One of the simplest and most used methods in the world to protect the information of a system is the use of passwords. Of course, these passwords must be complex to avoid using the current methods to discover them, when we manage a server with Windows Server 2022, the use of passwords must prevail even more since all roles, services are configured on the server and shared accesses with the entire domain..
If for some reason you have forgotten the administrator password in Windows Server 2022 , it is possible to reset it and TechnoWikis will explain how to do this in a functional way.
To stay up to date, remember to subscribe to our YouTube channel! SUBSCRIBE
How to reset Administrator password in Windows Server 2022
Step 1
We must download the ISO image of Windows Server 2022 at the following link:
Download Windows Server Insider Preview
Step 2
After this we record the image on a bootable DVD or USB and configure the server to boot from there directly in the BIOS or UEFI, when booting we will see the following:
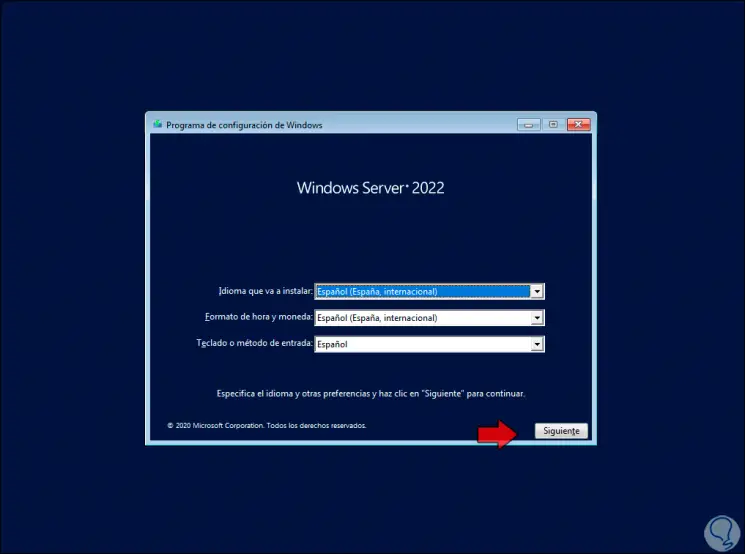
Step 3
We click on "" Next "and then we will see this:
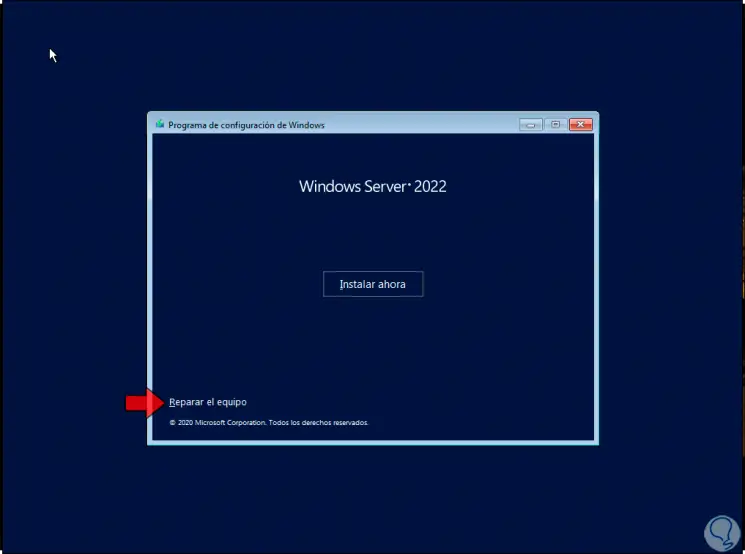
Step 4
There we click on "Repair computer" to see the following options:
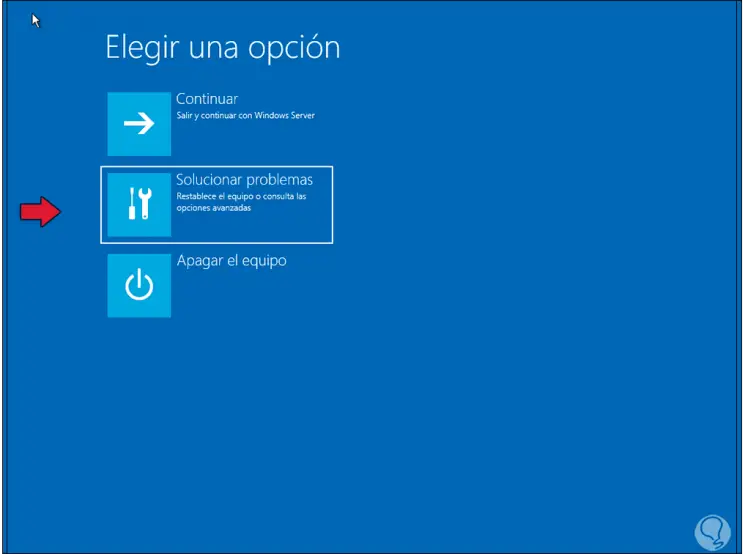
Step 5
We click on "Troubleshoot" and we will see the following:
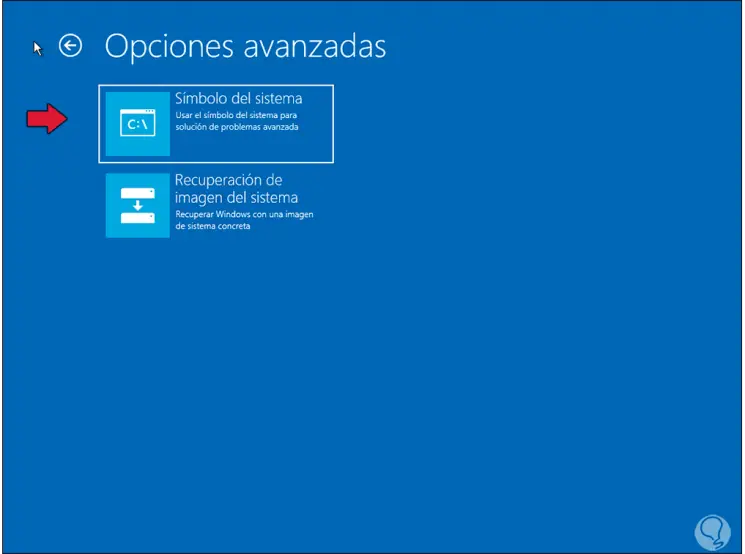
Step 6
In this case we click on "Command Prompt" to access the CMD console in advanced mode, in the console we enter ad: and use "dir" to list the content:
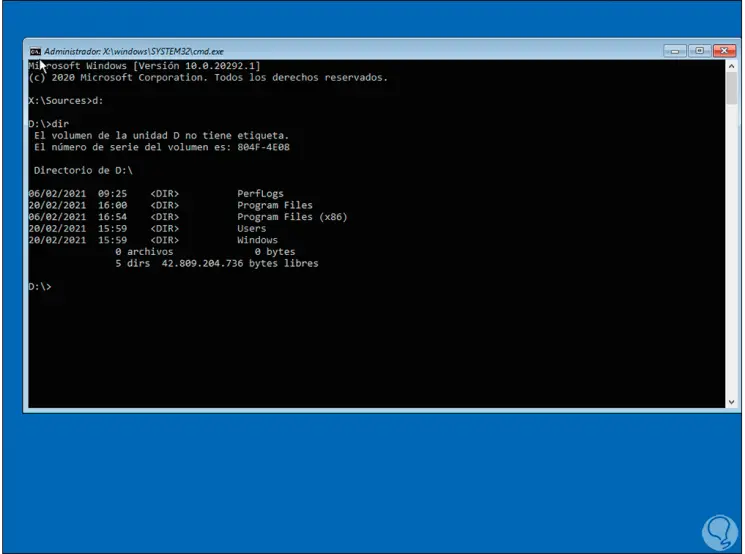
Note
in File Explorer this is drive C but in this mode it is named D.
