Security in the IT world will always be one of the main tasks that we must preserve and be attentive since in a digital world like today there are thousands of threats everywhere. We always think of our files and documents , but there are other elements that must also be treated even more carefully and are the files or folders of the operating system itself which if they are edited incorrectly can cause a negative and harmful impact in the system ..
macOS Mojave, has an integrated security mechanism that prevents access and editing of this type of folders using a functionality called SIP. In TechnoWikis we will explain in detail how to verify and enable or not such functionality in macOS Mojave.
What is SIP?
SIP (System Integrity Protection - System Integrity Protection), is a security technology implemented since the El Capitan edition but better functionalities have been added focused on helping to prevent any potentially malicious software from being able to modify files and folders protected in the system.
With System Integrity Protection, the root user account is restricted and the actions that the root user can execute in protected sections of the macOS Mojave operating system are limited..
Operating system protection
SIP includes protection for the following sections of the operating system:
- Applications that are preinstalled on the system
The routes and applications that can remain active are:
These directories are protected from any type of modification such as add, delete, modify, edit, move, and more, either from any administrator account or from root accounts. In case the System Integrity Protection is deactivated manually, it will be possible to have privileges to modify those directories, and for the deactivation of SIP an administrator password and boot access to a Mac are required.
The system integrity protection has been designed to allow the modification of these parts listed as protected only through processes signed by Apple and where they must have special rights to write to the system files, such as updates of Apple software and Apple installers..
Another option of System Integrity Protection is to help prevent the software from selecting a boot disk to boot and thus prevent malicious software from being installed from there.
1. How to check the status of SIP in macOS Mojave
To verify this we have two simple options.
Option 1
The first is through the terminal and to access it we have the following options:
- On the route Go / Utilities / Terminal
- Using the key combination ⇧ + ⌘ + U and in the open window select the terminal
Now, in the terminal console, let's run the following:
csrutil status
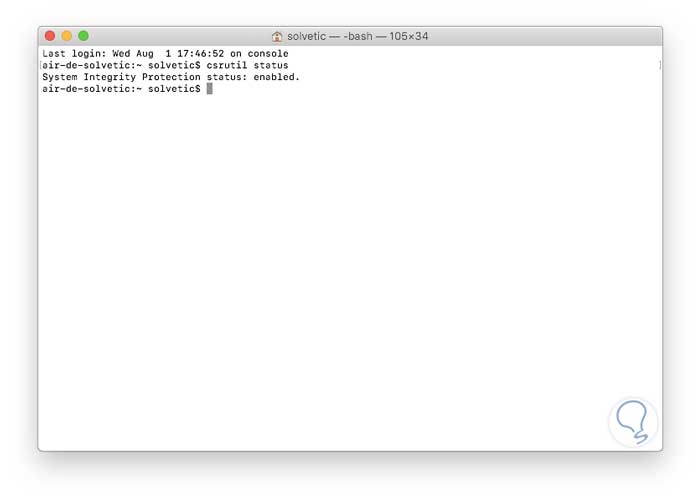
By default its status must be enabled.
