One of the threats that frequently as IT users we have to face is virus infection which spreads in a dizzying way since there are millions of viruses in the network around each site. We have thousands of infected links, attachments that at the time of opening infect our computer and in general we are vulnerable to add a virus, independent of its type, to our computers or devices..
Something that happens frequently, both at home and in the office, is that we connect any USB media in public places, where viruses abound, and then we connect them to our computer and there we are opening a vulnerability door so that this threat is in the system.
One of the viruses that most affects the storage units are the shortcut viruses which make the files and folders full of shortcuts, but none open the original file affecting its use. Shortcut viruses take advantage of a Windows system design error which involves executing malicious code inserted in a shortcut. At the same time, these viruses hide folders or files inside the drive..
For these reasons, TechnoWikis will give a series of practical tips on how to remove these viruses either from our USB media or from the hard drive itself and thus enjoy greater security in the operating system.
1. How to remove viruses using the Windows command prompt
This method allows us to make use of the utility of the symbol of the system integrated in the Windows systems by means of which, through a series of attributes, we can easily remove the virus.
Step 1
For this, we will access the command prompt as administrators and the first step is to verify which is the letter assigned by the system to the hard disk, USB drive or SD card, for this we execute the following commands:
diskpart (Allows access to the disk management utility) list disk (List available discs)
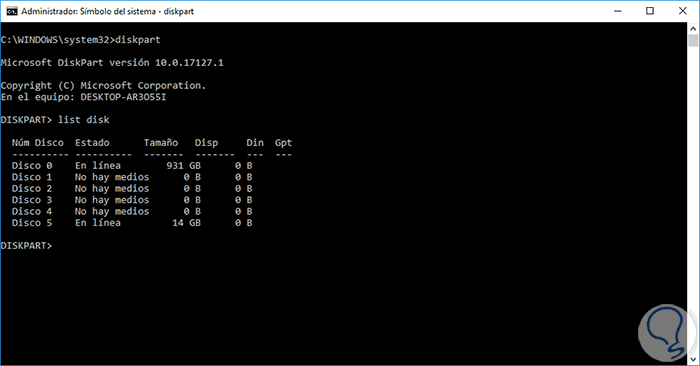
Step 2
There we can see the assigned unit or we can locate it directly in the Windows file explorer:
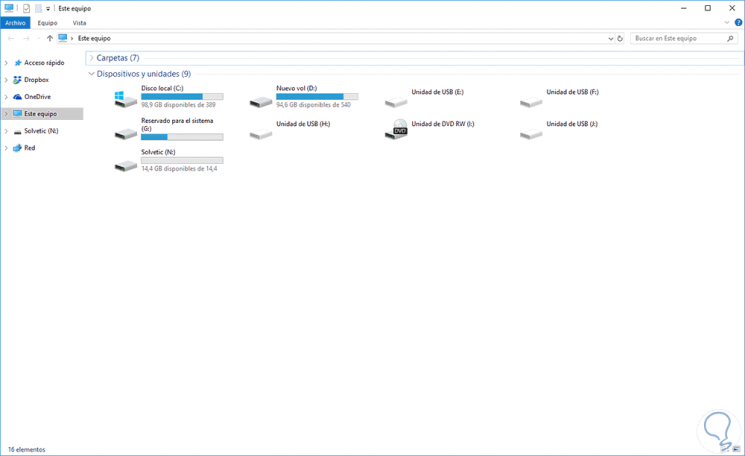
Step 3
In this case we will analyze the USB memory which is assigned the letter N, at the command prompt we execute n: to access it:
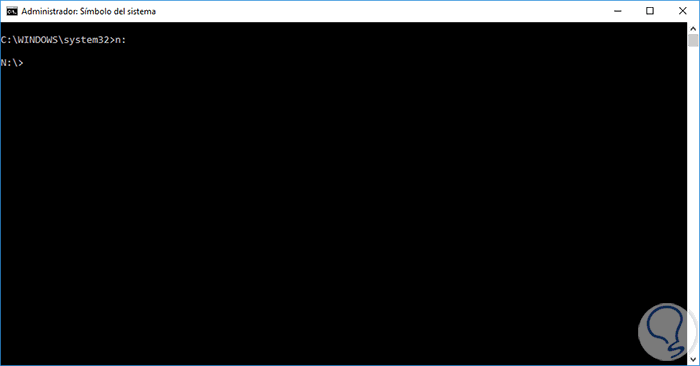
Step 4
Once we access it we will execute the following:
* lnk
Files of type .lnk are shortcuts of the Windows operating system. They are Windows pointers that point to the original files, once we delete these .lnk files, we will execute the following:
attrib n: *. * / d / s -h -r –s
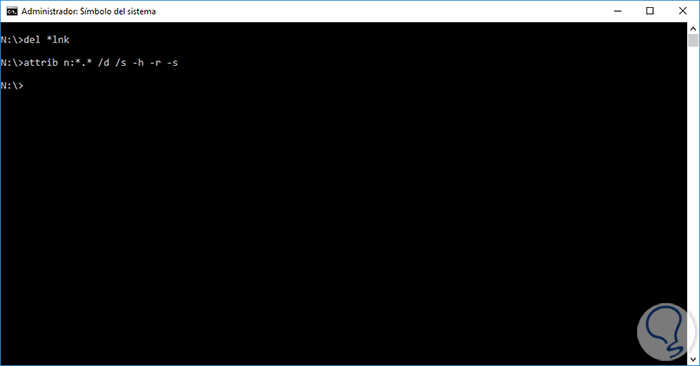
Note
Remember to change the letter by which the system assigns to our unit.