Step 7
Now we are going to execute the following to deploy the system to use at startup:
bcdedit / set {bootmgr} displaybootmenu yes 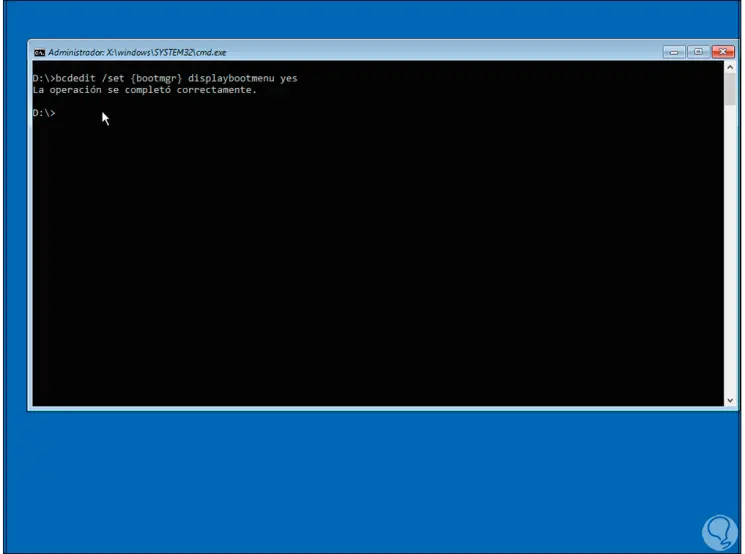
Step 8
After this we configure how long the system selection will be visible:
bcdedit / set {bootmgr} timeout 15 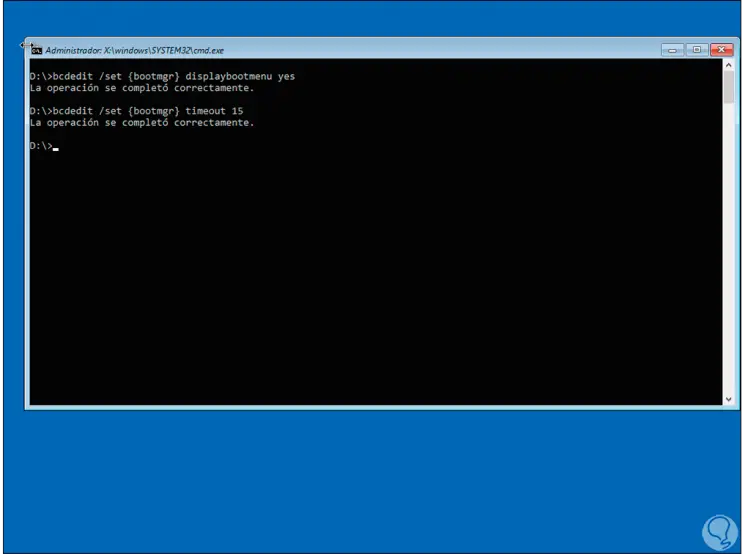
Step 9
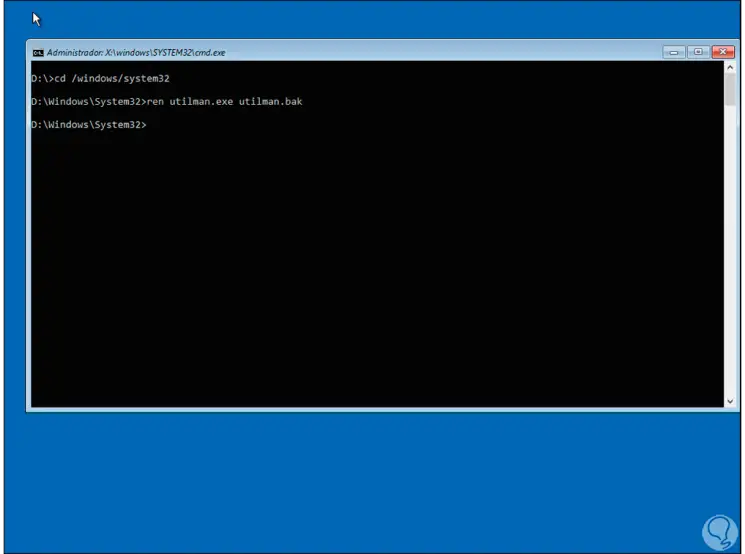
Now run "cd / windows / system32", there we are going to rename Utilman with the following command:
ren utilman.exe utilman.bak
Step 10
