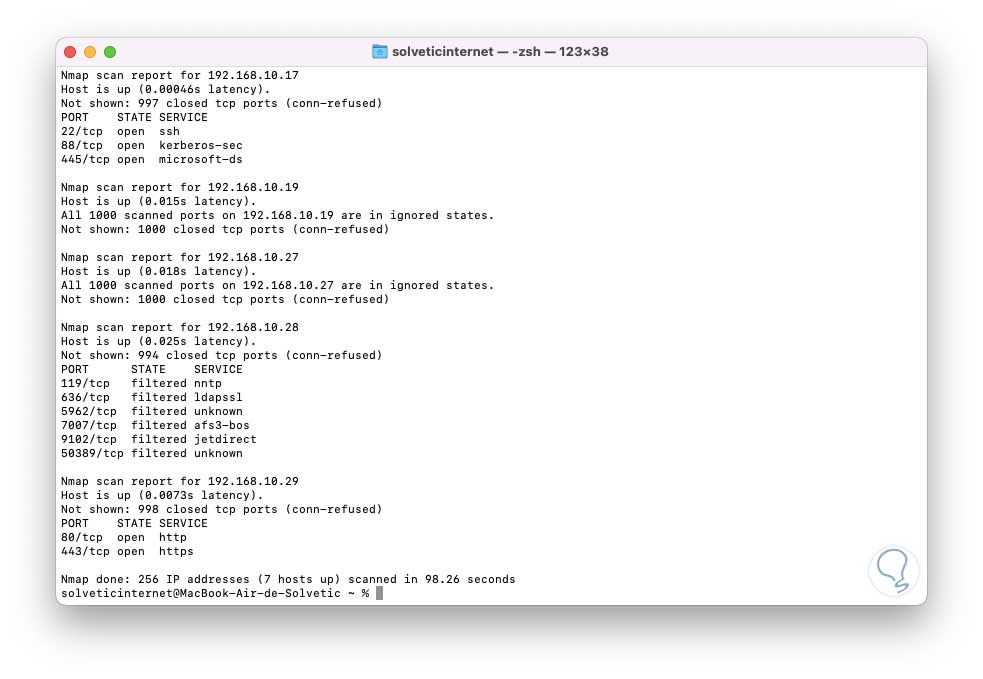
step 8
There we will see a complete summary of each device detected on the network with its details.
To find the IP addresses of the computers or routers, run:
sudo nmap -A scanme.nmap.org
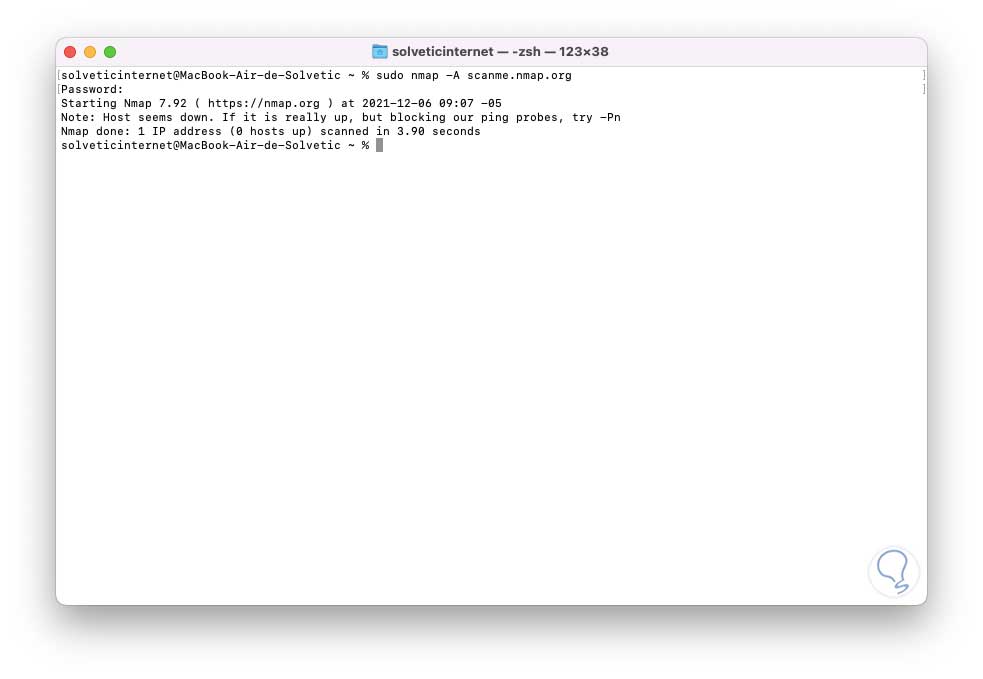
The -A parameter forces nmap to scan deeper for more information while hiding the Nmap process on the target..