When executing this series of attributes, hidden files will be displayed in the analyzed medium and it is enough to go to it and eliminate those that we consider unnecessary..
2. How to run a scan with Windows USB antivirus software
Having installed in our system some antivirus utility, this allows us to perform a quick or complete analysis on the units in search of threats intuitively.
If you do not have it, we can use, in the case of Windows 10, the Windows Defender utility which has improved analysis and security allowing us to perform a complete analysis on any of the units of the computer and thus discard any type of threat.
To run an analysis with Windows Defender, simply go to the file browser and right click on the unit to analyze and select the option Browse with Windows Defender:
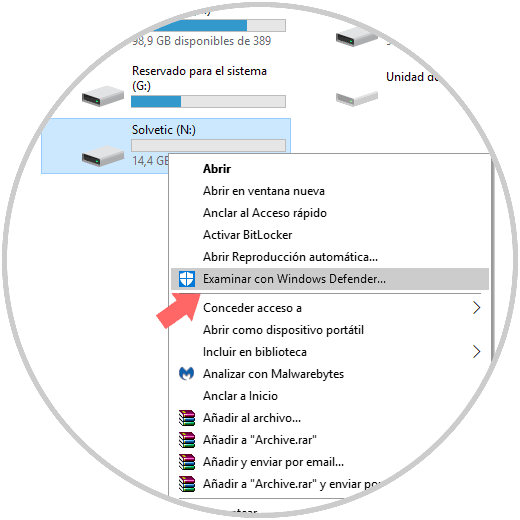
This will display the Windows Defender Security Center from where we can start the analysis.
3. How to remove shortcut viruses using free programs
There are several free utilities that give us the possibility of eliminating these annoying shortcut viruses and one of them is Shortcut virus, which we can download for free in the following link.
Shortcut virus remove
It is a portable utility which displays the following at the time of its execution:
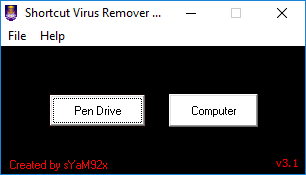
There we can select Pen Drive to analyze the USB sticks or the Computer option to analyze the hard disk.
Once we select the correct option, the following will be displayed:
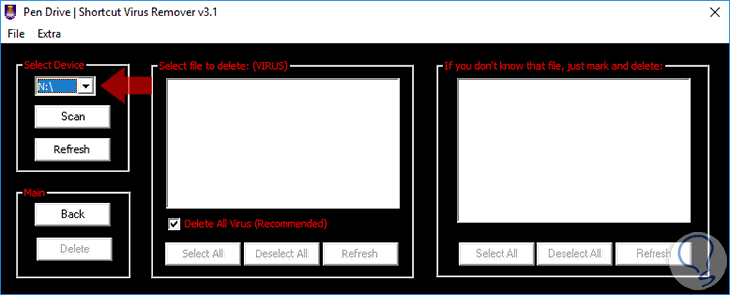
There we select the letter of the unit to be analyzed and click on the Scan button to start the analysis, as we see we can activate the Delete All Virus box to automatically remove the threats.
We have been able to know some useful alternatives to give a comprehensive and complete solution to this direct access virus and thus be able to take full advantage of the files or folders in our storage units.