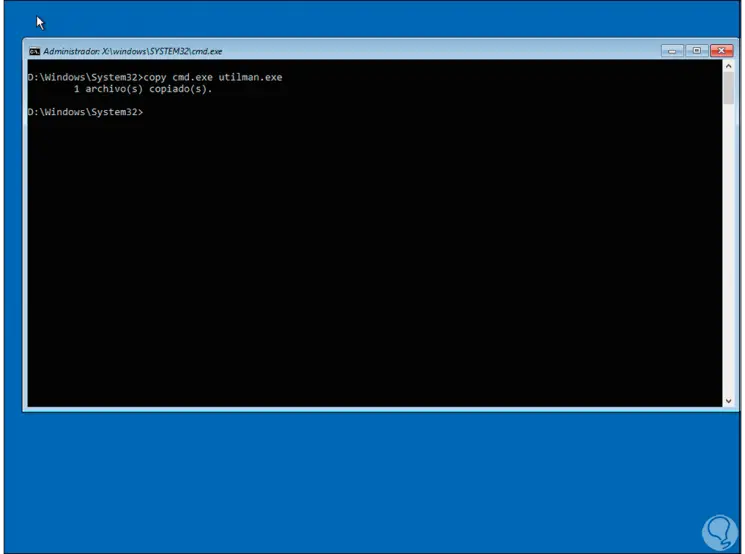
Now we are going to copy CMD to Utilman with the command:
copy cmd.exe utilman.exe
Step 11
What this does is allow the Utilman function (which is accessibility in Windows Server), to work as a CMD console to make changes to user profiles.
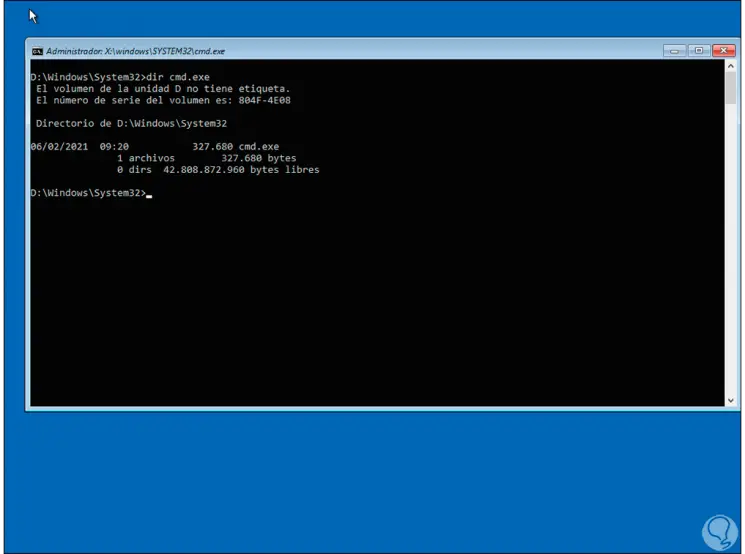
After this, we are going to list the content of CMD with the command:
dir cmd.exe
Step 12
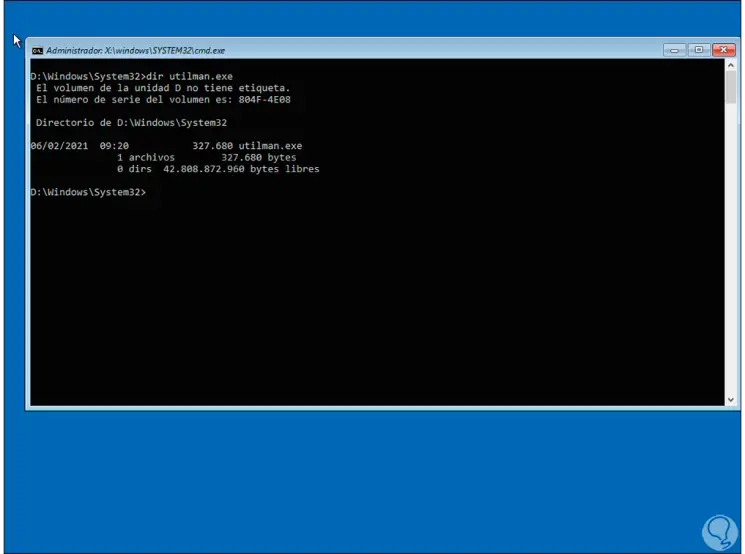
Now we list the contents of Utilman with the command:
dir utilman.exe
Step 13