Being a more complete process, it must be executed with privileges (sudo).
step 9
To scan the IP address defined for the operating system we will execute:
sudo nmap -O scanme.nmap.org
To perform the analysis silently we execute:
sudo nmap -sS scanme.nmap.org
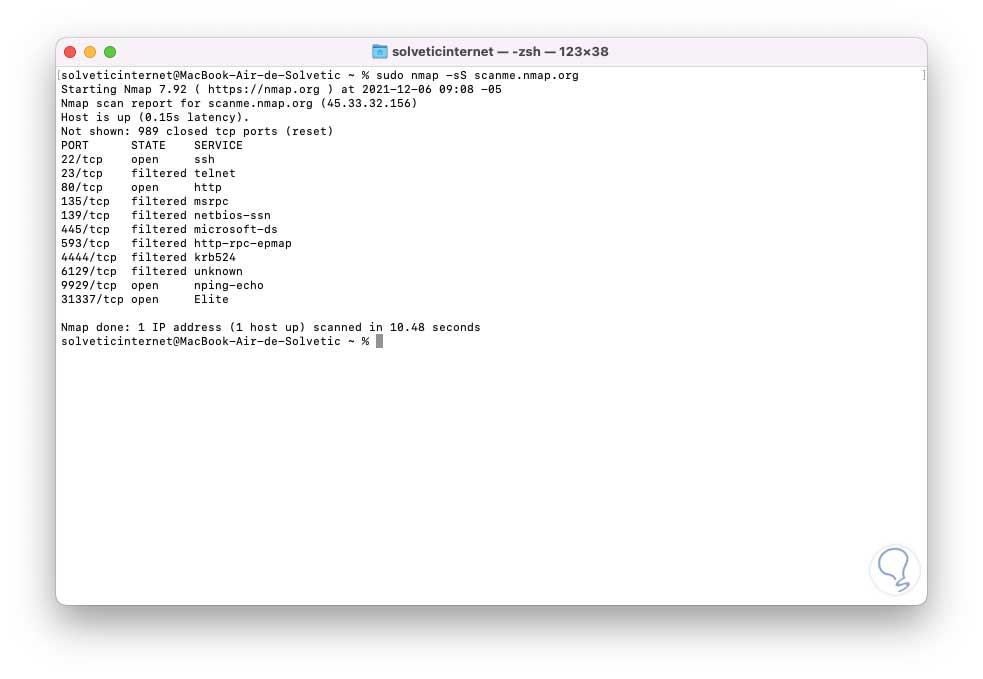
step 10
It is possible to filter the results from nmap to grep in order to get specific results, for example:
nmap scanme.nmap.org | grep "139 /tcp"
To list all the devices in the network we execute the following:
harp
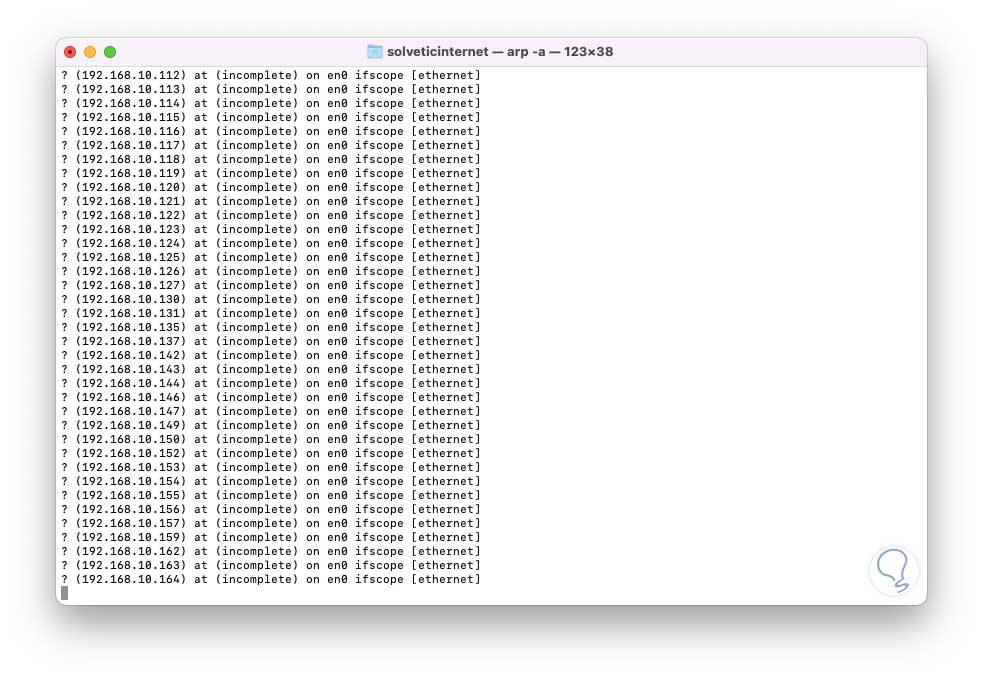
We will see as a result the IP and the MAC address in the detected equipment.
With Nmap it is possible to have a functional tool for analyzing the local network and accessing comprehensive results.