Option 2
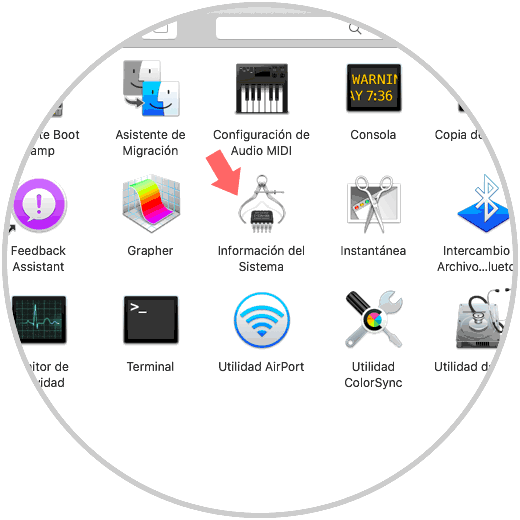
The second option to obtain this information is graphically through System Information and for this we have the following options:
- Access the system utilities and select System Information there
- Press the Option key, click on the Apple logo and select System Information there
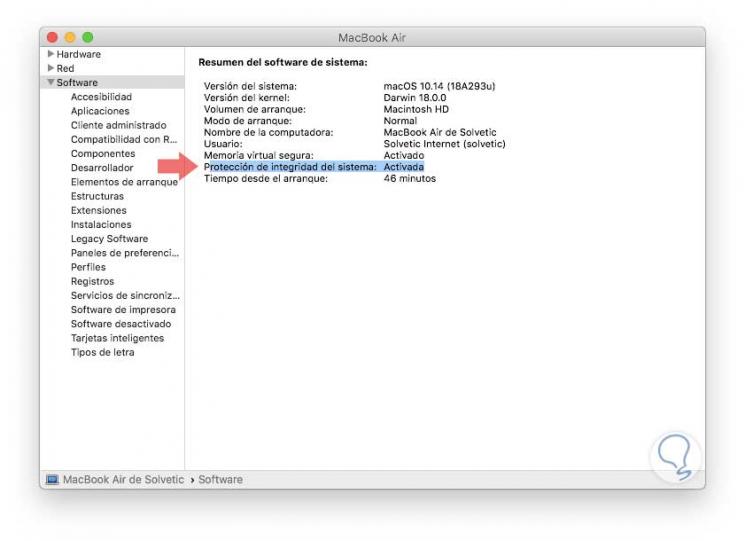
In the window that will be displayed, we go to the Software section and there we will see the current status of SIP in the System Integrity Protection line:
2. How to disable Integrity Protection of the Mac System
Step 1
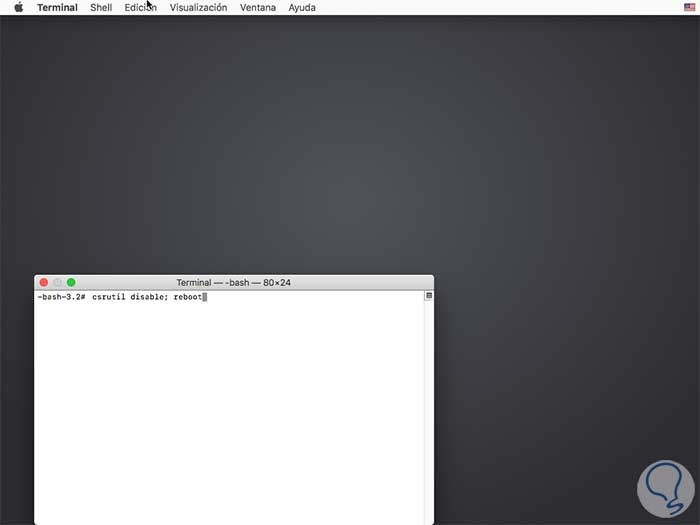
Although this is not recommended, if we want to disable SIP in macOS Mojave it will be necessary to turn on or restart the computer and during this process, press the Command + R keys until the Apple logo is displayed and in the window we will see we go to the tab Utilities and there we select Terminal:

Step 2
In the deployed console we execute the following:
csrutil disable; reboot
Step 3
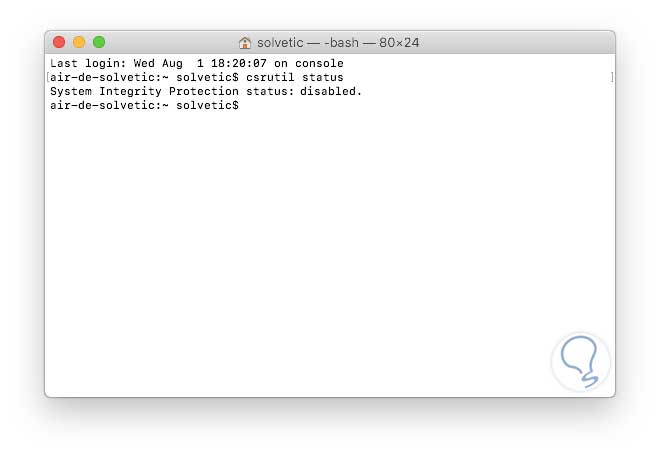
We proceed to restart the system and once we log in, we validate the status of SIP again by executing:
csrutil status
Step 4
Now we will see that its state is disabled.
If we want to activate it again, we will access using ⌘ + R during the macOS Mojave boot process and execute the following command:
csrutil enable
Thus, we can enable or not the Integrity Protection of the system in macOS Mojave in order to have the best security features for the most delicate folders of the operating system which should, if possible, not be edited.