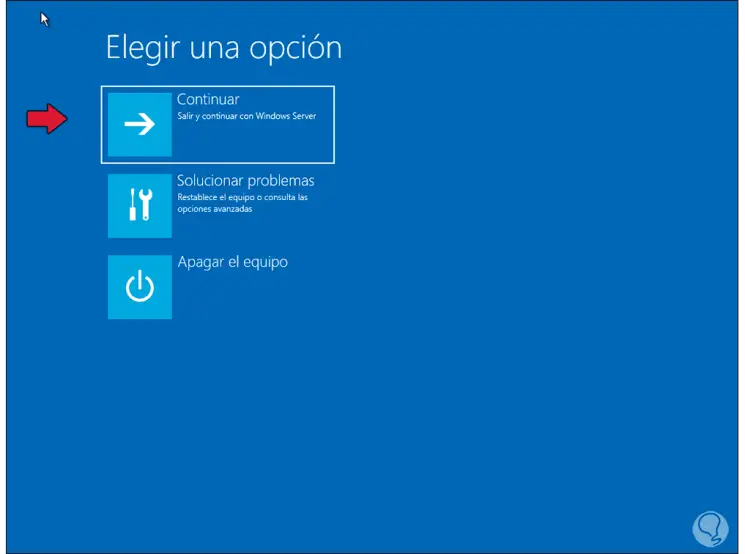
We exit the console with the "exit" command and then we will see the following window, there we click on "Continue":
Step 14
Windows Server 2022 and will start:
Step 15
We get to the lock screen:
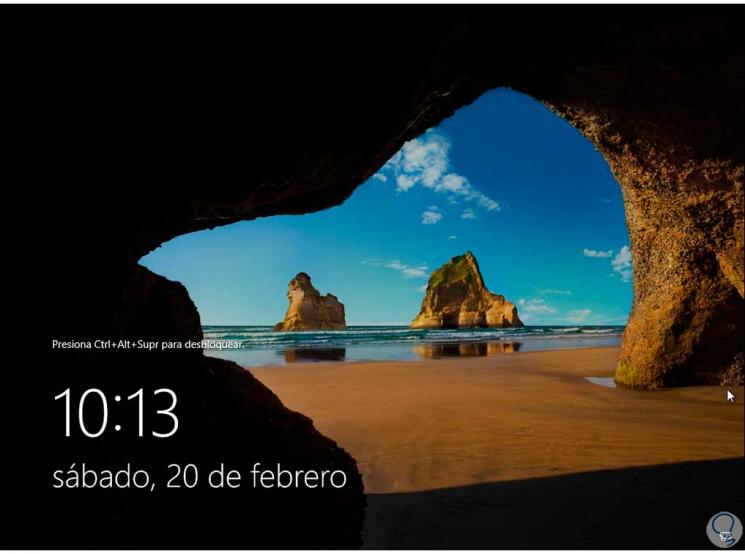
Step 16
We use the following keys to unlock and at the bottom we click on the accessibility icon:
Ctrl + Alt + Del
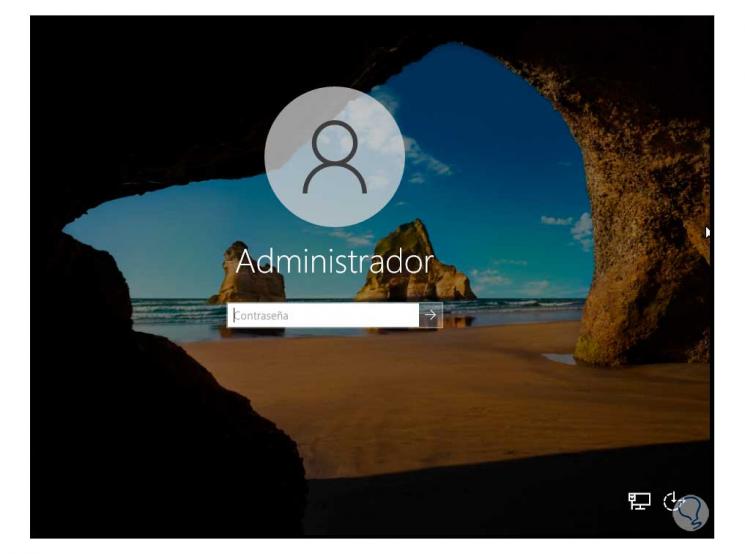
Step 17
Clicking there will open a CMD console, there we enable the Administrator user:
