Safe browsing is something that seems remote due to the immense threats that we find the network both locally and externally and that at the slightest error on our part will act by damaging basic or delicate files and in more extreme cases completely the device. If we talk about mobile devices, specifically Android, the threats become even more abundant due to factors such as:
- Connection to public networks such as airports, cafes, libraries, etc.
- Auto Connectivity Settings
- Constant web browsing which can be redirected to malicious sites
- Receiving unwanted emails with malicious code that we can open easily and many more threats.
Although there are several ways we can protect ourselves on Android, TechnoWikis will focus on one of the simplest, safest and most powerful ways to improve all aspects of browsing security and it is using Tor..
What is Tor
Tor has developed as a group of servers whose main objective and mission is to improve and optimize privacy and security on the Internet. When we connect to the Tor network, we will be connecting through a series of virtual tunnels which avoids having to establish a direct connection which is, in many cases dangerous, in this way each Tor user can share their information through public networks without your privacy being at risk.
Tor has been designed as a tool to escape censorship, which allows all users to access content that is capped or blocked. Even so, TechnoWikis always recommends being responsible for the sites visited without violating any local or international law that may have any legal repercussion.
Another advantage of Tor, is that it can be used as a creation model for software developers in order to give rise to new communication tools that include new privacy policies. Tor's services allow users to post on pages and other services without having to display information on the original site location which is a form of advanced integrity and privacy..
In a connected world like the current one, there is something called traffic analysis which can be used, and is used every second, to check who is talking to who through a public network and in this way you can reach sensitive information such as Know the source and destination of this Internet traffic and thus track all behavior and interests which is subsequently sold to groups interested in this information. Now, to understand why traffic analysis has this impact we must understand how it works, all Internet data packages are composed of two parts:
- a header used for routing.
With the data load we refer to the data that is sent such as an email message, a web page, etc., and the worst part of this is that, even if the data load is encrypted , the traffic analysis is in the ability to access this content since this analysis focuses on the header, which reveals the source, destination, size, time and more details of the message sent.
If we choose to use Tor, we can reduce the risks of a traffic analysis since all transactions executed on the network will be launched from several places on the Internet, so that no point can link that message to a particular destination. All data packets in the Tor network make use of a random path in order to avoid detection of where the data comes from or where it is directed..
In order to create a private network with Tor , the user's software or client is incrementally built with a circuit of encrypted connections using relays in the network and no individual relay knows in detail the complete path that a data packet has taken just for prevent it from being violated and the information is revealed, then the client negotiates a separate set of encryption keys to ensure that each hop cannot track these connections.
What is the Dark web?
Now, with all the advancement of technologies, we find a new term at the network level called dark web (dark network) and this type of network is a portion of the Internet that has been intentionally hidden from traditional search engines , making use of masked and accessible IP addresses only through a special web browser.
When using a dark web you run the risk of being attacked by some kind of hacker and that is where Tor will be of great help along with Orbot proxy.
TechnoWikis will explain how to enter the dark web using Tor.
1. Install Tor browser in Andriod
This is in beta and is the only mobile browser compatible with Tor Project. For this beta version it will also be necessary to install Orbot, the lime is a proxy application that connects the Tor browser for Android with the Tor network.
features
Within the features of this browser we have:
- Avoid navigation surveillance
- Restrict the use of the fingerprint reader
Step 1
To start this process we must install the Tor browser through the following link in the Play Store:
Tor Browser
Step 2
When accessing the Play Store we will see the following. There we click on the "Install" button to carry out the installation of Tor on Android.
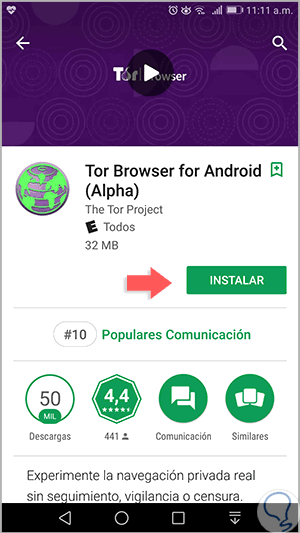
2. Install Orbot proxy on Android
features
Among its characteristics we find:
- Use of private applications
- It has a mode of use called universal
Step 1
Now we must install Orbot to ensure privacy and confidentiality of navigation, for this, Orbot offers three interfaces in the Tor network:
- SOCKS 4A / 5 proxy 127.0.0.1:9050
- HTTP proxy 127.0.0.1:8118
- Transparent proxying (only on some devices)
Step 2
Orbot is available for download at the following link:
Orbot Proxy
Step 3
There we click on the "Install" button to carry out the process.

3. Configure and use Tor with Orbot proxy on Android
Step 1
As soon as the two applications have been installed on Android, we will first run Orbot proxy and see the following:
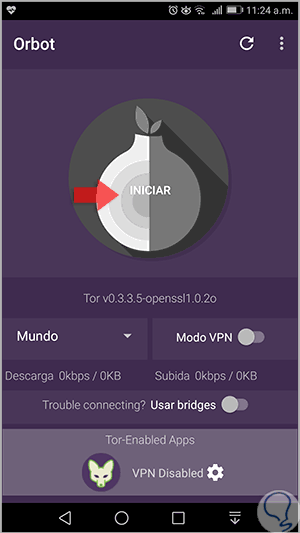
Step 2
There we click on the Start button and if we wish we can configure the VPN network in order to hide our real location on the network. We can see that the Orbot connection process begins:
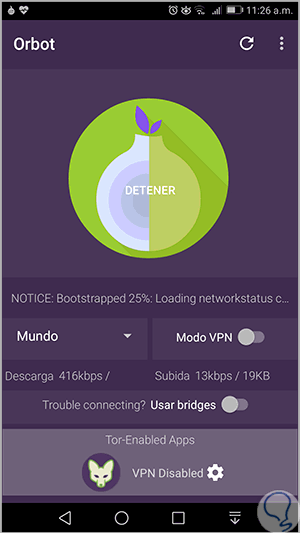
Step 3
We can verify that the connection has been successful when the onion icon turns green and the message Stop. Now that the network is secure, we can open the Tor browser and see this. There we have an introduction to the use of Tor and we can start browsing the web, here the only difference is that it will be possible to access pages, onion which belong to the TOR network, being one of the most popular of the Dark Web .

Thus we are accessing an anonymous but safe, strong and reliable navigation thanks to the integration of Tor with Orbot Proxy.