net user administrator / active: yes
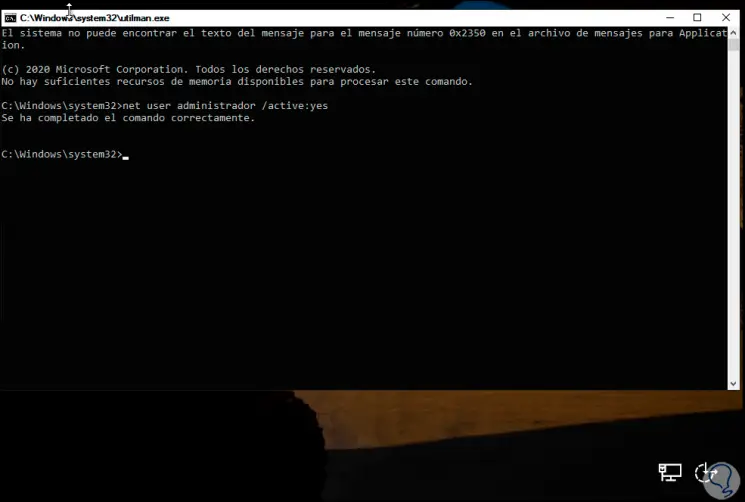
Step 18
After this we set the password with the syntax:
net user administrator "password"
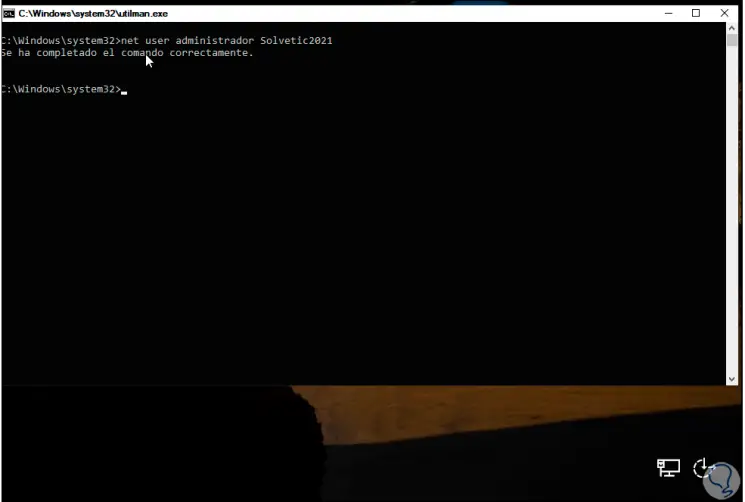
Step 19
We exit with "exit" and then we enter the password created to access Windows Server 2022:
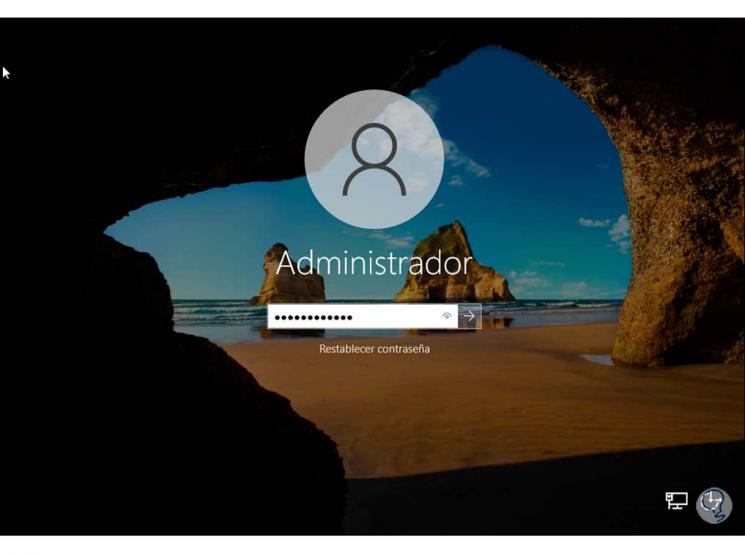
Step 20
We will have access to the system that is the objective:

With this process it is possible to reset the administrator password and have access to Windows Server 2022..